The Pentbox is a safety kit containing various tools for streamlining PenTest conducting a job easily. It is programmed in Ruby and oriented to GNU / Linux, with support for Windows, MacOS and every systems where Ruby is installed. In this small article we will explain how to set up …
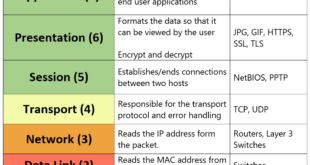
Read More »OSI Layers – Please Do Not Tell Secret Passwords Anytime
I had an interesting day at work trying to figure out how best I can setup a service for a client who is sending UDP licensing traffic through some high-end networking devices over VPN. UDP by design is unreliable. This was causing issues as the UDP packet size was over the …
Read More »Advantages disadvantages of using Proxy vs VPN vs TOR vs TOR and VPN together.
What makes you truly anonymous and leaves next to no trace in the internet? In this post I will discuss the advantages disadvantages of Proxy vs VPN vs TOR vs TOR and VPN together. Internet is a huge and gravely important part of our life these days. It is not …
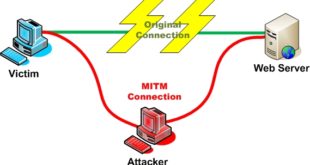
Read More »Man in the Middle Attack using Kali Linux – MITM attack
The man-in-the-middle attack (often abbreviated MITM, MitM, MIM, MiM, MITMA) in cryptography and computer security is a form of active eavesdropping in which the attacker makes independent connections with the victims and relays messages between them, making them believe that they are talking directly to each other over a private …
Read More »New Mozilla Firefox Version 37.0 fixed 13 security issues and introduced Opportunistic Encryption support
Mozilla Foundation just released it’s latest Firefox (Version 37.0). It’s been rolled out for Windows, Mac, Linux and Android operating systems. Those who don’t know, it was released on the week of March 31st. Well to be honest, as of writing this article, Version 37.0.1 was already out on April …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….