Fixing problems
If you remember from previous post, we reached this point-
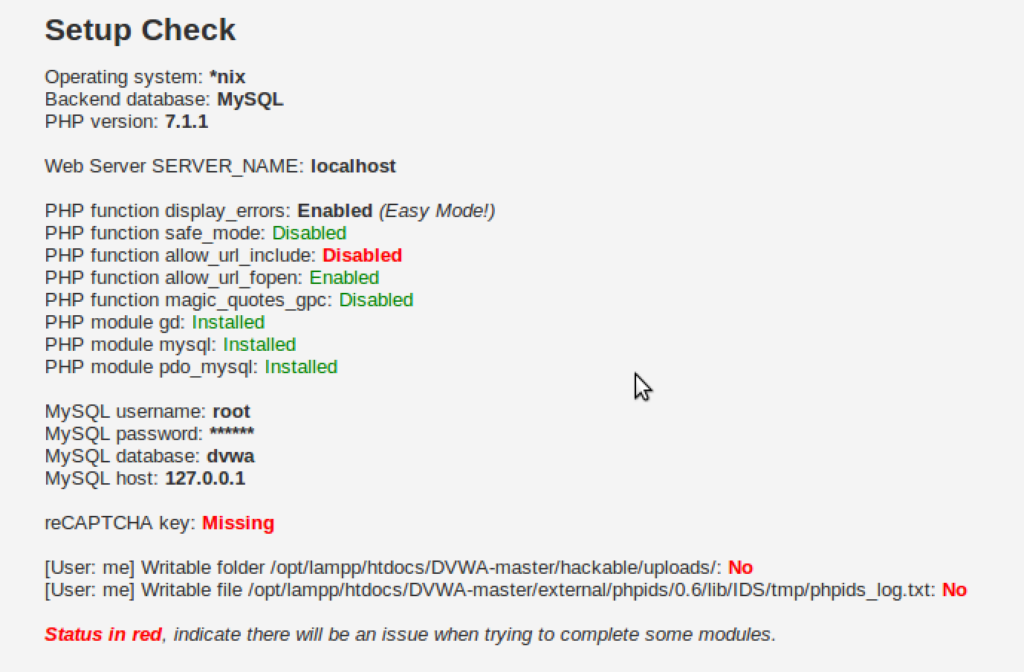
There’s some stuff in red color.
All the stuff in red needs fixing. If you are lucky, we have the same set of issues which need fixing. Otherwise, you’ll have to do some googling to find out how to fix problems which you are facing and I am not.
Changing mysql username and password
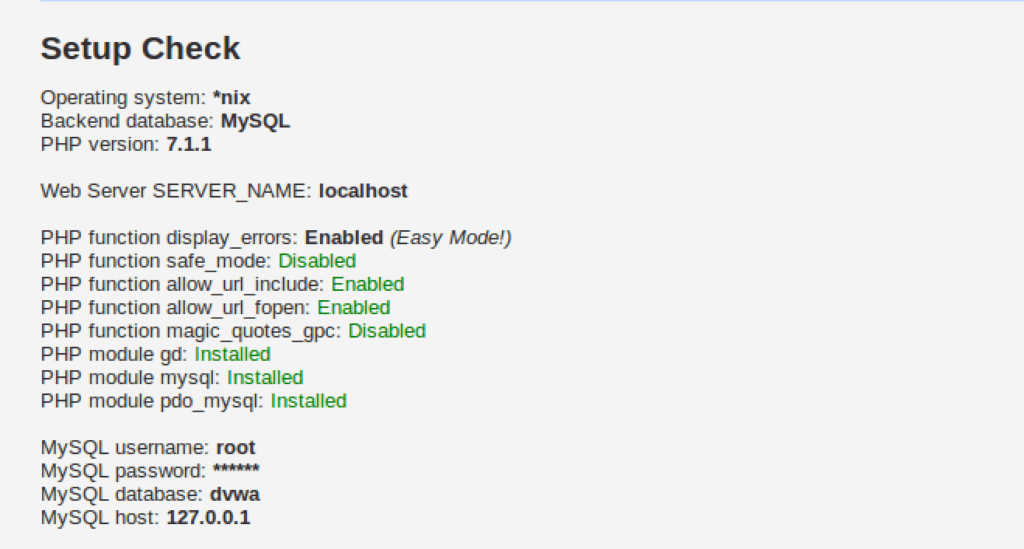
The default credentials are ‘root’ and ‘p@ssw0rd’ in the config.inc.php file. We change it to the correct mysql login credentials, ‘root’ and ”, in my case. You can change depending on your mysql credentials. This gets rid of our biggest worry – Unable to connect to database!
