How often you bumped into a .gz file where you need to check the contents?  I know I do quite often. A gz file is a compressed file created with gzip and I didn’t knew better, I would copy the file into another folder, uncompress it and then look into the contents. Is there a way to avoid these unnecessary decompression and waste time? Of course there is. In Linux, you can view contents of a compressed .gz file without uncompressing (uncompress on the fly actually or in temp directory) which makes perfect sense for those who deal with large log files and does forensic stuffs. The way it’s done is by using Z commands.
I know I do quite often. A gz file is a compressed file created with gzip and I didn’t knew better, I would copy the file into another folder, uncompress it and then look into the contents. Is there a way to avoid these unnecessary decompression and waste time? Of course there is. In Linux, you can view contents of a compressed .gz file without uncompressing (uncompress on the fly actually or in temp directory) which makes perfect sense for those who deal with large log files and does forensic stuffs. The way it’s done is by using Z commands.
Z commands for example: zcat allows you to view contents of a compressed file, zless or zmore allows you to do paging (page by page viewing of a file), zgrep or zegrep allows you to search within a compressed file, zdiff or zcmp allows you to compare two files… Sounds good? I bet it does. Welcome to Z commands that you can use to view, search, compare and page compressed files without wasting time uncompressing.
First of all, lets find some compressed files to see what it actually looks like.
Compressed files:
Open a terminal and browse to /var/log. /var/log is where most of your logs files will go by default unless otherwise specified by an application/system. Perform a list (ls) command to see contents of that directory. As you can see, many .gz files in there.
root@kali:~# cd /var/log root@kali:/var/log# ls alternatives.log debug kern.log.1 mysql.log.4.gz syslog.6.gz alternatives.log.1 debug.1 kern.log.2.gz mysql.log.5.gz syslog.7.gz apache2 debug.2.gz kern.log.3.gz mysql.log.6.gz sysstat apt debug.3.gz kern.log.4.gz mysql.log.7.gz tor aptitude dmesg lastlog news unattended-upgrades aptitude.1.gz dmesg.0 lpr.log nginx user.log auth.log dmesg.1.gz mail.err ntpstats user.log.1 auth.log.1 dmesg.2.gz mail.info openvas user.log.2.gz auth.log.2.gz dmesg.3.gz mail.log pm-powersave.log user.log.3.gz auth.log.3.gz dmesg.4.gz mail.warn pm-powersave.log.1 user.log.4.gz auth.log.4.gz dpkg.log messages postgresql wtmp bootstrap.log dpkg.log.1 messages.1 pycentral.log wtmp.1 btmp dradis messages.2.gz samba wvdialconf.log btmp.1 exim4 messages.3.gz speech-dispatcher Xorg.0.log chkrootkit faillog messages.4.gz stunnel4 Xorg.0.log.old ConsoleKit fontconfig.log mysql syslog Xorg.1.log daemon.log fsck mysql.err syslog.1 Xorg.1.log.old daemon.log.1 gdm3 mysql.log syslog.2.gz daemon.log.2.gz inetsim mysql.log.1.gz syslog.3.gz daemon.log.3.gz installer mysql.log.2.gz syslog.4.gz daemon.log.4.gz kern.log mysql.log.3.gz syslog.5.gz
I will use dmesg and dmesg.1.gz files for this exercise.
Now normally if you want to see the contents of dmesg file, you would use cat command and pipe it to either more or less for pagination:
root@kali:/var/log# cat dmesg | more (output - truncated) [ 0.000000] Initializing cgroup subsys cpuset [ 0.000000] Initializing cgroup subsys cpu [ 0.000000] Initializing cgroup subsys cpuacct [ 0.000000] Linux version 3.14-kali1-amd64 (debian-kernel@lists.debian.org) (gcc version 4.7.2 (Debian 4.7.2-5) ) #1 SMP Debian 3.14.5-1kali1 (2014-06-07) [ 0.000000] Command line: BOOT_IMAGE=/boot/vmlinuz-3.14-kali1-amd64 root=UUID=9f174fa5-0c59-4024-b307-463b7bc1752d ro initrd=/install/gtk/initrd.gz quiet nouveau.modeset=0 [ 0.000000] e820: BIOS-provided physical RAM map: [ 0.000000] BIOS-e820: [mem 0x0000000000000000-0x000000000009efff] usable [ 0.000000] BIOS-e820: [mem 0x000000000009f000-0x000000000009ffff] reserved [ 0.000000] BIOS-e820: [mem 0x00000000000e4000-0x00000000000fffff] reserved [ 0.000000] BIOS-e820: [mem 0x0000000000100000-0x00000000bd77ffff] usable [ 0.000000] BIOS-e820: [mem 0x00000000bd780000-0x00000000bd78dfff] ACPI data [ 0.000000] BIOS-e820: [mem 0x00000000bd78e000-0x00000000bd7cffff] ACPI NVS [ 0.000000] BIOS-e820: [mem 0x00000000bd7d0000-0x00000000bd7dffff] reserved [ 0.000000] BIOS-e820: [mem 0x00000000bd7ed000-0x00000000bdffffff] reserved [ 0.000000] BIOS-e820: [mem 0x00000000fed20000-0x00000000fed3ffff] reserved [ 0.000000] BIOS-e820: [mem 0x00000000fee00000-0x00000000fee00fff] reserved [ 0.000000] BIOS-e820: [mem 0x00000000ffb00000-0x00000000ffffffff] reserved [ 0.000000] BIOS-e820: [mem 0x0000000100000000-0x000000023fffffff] usable [ 0.000000] NX (Execute Disable) protection: active [ 0.000000] SMBIOS 2.6 present. [ 0.000000] DMI: Acer Veriton S680G /Veriton S680G, BIOS P01-B0C2 03/25/2011 [ 0.000000] e820: update [mem 0x00000000-0x00000fff] usable ==> reserved [ 0.000000] e820: remove [mem 0x000a0000-0x000fffff] usable [ 0.000000] No AGP bridge found --More--
root@kali:/var/log# cat dmesg | less
But what happens when you try to view contents of a compressed file such as dmesg.1.gz
root@kali:/var/log# cat dmesg.1.gz | more
j_�Sdmesg.0��$�,�ה8�&e�~9��4j�q��~��F�Y��QH�.U;O�^L*�
�8�K7��k;tI���G��� ��I�ft�qE���5�ճ�hVG�d��P$�����X8��dȉ�K�ˏ~�fv|\fO �g��w���g ��3�7�u�2X�K�..3e �
��:q=�.sI�zM}�CB�vܫ
3q���˚���M��:�G�<�+٤�"`'�Y^��` �'yf�IpLm�y��.\���5U�4�`�����阸vf���xû�uv���}�ꀗ�u8��+�1W�
I��1�Ǹ��
�[4��wO�6w���p�fw���l��9�����I� ���9��
�����6��D��@^Lr�Y�N2��{�ﰄ��?:�M�����ʳ
>'2�h�J�9
Well, that wasn’t helpful, wasn’t it? It’s in non-human readable format. This is where Z commands comes to rescue.
Use zcat to view compressed files
What you do is pretty much add z infront of your cat command. See example below:
root@kali:/var/log# zcat dmesg.1.gz | more [ 0.000000] Initializing cgroup subsys cpuset [ 0.000000] Initializing cgroup subsys cpu [ 0.000000] Initializing cgroup subsys cpuacct [ 0.000000] Linux version 3.14-kali1-amd64 (debian-kernel@lists.debian.org) (gcc version 4.7.2 (Debian 4.7.2-5) ) #1 SMP Debian 3.14.5-1kali1 (2014-06-07) [ 0.000000] Command line: BOOT_IMAGE=/boot/vmlinuz-3.14-kali1-amd64 root=UUID=9f174fa5-0c59-4024-b307-463b7bc1752d ro initrd=/install/gtk/initrd.gz quiet nouveau.modeset=0 [ 0.000000] e820: BIOS-provided physical RAM map:
That is so easy…
Using zcat to view files instead of cat
By this time, you are already getting the hang of it. But what happens if you want to view a regular (uncompressed file) using zcat?
root@kali:/var/log# zcat dmesg gzip: dmesg: not in gzip format
Well, that wasn’t very helpful. But there’s a way around that, just use a -f flag which will allow you to view any file compressed or not uzing zcat.
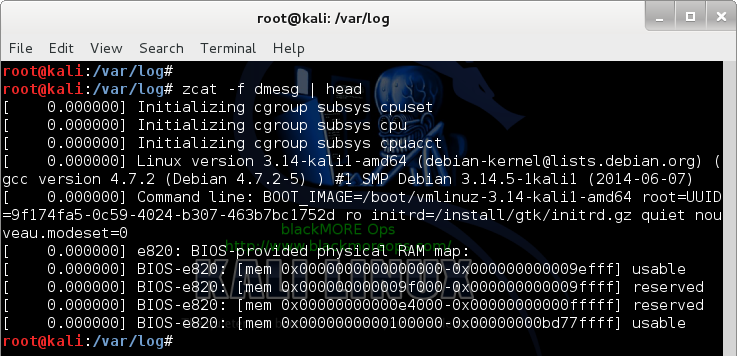
root@kali:/var/log# zcat -f dmesg | more [ 0.000000] Initializing cgroup subsys cpuset [ 0.000000] Initializing cgroup subsys cpu [ 0.000000] Initializing cgroup subsys cpuacct [ 0.000000] Linux version 3.14-kali1-amd64 (debian-kernel@lists.debian.org) (gcc version 4.7.2 (Debian 4.7.2-5) ) #1 SMP Debian 3.14.5-1kali1 (2014-06-07) [ 0.000000] Command line: BOOT_IMAGE=/boot/vmlinuz-3.14-kali1-amd64 root=UUID=9f174fa5-0c59-4024-b307-463b7bc1752d ro initrd=/install/gtk/initrd.gz quiet nouveau.modeset=0
Much better. The reason I am showing this is because now you can write a script to view files, search files irrespective of compression.
 blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….