Social engineering, in the context of information security, refers to psychological manipulation of people into performing actions or divulging confidential information. A type of confidence trick for the purpose of information gathering, fraud, or system access, it differs from a traditional “con” in that it is often one of many steps in a more complex fraud scheme. In December 2006, United States Congress approved a Senate sponsored bill making the pretexting of telephone records a federal felony with fines of up to $250,000 and ten years in prison for individuals (or fines of up to $500,000 for companies). It was signed by President George W. Bush on 12 January 2000. 
As a security conscious user who follows the best practices like: using unique passwords, 2FA, only using a secure computer and being able to spot phishing attacks from a mile away, I would have thought my accounts and details would be be pretty safe? Wrong.
Because when someone has gone after me, it all goes for nothing. That’s because most systems come with a backdoor, customer support. In this post I’m going to focus on the most grievous offender: Amazon.com
Amazon.com was one of the few companies I trusted with my personal information. After all, I shop there, I used to work as a Software Developer and I am a heavy AWS user (raking up well over $600/month)
It all began with a rather innocuous email:
At first, I assumed it might be a mistake or a delayed email from the time I contacted them months earlier. But curiosity got the better of me, and I contacted Amazon to ask what it was about. They told me that “I” had a conversation with Amazon support? What the hell? It was a text-chat, and they emailed me a transcript:
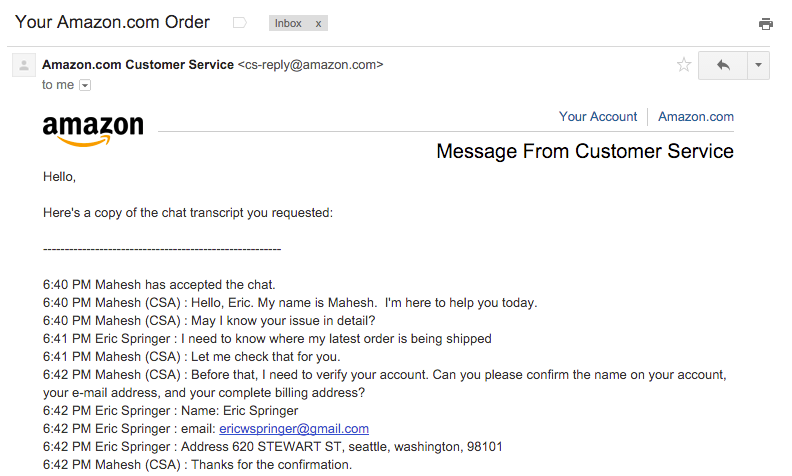
Let me just stop right there, so I can point out that address isn’t mine. It’s just a fake address of a hotel that was in the same zip code where I lived. I used it to register some domains, knowing that the whois information all too often becomes public. I used the same general area as I lived, so that my ip address would match up with it.
Let’s continue:
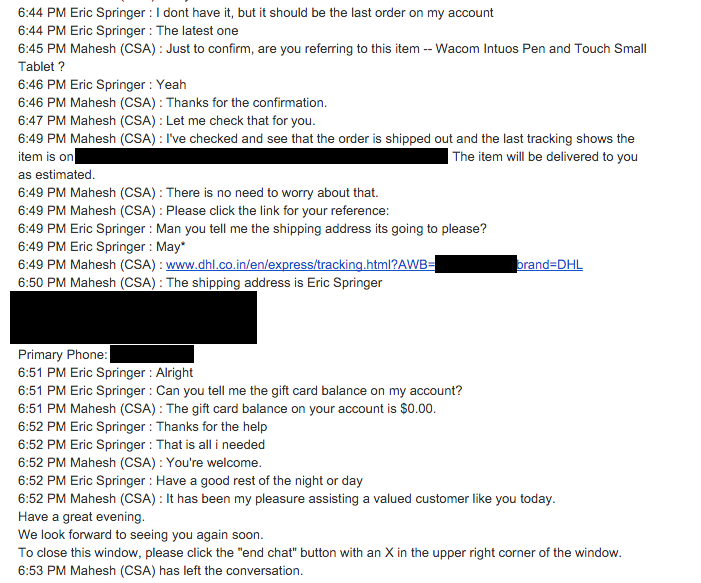
Wow. Just wow. The attacker gave Amazon my fake details from a whois query, and got my real address and phone number in exchange. Now they had enough to bounce around a few services, even convincing my bank to issue them a new copy of my Credit Card.
