Vulhub is an open-source collection of pre-built vulnerable docker environment for learning to hack. No pre-existing knowledge of docker is required, just execute two simple commands and you have a vulnerable environment.

Vulnerable docker environment for learning to hack
Vulhub contains many frameworks, databases, applications, programming languages and more such as:
- Drupal
- ffmpeg
- CouchDB
- ActiveMQ
- Glassfish
- Joombla
- JBoss
- Kibana
- Laravel
- Rails
- Python
- Tomcat
And many, many more.
Install docker/docker-compose
Install the docker/docker-compose on Ubuntu 20.04:
# Install pip curl -s https://bootstrap.pypa.io/get-pip.py | python3 # Install the latest version docker curl -s https://get.docker.com/ | sh # Run docker service systemctl start docker # Install docker compose pip install docker-compose
The installation steps of docker and docker-compose for other operating systems might be slightly different, please refer to the docker documentation for details.
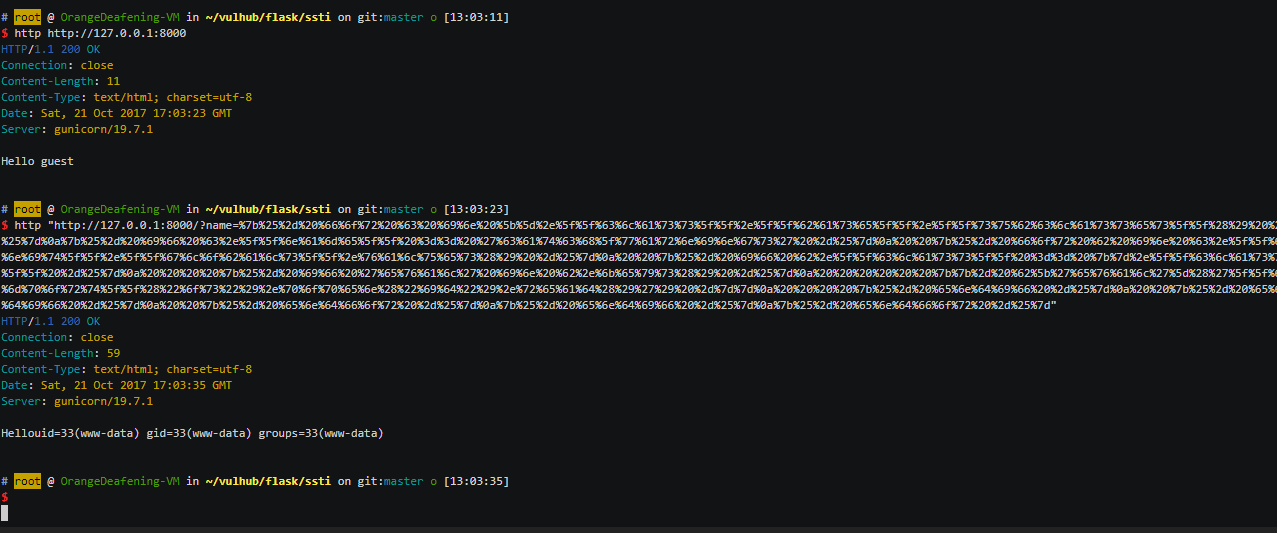
Usage
# Download project wget https://github.com/vulhub/vulhub/archive/master.zip -O vulhub-master.zip unzip vulhub-master.zip cd vulhub-master # Enter the directory of vulnerability/environment cd flask/ssti # Compile environment docker-compose build # Run environment docker-compose up -d
There is a README document in each environment directory, please read this file for vulnerability/environment testing and usage.
After the test, delete the environment with the following command.
docker-compose down -v
It is recommended to use a VPS of at least 1GB memory to build a vulnerability environment. The your-ip mentioned in the documentation refers to the IP address of your VPS. If you are using a virtual machine, it refers to your virtual machine IP, not the IP inside the docker container.
All environments in this project are for testing purposes only and should not be used as a production environment!
Notice
- To prevent permission errors, it is best to use the root user to execute the docker and docker-compose commands.
- Some docker images do not support running on ARM machines.
More here.
 blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….