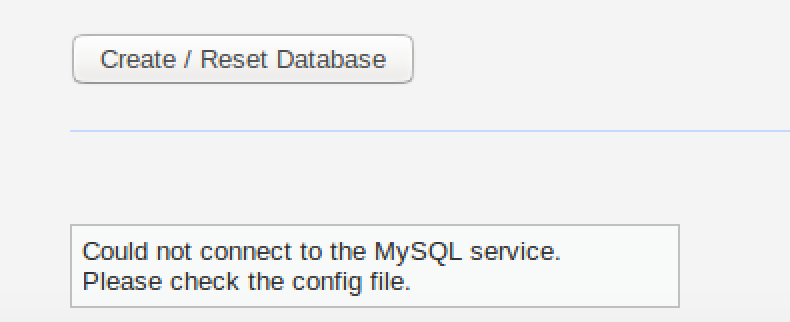
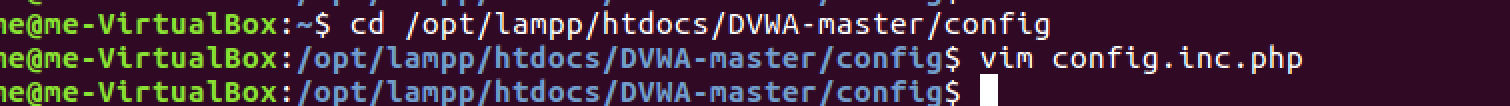
This is the biggest problem. Solving this means we can create our database, some modules may not work perfectly, but DVWA will run. Without fixing this, we won’t even be able to start. To fix this, open /opt/lamp/htdocs/DVWA-master/config/config.inc.php file in your favorite text editor.
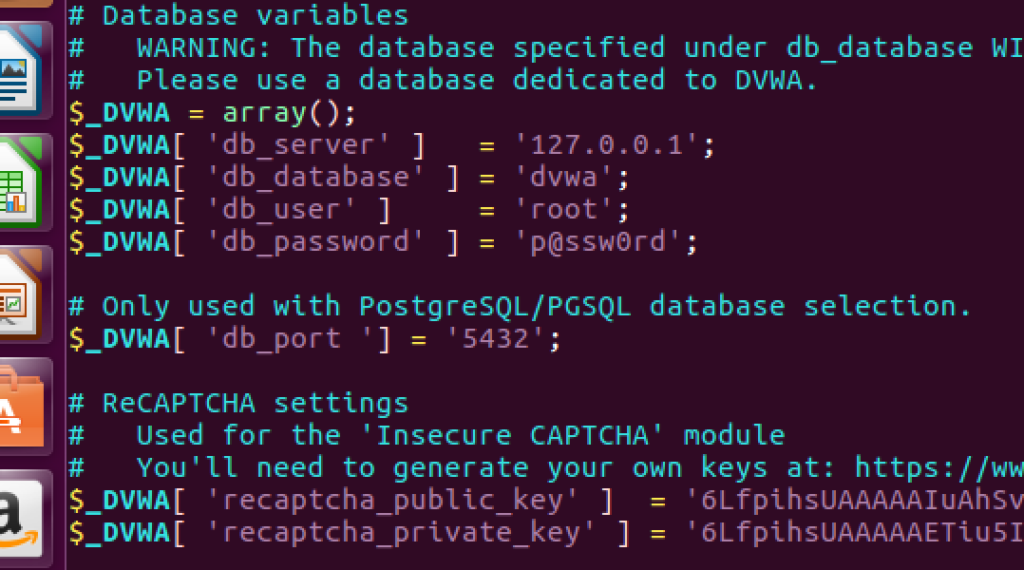
This password isn’t the password of our mysql database. In my case, password is nothing, i.e. two single quotes (i.e. ”). Update the value here. In case your mysql password is something else, use that. Change the username too is need be.

This is the corrected password value in my case. After this, refresh the page and click “Create/Reset database”
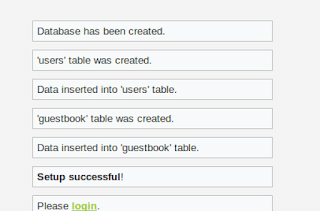
Now everything works fine after you click Create/Reset database. We’ll fix the other remaining issues in next section.
