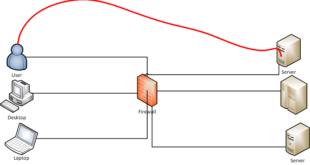
dontgo403 is a tool to bypass 40X errors.

Installation
git clone https://github.com/devploit/dontgo403; cd dontgo403; go get; go build
Customization
If you want to edit or add new bypasses, you can add it directly to the specific file in payloads folder and the tool will use it.
Options
./dontgo403 -h Command line application that automates different ways to bypass 40X codes. Usage: dontgo403 [flags] Flags: -b, --bypassIp string Try bypass tests with a specific IP address (or hostname). i.e.: 'X-Forwarded-For: 192.168.0.1' instead of 'X-Forwarded-For: 127.0.0.1' -H, --header strings Add a custom header to the requests (can be specified multiple times) -h, --help help for dontgo403 -p, --proxy string Proxy URL. For example: http://127.0.0.1:8080 -u, --uri string Target URL -a, --useragent string Set the User-Agent string (default 'dontgo403/0.3')
 blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….