The Department of Homeland Security (DHS) National Cybersecurity and Communications Integration Center (NCCIC) and the Federal Bureau of Investigation (FBI) are issuing this activity alert to inform computer network defenders about SamSam ransomware, also known as MSIL/Samas.A. Specifically, this product shares analysis of vulnerabilities that cyber actors exploited to deploy …
Read More »New Exploits for Unsecure SAP Systems
A presentation at the April 2019 Operation for Community Development and Empowerment (OPCDE) cybersecurity conference describes SAP systems with unsecure configurations exposed to the internet. Typically, SAP systems are not intended to be exposed to the internet, as it is an untrusted network. Malicious cyber actors can attack and compromise these unsecure systems with publicly available exploit tools, termed “10KBLAZE.” The presentation detailed the new exploit tools and reports on systems exposed to the internet.
Read More »Microsoft Operating Systems BlueKeep Vulnerability
The Cybersecurity and Infrastructure Security Agency (CISA) is issuing this Activity Alert to provide information on a vulnerability, known as “BlueKeep,” that exists in the following Microsoft Windows Operating Systems (OSs), including both 32- and 64-bit versions, as well as all Service Pack versions:
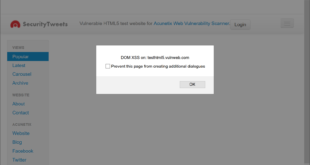
Read More »How to Prevent DOM-based Cross-site Scripting
There’s no denying the role that JavaScript has played in making web applications the sleek, interactive, online experiences that we know and love today. This powerful scripting language brought interactivity and animation to the web. But with great power comes great responsibility. Cross-site-scripting (XSS) remains a persistent stalwart among the …
Read More »Side-Channel Vulnerability Variants 3a and 4 – Spectre and Meltdown
On May 21, 2018, new variants of the side-channel central processing unit (CPU) hardware vulnerabilities known as Spectre and Meltdown were publicly disclosed. These variants—known as 3A and 4—can allow an attacker to obtain access to sensitive information on affected systems. Systems Affected CPU hardware implementations Description Common CPU hardware …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….