RDPY is a Microsoft RDP Security Tool developed in pure Python with RDP Man in the Middle proxy support. This allows a user to record sessions and develop honeypot functionality. It supports both Microsoft RDP (Remote Desktop Protocol) protocol client and server side. RDPY supports standard RDP security layer, RDP …
Read More »WPSeku – WordPress Security Scanner
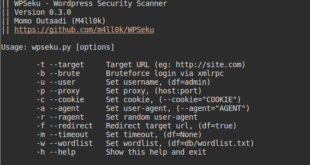
WPSeku is a black box WordPress vulnerability scanner that can be used to scan remote WordPress installations to find security issues. Features of WPSeku WordPress Security Scanner WPSeku supports various types of scanning including: Testing for XSS Vulnerabilities Testing for SQL Injection Vulnerabilities Testing for LFI Vulnerabilities Bruteforce login via …
Read More »Gain root access in macOS High Sierra #iamroot
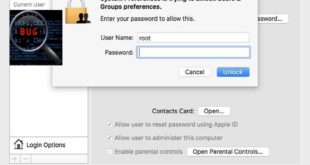
It’s a rather embarrassing a bug that was discovered by developer Lemi Ergin that allows anyone to gain root access in macOS High Sierra with a blank password. Yes, all you need to do is just press enter enough times and you’re root. In fact everyone now using #iamroot just to …
Read More »Buffer overflow attack in Kali Linux
This is a great video made by Assistant Professor Dr Mike Pound on how to make yourself root user on a computer using a buffer overflow attack in Kali Linux. Assistant Professor Dr Mike Pound details how it’s done in the following video:
Read More »dns2proxy – Offensive DNS server post-explotation tool – DNS spoofing, phishing and pharming
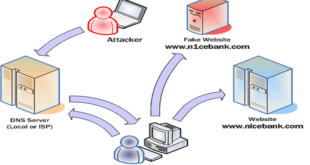
dns2proxy is an offensive DNS server that offers various features for post-exploitation once you’ve changed the DNS server of a victim. This tools offers different features for post-explotation once you change the DNS server of a Victim. DNS spoofing, also referred to as DNS cache poisoning, is a form of …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….