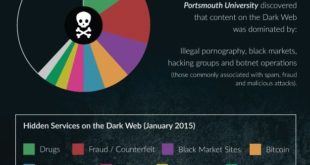
The concept of the Dark Web isn’t vastly different from the Surface Web. There are message boards (e.g. 8chan, nntpchan), places you can buy things (e.g. Alphabay, Hansa), and blogs (e.g. OnionNews, Deep Web Radio). The rules, or rather a lack thereof, is what makes the Dark Web unique. Anything …
Read More »Inception Attackers Target Europe with Year-old Office Vulnerability
The Inception attackers have been active since at least 2014 and have been documented previously by both Blue Coat and Symantec; historical attacks used custom malware for a variety of platforms, and targeting a range of industries, primarily in Russia, but also around the world. This blog describes attacks against …
Read More »Brute Force Attacks Conducted by Cyber Actors
In a traditional brute-force attack, a malicious actor attempts to gain unauthorized access to a single account by guessing the password. This can quickly result in a targeted account getting locked-out, as commonly used account-lockout policies allow three to five bad attempts during a set period of time. During a …
Read More »Avoiding Web Application Firewall using Python
Web application firewalls are usually placed in front of the web server to filter the malicious traffic coming towards server. If you arehired as a penetration tester for some company and they forgot to tell you that they are using web application firewall than you might get into a serious …
Read More »Targeting websites with Password Reset Poisoning
Most of web application security vulnerabilities, leverage user input in ways that were not initially intended by their developer(s). Password Reset Poisoning is one such vulnerability, that leverages commonly unthought of headers, such as the Host header seen in an HTTP request: GET https://example.com/reset.php?email=foo@bar.com HTTP/1.1 Host: evilhost.com Notice the difference …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….