Remote Access Trojan: JBiFrost First observed in May 2015, the JBiFrost RAT is a variant of the Adwind RAT, with roots stretching back to the Frutas RAT from 2012. A RAT is a program that, once installed on a victim’s machine, allows remote administrative control. In a malicious context, it …
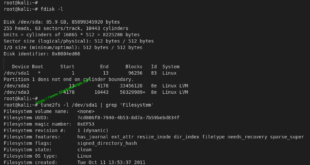
Read More »Find exact installation date of Linux
Ran into an interesting question today while trying to debug a problem with a monitoring tool, what was the exact installation date of Linux system on this server? I mean this is something you don’t try to find everyday and for a second I was like … yeah… i don’t …
Read More »Catching bad guys
Ever wondered how the good guys catch bad guys? I meant to say, what’s the process of catching bad guys who create virus, malware, crypto-lockers? It’s sort of a grey area and mostly not discussed very openly about the different methodologies used for Catching bad guys who create and distribute …
Read More »PuTTY alternatives
PuTTY is the most popular SSH client for Windows based systems. In fact it’s so popular that people actually install it in Linux (apt-get install putty)I. PuTTY is easy to use and you can save a lot of preferences. However, is PuTTY is best? To be honest, I think not. …
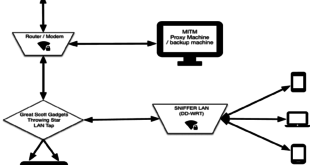
Read More »Create MITM Test Environment using Snifflab
Snifflab is a technical test environment for capturing and decrypting WiFi data transmissions. Snifflab creates a WiFi hotspot that is continually collecting all the packets sent over it. All connected clients’ HTTPS communications are subjected to a “Man-in-the-middle” attack, whereby they can later be decrypted for analysis. This article presents …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….