Wesside-ng is an auto-magic tool which incorporates a number of techniques to seamlessly obtain a WEP key in minutes. It first identifies a network, then proceeds to associate with it, obtain PRGA (pseudo random generation algorithm) xor data, determine the network IP scheme, reinject ARP requests and finally determine the WEP key. All this is done without your intervention.
Crack a WEP key of an open network without user intervention
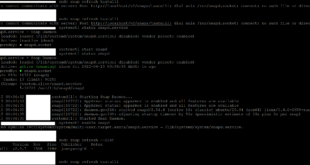
root@kali:~# wesside-ng -h Wesside-ng 1.2 rc4 - (C) 2007, 2008, 2009 Andrea Bittau http://www.aircrack-ng.org Usage: wesside-ng <options> Options: -h : This help screen -i <iface> : Interface to use (mandatory) -m <my ip> : My IP address -n <net ip> : Network IP address -a <mymac> : Source MAC Address -c : Do not crack the key -p <min prga> : Minimum bytes of PRGA to gather -v <victim mac> : Victim BSSID -t <threshold> : Cracking threshold -f <max chan> : Highest scanned chan (default: 11) -k <txnum> : Ignore acks and tx txnum times
wesside-ng Usage Example
Use the specified monitor mode interface (-i wlan0mon) and target a single BSSID (-v de:ad:be:ef:ca:fe).
root@kali:~# wesside-ng -i wlan0mon -v de:ad:be:ef:ca:fe [18:31:52] Using mac 3C:46:D8:4E:EF:AA [18:31:52] Looking for a victim... [18:32:13] Chan 04 -
Source:
Author: Thomas d’Otreppe, Original work: Christophe Devine
License: GPLv2
 blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….

That was so helpful. Thanks for sharing with us. I appreciated what you done.