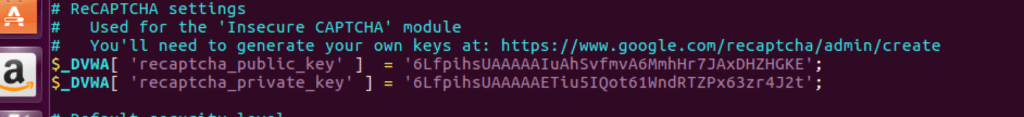
Fixing missing recaptcha key
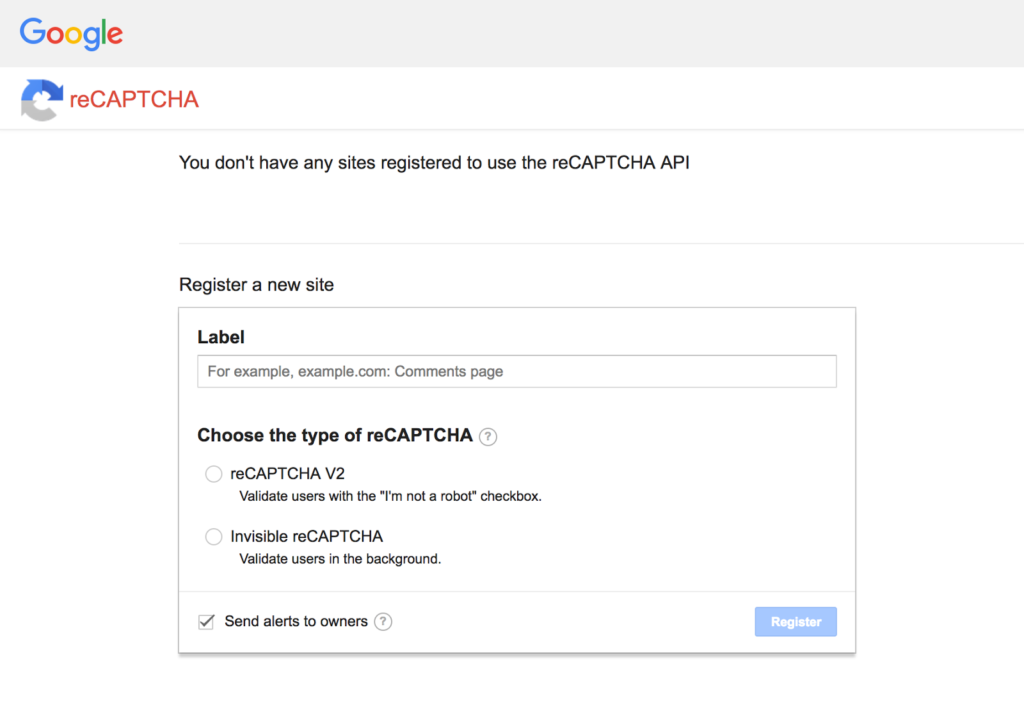
First, we need to solve the recaptcha key missing problem. Go to this URL–
Go to the URL, you’ll see a form like this.
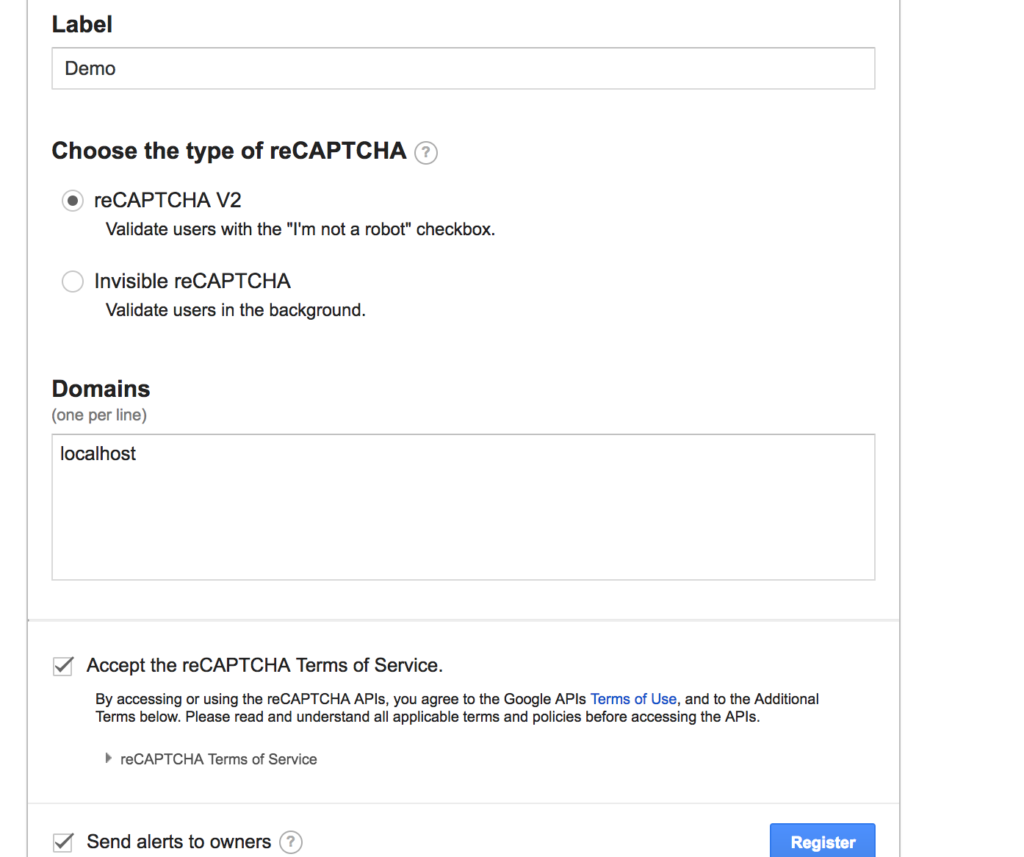
Fill form, values don’t matter much
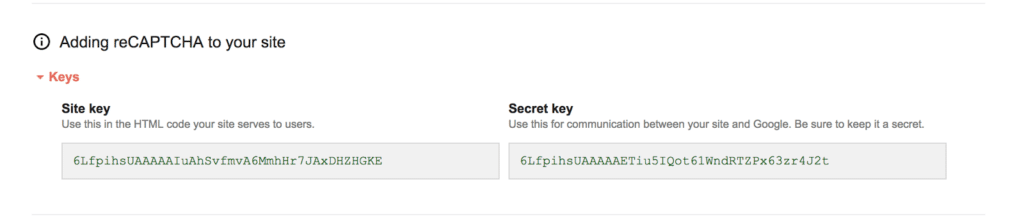
