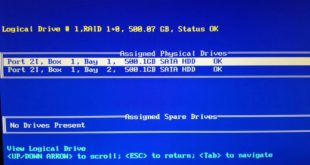
When the HP Proliant DL380 G7 boots up the only displayed BIOS options are F9 for Setup, F11 for the boot disk menu, but neither other these take you to the RAID setup. To get to the RAID setup options, when the screen appears showing the F9 and F11 options …
Read More »Change IP address in packet capture file (faking IP)
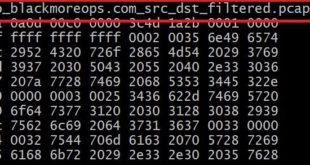
I'm sure you bumped into situations where you needed to fake IP address in a capture file. This maybe required when you're trying to send the capture file to someone that you don't really share your real IP's with or you just want to change cause you can. If you've tried this and looked around the interwebs, you'd surely know that there's not many guides available and most people would just tell casually "just use sed" or use "WireEdit" and pay some fees for their license. Now, both works but I just got pissed off in a particular situation where sed wasn't an options (the file was literally few GB's in size and most text editors would just freeze) and to make things worse, I needed to filter a lot of info and only keep source and destination IP addresses in there for privacy's sake. Yeah, that means removing all those noises like DNS, UDP, Broadcast, Cisco ARP, Broadcast, MDNS (yes, that too), SSDP ... yes, pretty much anything except TCP/UDP, HTTP and TLS trarffic between my server and the destination server. So, in summary I had to filter all of these noises and change IP address in packet capture file to hide source IP address, this is similar to faking IP address in packet captures. You can also use other tools to do it on the fly but they require more setup and all I just wanted to do is to hide my source IP.
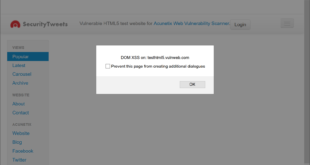
Read More »How to Prevent DOM-based Cross-site Scripting
There’s no denying the role that JavaScript has played in making web applications the sleek, interactive, online experiences that we know and love today. This powerful scripting language brought interactivity and animation to the web. But with great power comes great responsibility. Cross-site-scripting (XSS) remains a persistent stalwart among the …
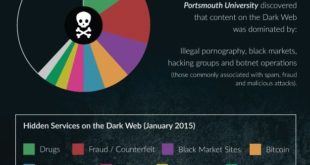
Read More »How to access Dark Web?
The concept of the Dark Web isn’t vastly different from the Surface Web. There are message boards (e.g. 8chan, nntpchan), places you can buy things (e.g. Alphabay, Hansa), and blogs (e.g. OnionNews, Deep Web Radio). The rules, or rather a lack thereof, is what makes the Dark Web unique. Anything …
Read More »Inception Attackers Target Europe with Year-old Office Vulnerability
The Inception attackers have been active since at least 2014 and have been documented previously by both Blue Coat and Symantec; historical attacks used custom malware for a variety of platforms, and targeting a range of industries, primarily in Russia, but also around the world. This blog describes attacks against …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….