For years, experts have warned about the risks of relying on weak passwords to restrict access to data, and this is still a problem. A rule of thumb for passwords is the longer, the better. In this guide I will use FTP as a target service and will show how …
Read More »Man in the Middle Attack using Kali Linux – MITM attack
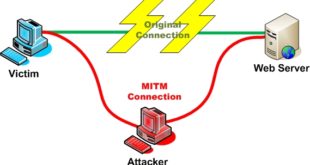
The man-in-the-middle attack (often abbreviated MITM, MitM, MIM, MiM, MITMA) in cryptography and computer security is a form of active eavesdropping in which the attacker makes independent connections with the victims and relays messages between them, making them believe that they are talking directly to each other over a private …
Read More »5 ways to change GRUB background in Kali Linux
This is a simple guide on how to change GRUB background in Kali Linux (i.e. it’s actually Kali Linux GRUB splash image). Kali dev team did few things that seems almost too much work, so in this article I will explain one of two things about GRUB and somewhat make …
Read More »Changing GRUB timeout in Kali Linux
I use Kali Linux alongside my Windows in my Laptop (yes I do use Windows and No thanks for the incoming sarcasms)! So when I start my Laptop, I get Kali Linux, Windows and Linux Mint as the 3 options. Kali Linux being the GRUB 1st choice it counts down …
Read More »Install Angry IP Scanner on Kali Linux
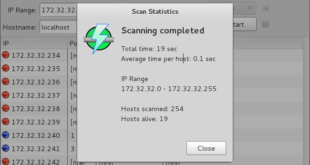
Angry IP Scanner (or simply ipscan) is an open-source and cross-platform network scanner designed to be fast and simple to use. It is a very fast IP address and port scanner. It can scan IP addresses in any range as well as any their ports. It is cross-platform and lightweight. …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….