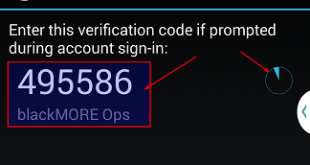
Two-step verification (also known as Two-factor authentication, abbreviated to TFA) …
Read More »
March 5, 2024
Whispers: A Powerful Static Code Analysis Tool for Credential Detection
“My little birds are everywhere, even in the North, they whisper to me the strangest stories.&…
March 5, 2024
Enabling AMD GPU for Hashcat on Kali Linux: A Quick Guide
If you’ve encountered an issue where Hashcat initially only recognizes your CPU and not the GP…
March 5, 2024
Identifying harmful activity on your captured traffic
This Python script utilises Wireshark or TCPdump to analyse network traffic stored in a specified .p…
May 20, 2023
Nyxt: Hacker’s Dream Browser
In the ever-evolving digital landscape, the demand for specialized tools and platforms has grown exp…
May 19, 2023
Migrate Plex Server – Ubuntu
To migrate your Plex server to a new Ubuntu server, you can follow these steps: 1. Set up the new Ub…
May 19, 2023
Boot Ubuntu Server 22.04 LTS from USB SSD on Raspberry Pi 4
This is a guide for configuring Raspberry Pi4 to boot Ubuntu from external USB SSD drive instead of …
April 26, 2023
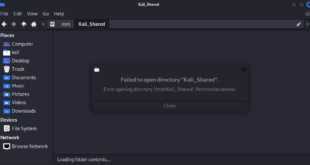
How to fix You can’t access this shared folder because your organization’s security policies block unauthenticated guest access error on Windows 11
If you have the following error on Windows 11 “You can’t access this shared folder becau…
June 11, 2022
Ubiquiti Dream Machine (UDM) – unable to connect to NBN
I don’t want the NBN ISP router running anymore and use Ubiquiti Dream Machine (UDM) instead. …
April 15, 2022
Quick Snap Cheat Sheet for Ubuntu
Snaps are app packages for desktop, cloud and IoT that are easy to install, secure, cross‐platform a…
February 11, 2022
Bypass 40X Response Codes with dontgo403
Bypass 40X Response Codes with dontgo403 …
Recent Posts
-
Securing SSH with two factor authentication using Google Authenticator
-
How to install the noip2 on Ubuntu and run via systemd systemctl (noIP Dynamic Update Client)
-
Connect to WiFi network from command line in Linux
-
How to use sar for monitoring your Linux system? sysstat sar examples and usage
-
Install AMD ATI proprietary driver (fglrx) in Kali Linux 1.0.6 running Kernel version 3.12.6
-
A very detailed guide on how to setup VPN on Kali Linux and Ubuntu
Every day millions of people uses different VPN service providers …
Read More » -
Advanced Persistent Threat Activity Exploiting Managed Service Providers
-
Advantages disadvantages of using Proxy vs VPN vs TOR vs TOR and VPN together.
-
Complete solution for online privacy with own private OpenSSH, OpenVPN and VNC server
-
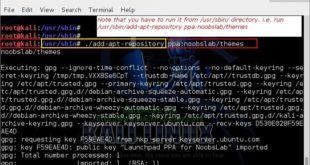
Kali Linux add PPA repository add-apt-repository
A Personal Package Archive (PPA) is a special software repository …
Read More » -
How to install/remove different KDE Desktop Environments in Kali Linux
-
Free DoS Attack Tools
-
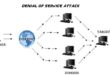
Denial-of-service Attack – DoS using hping3 with spoofed IP in Kali Linux
-
Identify USB Driver. Ubuntu, Debian, Mint, CentOS, Fedora & all Linux distro
This guide shows how you can identify USB Driver Chipset(most …
Read More » -
Automatically crack WiFi password with besside-ng
-
Generate WiFi IVS dump with makeivs-ng on Kali Linux
-
802.11 Recommended USB Wireless Cards for Kali Linux
-
Targeting websites with Password Reset Poisoning
Most of web application security vulnerabilities, leverage user input in …
Read More » -
Side-Channel Vulnerability Variants 3a and 4 – Spectre and Meltdown
-
How to Prevent DOM-based Cross-site Scripting
-
Denial of Service Attack Proof of Concept PHP Exploit for <=4.0 WordPress DoS Attack - CVE-2014-9034
-
Output your microphone to a remote computers speaker
Output your microphone to a remote computers speaker
Read More » -
SSH through host in the middle
-
Three different ways to duplicate installed packages in multiple machines in Linux
-
ssh to machine behind shared NAT
-
How to check Network Interface details in Linux
 blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….