You obtain site key and secret key. Site key = Private key, secret key = private key
Open the config.ini.php file in your favourite text editor
Edit the recaptcha public key and private key fields. Here is what I did.
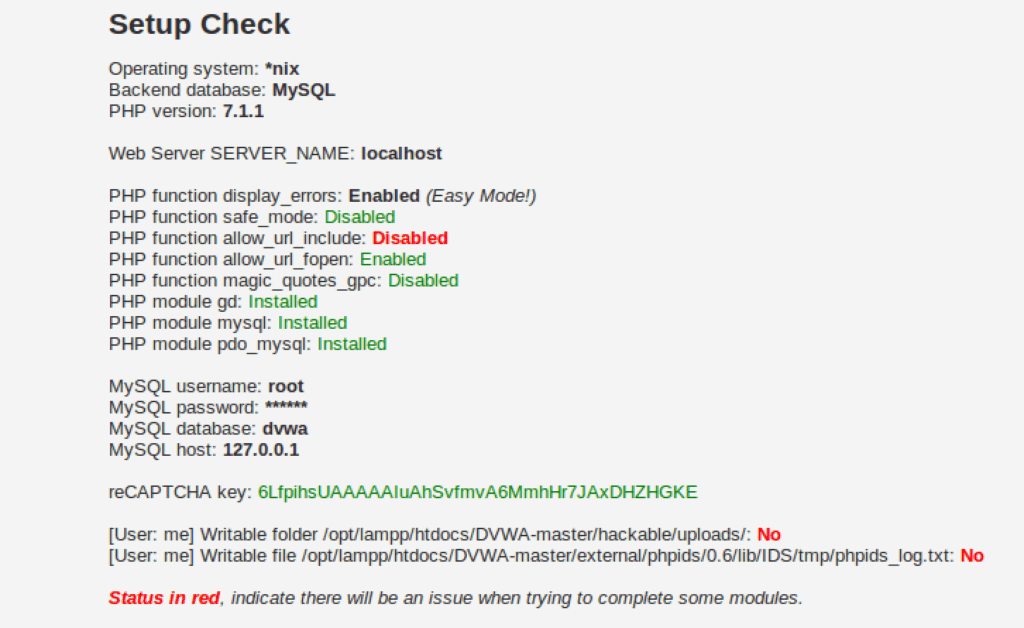
Now we have a a recaptcha key. One red down, 3 to go.