Trying very hard to not take out my frustrations on an unrelated support rep, I contacted both Amazon Retail and AWS expressing my disappointment and asking them to put a note on my account that it is at extremely high risk of being social engineering, and I will always be capable of logging in. Amazon Retail said they would put a note, and have a specialist contact me (who never did) while AWS was dismissive of even a risk existing.
Fast forward a couple of months, I made the big mistake of thinking the risk was gone, giving Amazon my fresh credit card and now new address details. I receive another email. I feel a pit of my stomach.

So once again, I contact Amazon support to see what happened. This time I had the pleasure of dealing with a support agent who seemed 100% incapable of realizing that someone was impersonating me. I had trouble keeping my composure when he told me I should change my password to prevent people impersonating me. Eventually I had to basically tell him that it was “me” that contacted support and I wanted “my” transcript, which he provided.
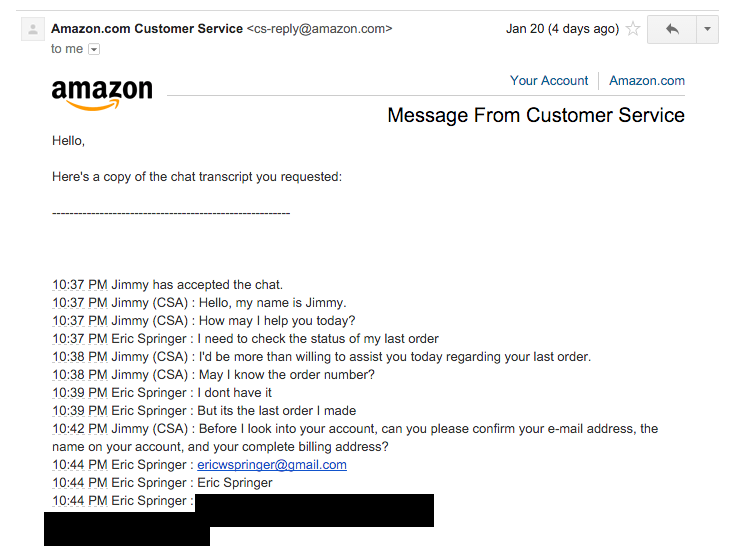
Using the address they got the last time from Amazon..
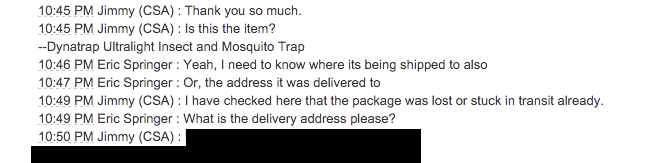
And then goes on to unsuccessfully try get the last digits of my credit card:
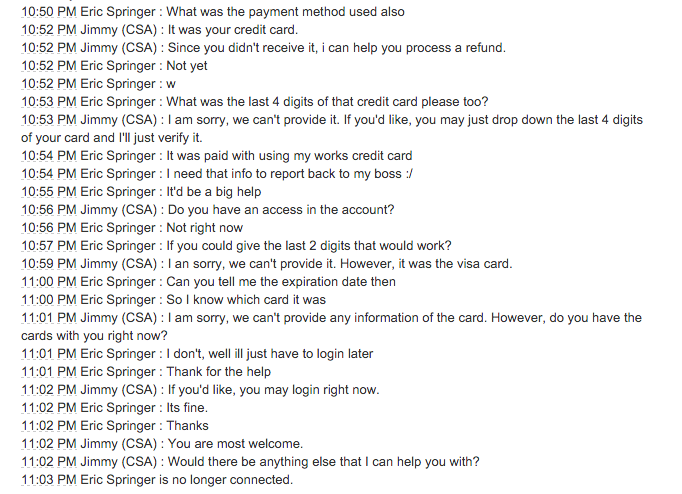
Guess I should count my blessings they didn’t give the last digits of my credit card. I again contact Amazon to reiterate how important it is that they keep my account secure, and not give out my details to anyone with a name and address. They promise they’re putting a note on my account, and it’ll never happen again. And I will be contacted by a specialist (never happened, again)
This time I decide I can no longer trust Amazon with my address, and delete it from my account.
