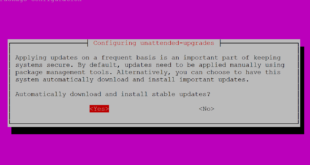
This guide explains how to configure automatic updates in Ubuntu Server 20.04. This tutorial is based on the following official Ubuntu Documentation article: Ubuntu Server Guide » Package Management » Automatic Updates. If you just want to do it, scroll down to the end and copy paste the two configuration …
Read More »Sophisticated Spearphishing Campaign Targets Government Organizations, IGOs, and NGOs
This Joint Cybersecurity Advisory uses the MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK®) framework, Version 9. See the ATT&CK for Enterprise for all referenced threat actor tactics and techniques. The Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) are engaged in addressing a spearphishing …
Read More »Exploit ACL Based Privilege Escalation Paths in Active Directory
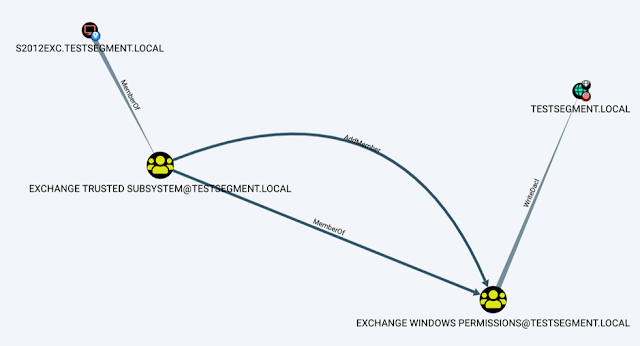
Aclpwn.py is a tool that interacts with BloodHound to identify and exploit ACL based privilege escalation paths. It takes a starting and ending point and will use Neo4j pathfinding algorithms to find the most efficient ACL based privilege escalation path.
Read More »SamSam Ransomware
The Department of Homeland Security (DHS) National Cybersecurity and Communications Integration Center (NCCIC) and the Federal Bureau of Investigation (FBI) are issuing this activity alert to inform computer network defenders about SamSam ransomware, also known as MSIL/Samas.A. Specifically, this product shares analysis of vulnerabilities that cyber actors exploited to deploy …
Read More »How to access Dark Web?
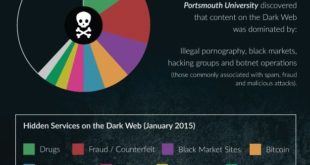
The concept of the Dark Web isn’t vastly different from the Surface Web. There are message boards (e.g. 8chan, nntpchan), places you can buy things (e.g. Alphabay, Hansa), and blogs (e.g. OnionNews, Deep Web Radio). The rules, or rather a lack thereof, is what makes the Dark Web unique. Anything …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….