Fixing missing modules
If a module is shown as missing , then we need to install it. In my case, everything is installed. Most likely, since you are also using XAMPP, everything would be installed. However, if that is not the case, then you have to figure out how to install the modules. If you aren’t using XAMPP and did everything manually, then apt-get would be the way to go. Otherwise look at XAMPP’s (or whichever bundle you are using) documentation.
Fixing File Ownership
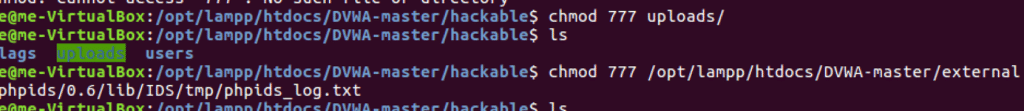
We need to give www-data user write access to two directories. We’ll can use chgrp and chmod commands in unison to give only the privileges that are needed, or we could go the lazy way and use chmod 777 (full read, write and execute privileges to everyone). I’m feeling lazy and I’m just gonna go the chmod way. Run the command below-
chmod 777 <directory> Replace directory with the correct directory.
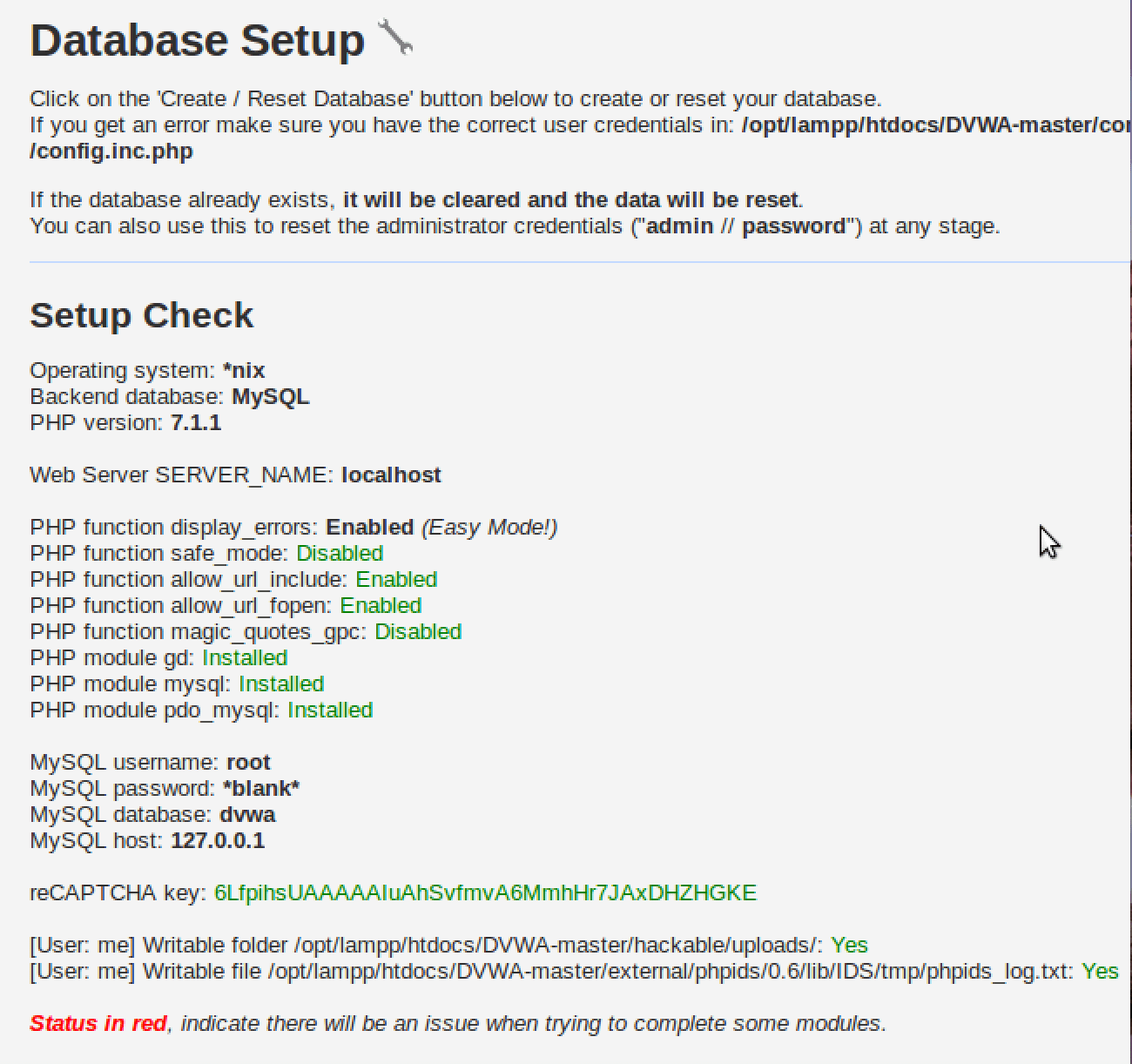
This is the last thing that needs to be done
Everything is green finally! Also, notice the credentials, we’ll need it later.
