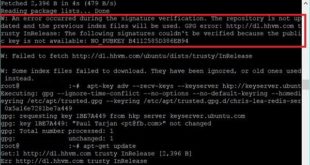
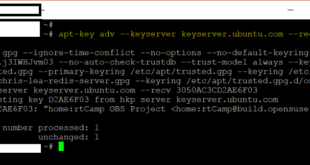
I was trying to update one of my server that has some HHVM repositories and received this error “W: An error occurred during the signature verification. The repository is not updated and the previous index files will be used. GPG error: http://dl.hhvm.com trusty InRelease: The following signatures couldn’t be verified …
Read More »Fixing W: GPG error: http://download.opensuse.org Release: The following signatures were invalid: KEYEXPIRED 1501595774 error
I was trying to update one of my server that has some Opensuse repositories and received this error “W: GPG error: http://download.opensuse.org Release: The following signatures were invalid: KEYEXPIRED 1501595774” root@someserver:~# apt-get update . . . ---SNIP---- Ign http://download.opensuse.org Translation-en Fetched 481 B in 4s (97 B/s) Reading package lists... …
Read More »Top 30 SSH shenanigans
Secure Shell (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. The best known example application is for remote login to computer systems by users. SSH provides a secure channel over an unsecured network in a client-server architecture, connecting an SSH client application with …
Read More »Disable touchscreen in Linux
I have a Dell Inspiron 5547, massive laptop with 16GB RAM and Intel i7. It also got a touchscreen. I don’t like touchscreens on laptops and I can’t remember ever using it. I usually plugin my laptop, Desktop and RaspberryPi 2 to an IOGear 4port KVM switch and use a …
Read More »Add timestamp to history command output in Linux
My last post was about adding timestamp to terminal in Linux. But isn’t it better to simply add timestamp to history command? This enables you to open your terminal anytime, run history command and find out when you ran which command, all without keeping terminal or putty windows open indefinitely. …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….