Free Android Penetration Testing Toolkit & Risk Assessment
Read More »How to configure automatic updates in Ubuntu Server
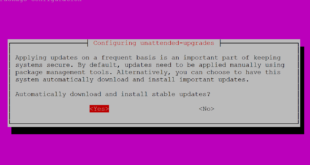
This guide explains how to configure automatic updates in Ubuntu Server 20.04. This tutorial is based on the following official Ubuntu Documentation article: Ubuntu Server Guide » Package Management » Automatic Updates. If you just want to do it, scroll down to the end and copy paste the two configuration …
Read More »Sophisticated Spearphishing Campaign Targets Government Organizations, IGOs, and NGOs
This Joint Cybersecurity Advisory uses the MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK®) framework, Version 9. See the ATT&CK for Enterprise for all referenced threat actor tactics and techniques. The Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) are engaged in addressing a spearphishing …
Read More »Vulnerable docker environment for learning to hack
Vulhub is an open-source collection of pre-built vulnerable docker environment for learning to hack. No pre-existing knowledge of docker is required, just execute two simple commands and you have a vulnerable environment.
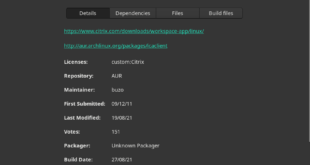
Read More »Install and Run Citrix Workspace on Linux
Citrix Workspace on Linux enables users to access virtual desktops and hosted applications delivered by XenDesktop and XenApp from devices running the Linux operating system. Workspace app for Linux is available in English, German, Spanish, French, Japanese, Dutch, Portuguese (Brazil), Simplified Chinese, Russian and Italian. It can be used: Thin …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….