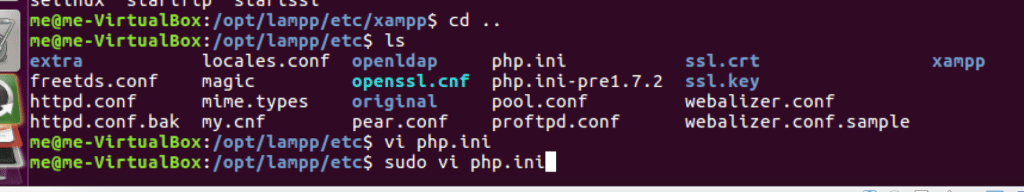
Fixing disabled allow_url_include
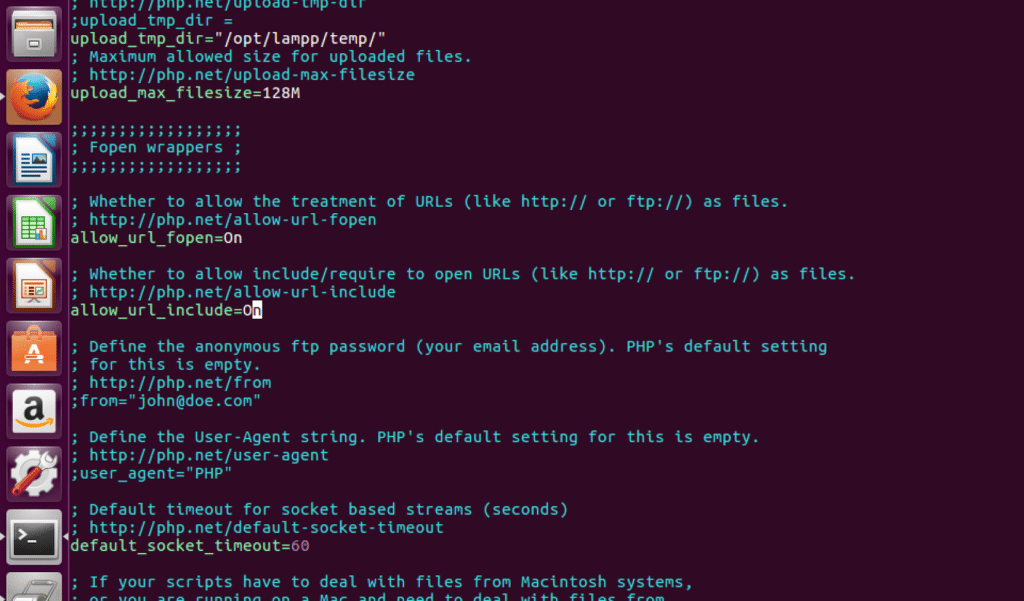
We simply have to locate the configuration file and edit the value of the parameter from Off to On.
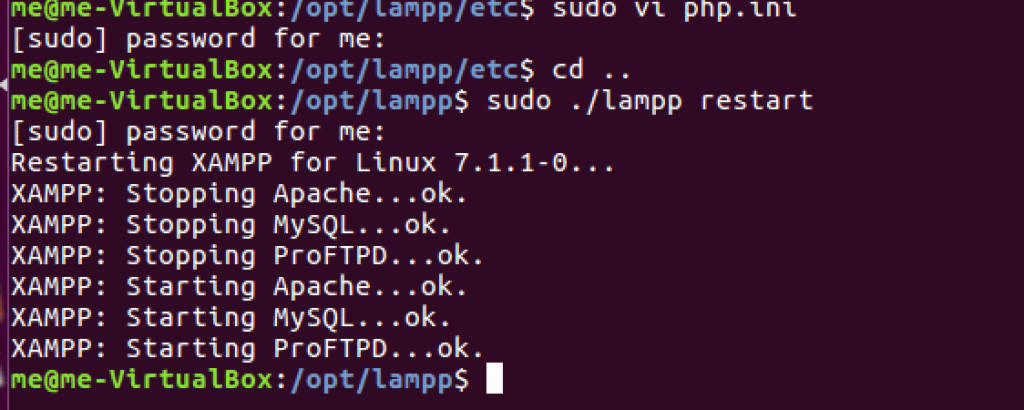
The php configuration file is located at /opt/lampp/etc/php.ini. Edit it with your favourite text editor, you’ll need root privileges (sudo)
Locate the allow_url_include line by using search feature of your text editor
Change Off to On.
Restart the lampp service
Reload page, you’ll see that the issue is fixed
Note: Any other function which is disabled can be enabled in a similar manner. All settings are in the php.ini file. You just need to search for the corresponding line and edit it.
 blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….