Fast forward another day:
This time, I can’t get a transcript of the conversation. They contacted Amazon by phone, and they don’t have a recording to give me. I’m going to have to assume they got the last digits of my credit card, like they seem to be after.
At this point, Amazon has completely betrayed my trust three times. I have done absolutely everything in my power to secure my account, but it’s hopeless. I am in the process of closing my Amazon account, and migrating as much to Google services which seem significantly more robust at stopping these attacks.
After being the victim of these attacks for months, I’d like to make some recommendations for services:
- NEVER DO CUSTOMER SUPPORT UNLESS THE USER CAN LOG IN TO THEIR ACCOUNT. The only exception to this, would be if the user forgot the password, and there should be a very strict policy. The problem is, 9999 times out of 10000 support requests are legitimate, agents get trained to assume they’re legitimate. But in the 1 case they’re not, you can completely fuck someone over.
- Show support agents the ip address of the person connecting. Is it a usual one? Is it a VPN/tor one? etc. Give them a warning to be suspicious.
- Email services should allow me to easily create lots of aliases. Right now the best defense against social engineering seems to be my fastmail account which allows me to create 1 email address alias per service. This makes it incredibly difficult for an attacker when they can’t even figure out your email.
- Please make whois protection default. Mine leaked because a stupid domain I didn’t care about had its namecheap whois protection expire
For users, be extremely careful with the information you share. Even big companies like Amazon can’t keep it safe, they’re far from the worst.
After reading through this article, obviously you would think that Amazon or such companies would be more careful. But another reader tried it, and posted his successful attempt of Social Engineering and obtaining sensitive information’s.
First Chat:
Second Chat:
Countermeasures
Organizations reduce their security risks by:
- Establishing frameworks of trust on an employee/personnel level (i.e., specify and train personnel when/where/why/how sensitive information should be handled)
- Identifying which information is sensitive and evaluating its exposure to social engineering and breakdowns in security systems (building, computer system, etc.)
- Establishing security protocols, policies, and procedures for handling sensitive information.
- Training employees in security protocols relevant to their position. (e.g., in situations such as tailgating, if a person’s identity cannot be verified, then employees must be trained to politely refuse.)
- Performing unannounced, periodic tests of the security framework.
- Reviewing the above steps regularly: no solutions to information integrity are perfect.
- Using a waste management service that has dumpsters with locks on them, with keys to them limited only to the waste management company and the cleaning staff. Locating the dumpster either in view of employees such that trying to access it carries a risk of being seen or caught or behind a locked gate or fence where the person must trespass before they can attempt to access the dumpster.
Sources and acknowledgments
- Thanks to Mitch for bringing this article to my attention.
- Original Article: https://medium.com/@espringe/amazon-s-customer-service-backdoor-be375b3428c4
- Wikipedia: https://en.wikipedia.org/wiki/Social_engineering_(security)
 blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….

I can tell you one thing, check your ssn and watch out for ID theft, get service,where it checks if someone opens new account or gets a loan. Good luck with that
This was an interesting read, thanks for sharing.
Hello ya all folks,
How foolish u can be, to allow Amazon.
In Windows 7 (sp1) I’ve tried and tried over and over again to block Amazon/AWS but they have sooooooo many url’s/search bots running that it won’t work.
Tried to put some of those amazon sites in the ‘Host’s file’ in Windows but they return every time over and over again.
I don’t buy things or use the Amazon services.
They are in your network.
I don’t use FB, No Twitter, No Skype because they’re damn rotten hell.
You folks do think what is he mumbling by now.
Ctrl+Alt+Delete is Windows Taskmanager but you can’t see it that way.
I do use another one in Windows the one you can see with that Amazon is watching/sniffing your network, google and FB also do.
That one is: http://processhacker.sourceforge.net (Windows stuff)
I do believe that Microsoft is payed by Amazon to let them watch/sniff the network.
I don’t like those ‘services’ and I don’t want them in my network.
I don’t have a problem with the ppl who want to use those ‘services’.
Maybe I’m the only one on earth who didn’t love those services, dunno????
Btw, thanks for the great articles on your site.
Keep up the good work, tnx.