DHS and FBI recommend that all SOHO router owners power cycle (reboot) their devices to temporarily disrupt the malware. Network device management interfaces—such as Telnet, SSH, Winbox, and HTTP—should be turned off for wide-area network (WAN) interfaces, and, when enabled, secured with strong passwords and encryption. Network devices should be upgraded …
Read More »Identify website technologies with WhatWeb
WhatWeb identifies websites. Its goal is to answer the question, “What is that Website?”. WhatWeb recognises web technologies including content management systems (CMS), blogging platforms, statistic/analytics packages, JavaScript libraries, web servers, and embedded devices. WhatWeb has over 1700 plugins, each to recognise something different. WhatWeb also identifies version numbers, email …
Read More »Setting up Damn Vulnerable Web Application (DVWA) – Pentesting Lab
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is damn vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, help web developers better understand the processes of securing web applications and aid teachers/students to …
Read More »CYBERFORCE Profile Series: Transforming Technical Conversations with a Best Practice Assessment
This is the first in a series of blogs featuring a Palo Alto Networks CYBERFORCE Engineer and the business challenges they tackle. CYBERFORCE recognizes the best-of-the-best from the NextWave Partner Community; proven partner engineers who put the customer first, are trusted for their security expertise, and focus on preventing successful …
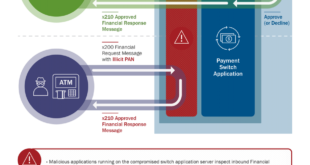
Read More »HIDDEN COBRA – FASTCash Campaign targeting banks
Since at least late 2016, HIDDEN COBRA actors have used FASTCash tactics to target banks in Africa and Asia. At the time of this TA’s publication, the U.S. Government has not confirmed any FASTCash incidents affecting institutions within the United States. FASTCash schemes remotely compromise payment switch application servers within …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….