“admin // password”
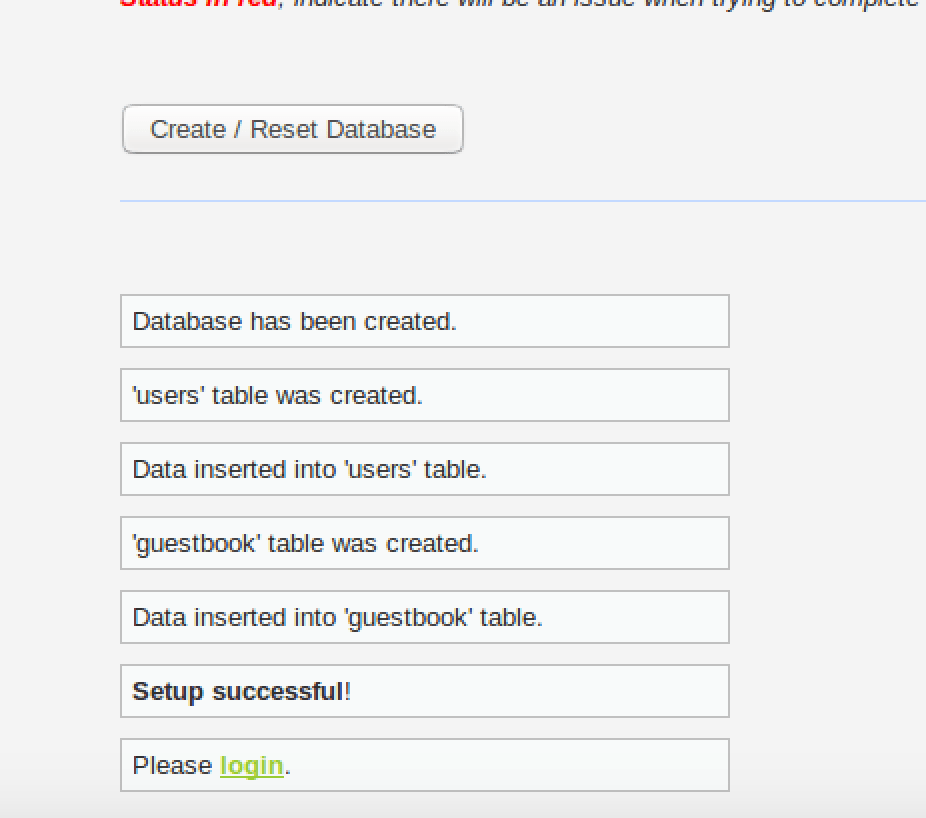
Database created. Populated with tables.
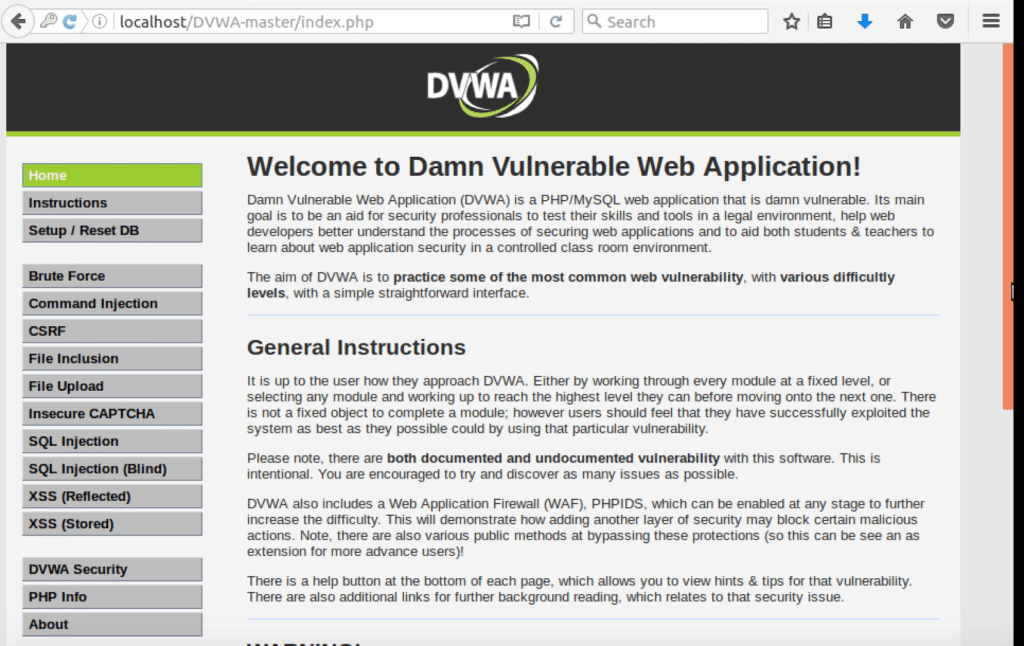
Finally the damn vulnerable application is running.
The username = “admin” and password is “password” (“admin // password” that we saw three pics ago).
Everything is running perfectly. This is the page you should see after successful login.
 blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….