The man-in-the-middle attack (often abbreviated MITM, MitM, MIM, MiM, MITMA) in cryptography and computer security is a form of active eavesdropping in which the attacker makes independent connections with the victims and relays messages between them, making them believe that they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. The attacker must be able to intercept all messages going between the two victims and inject new ones, which is straightforward in many circumstances (for example, an attacker within reception range of an unencrypted Wi-Fi wireless access point, can insert himself as a man-in-the-middle).
A man-in-the-middle attack can succeed only when the attacker can impersonate each endpoint to the satisfaction of the other—it is an attack on mutual authentication (or lack thereof). Most cryptographic protocols include some form of endpoint authentication specifically to prevent MITM attacks. For example, SSL can authenticate one or both parties using a mutually trusted certification authority.
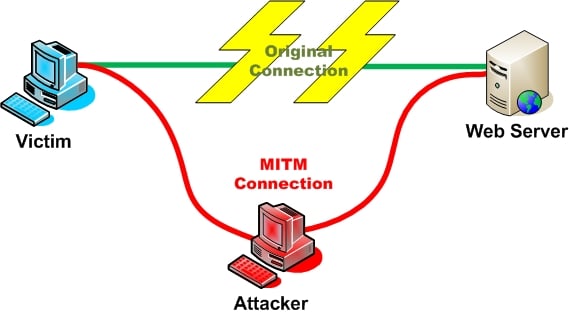
Scenario:
This is the simple scenario, and I try to draw it in a picture.
Kali Linux Man in the Middle Attack
- Victim IP address : 192.168.8.90
- Attacker network interface : eth0; with IP address : 192.168.8.93
- Router IP address : 192.168.8.8
Requirements:
- Arpspoof
- Driftnet
- Urlsnarf
Following steps show how to perform Man in the Middle Attack using Kali Linux and a target machine.
Open your terminal (CTRL + ALT + T kali shortcut) and configure our Kali Linux machine to allow packet forwarding, because act as man in the middle attacker, Kali Linux must act as router between “real router” and the victim.
You can change your terminal interface to make the view much more friendly and easy to monitor by splitting kali terminal window.
The next step is setting up arpspoof between victim and router.
arpspoof -i eth0 -t 192.168.8.90 192.168.8.8
Kali Linux Man in the Middle Attack
- And then setting up arpspoof from to capture all packet from router to victim.
arpspoof -i eth0 -t 192.168.8.8 192.168.8.90
Kali Linux Man in the Middle Attack
After step three and four, now all the packet sent or received by victim should be going through attacker machine.
Use DriftNet to Monitor packets and images
Inspired by EtherPEG (though, not owning an Apple Macintosh, I’ve never actually seen it in operation), DriftNet is a program which listens to network traffic and picks out images from TCP streams it observes. Fun to run on a host which sees lots of web traffic.
In an experimental enhancement, DriftNet now picks out MPEG audio streams from network traffic and tries to play them.
Now we can try to use DriftNet to monitor all victim image traffic. According to its website……
Use the following command to run DriftNet
driftnet -i eth0
When victim browse a website with image, DriftNet will capture all image traffic as shown in the screen-shot below.
Use URLSnarf to Monitor packets
URLSnarf is a tool that can sniff HTTP requests in Common Log Format. URLSnarf outputs all requested URLs sniffed from HTTP traffic in CLF (Common Log Format, used by almost all web servers), suitable for offline post-processing with your favorite web log analysis tool (analog, wwwstat, etc.).
urlsnarf -i eth0
and URLSnarf will start capturing all website address visited by victim machine.
When victim browse a website, attacker will know the address victim visited.
Defenses against the attack
Various defenses against MITM attacks use authentication techniques that include:
- DNSSEC Secure DNS extensions
- Strong encryption (as opposed to relying on small symmetric or asymmetric key sizes, broken ciphers or unproven ciphers)
- Public key infrastructures
- PKI mutual authentication The main defence in a PKI scenario is mutual authentication. In this case as well as the application validating the user (not much use if the application is rogue)—the users devices validates the application—hence distinguishing rogue applications from genuine applications
- A recorded media attestment (assuming that the user’s identity can be recognized from the recording), which can either be:
- A verbal communication of a shared value for each session (as in ZRTP)
- An audio/visual communication of the public key hash (which can be easily distributed via PKI)
- Stronger mutual authentication, such as:
- Secret keys (which are usually high information entropy secrets, and thus more secure), or
- Passwords (which are usually low information entropy secrets, and thus less secure)
- Latency examination, such as with long cryptographic hash function calculations that lead into tens of seconds; if both parties take 20 seconds normally, and the calculation takes 60 seconds to reach each party, this can indicate a third party
- Second (secure) channel verification
- Carry-forward verification
- Testing is being carried out on deleting compromised certificates from issuing authorities on the actual computers and compromised certificates are being exported to sandbox area before removal for analysis
The integrity of public keys must generally be assured in some manner, but need not be secret. Passwords and shared secret keys have the additional secrecy requirement. Public keys can be verified by a certificate authority, whose public key is distributed through a secure channel (for example, with a web browser or OS installation). Public keys can also be verified by a web of trust that distributes public keys through a secure channel (for example by face-to-face meetings).
Forensic analysis of MITM attacks
Captured network traffic from what is suspected to be a MITM attack can be analyzed in order to determine if it really was a MITM attack or not. Important evidence to analyze when doing network forensics of a suspected SSL MITM attack include:
- IP address of the server
- DNS name of the server
- X.509 certificate of the server
- Is the certificate self signed?
- Is the certificate signed by a trusted CA?
- Has the certificate been revoked?
- Has the certificate been changed recently?
- Do other clients, elsewhere on the Internet, also get the same certificate?
Conclusion
- To change or spoof the attacker MAC address, you can view the tutorial about how to change Kali Linux MAC address.
- Driftnet or Urlsnarf was hard to detect, but you can try to find the device in your network with promiscuous mode which have possibility to sniff the network traffic.
Hope you found it useful.
 blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….


all always thanks for share !!!!
&&
good Christmas and new year holidays
http://postimg.org/image/n96dgnfyr/full/
Hi zimmy,
Thank you. Merry Christmas and Happy New year Holidays to you too. Cheers,
-BMO
There is a -t missing in the second code area before the first ip.
Corrected, thank you.
You could add:
echo 1 > /proc/sys/net/ipv4/ip_forward
when you talk about “configure our Kali Linux machine to allow packet forwarding”
Hi! Can you do a tutorial bgp hijacking?
for even more fun set up an open wifi connection with a friendly name at a busy spot and capture the traffic there
and since most people just blindly click ok, you’ll get a bunch of email/social media/… usernames and passwords, credit card numbers and all sorts of abusable goodies just waiting to be monetized (and no, I wont say how, if you want to steal figure it out on your own :) )
Hey can anyone explain a good method for getting a computers public ip address while connected to the same site or game server, chat, or website ? Is there a way to sort conversation end points to determine who belongs to what address based off bytes in/out? I know it is basic stuff but im still learning so any help is appreciated.
are there any measures i need to take to make myself untraceble first?