This is something I would like to keep track, so posting it here. Very useful and scary that how easily it can happen.
Alert (TA14-017A)
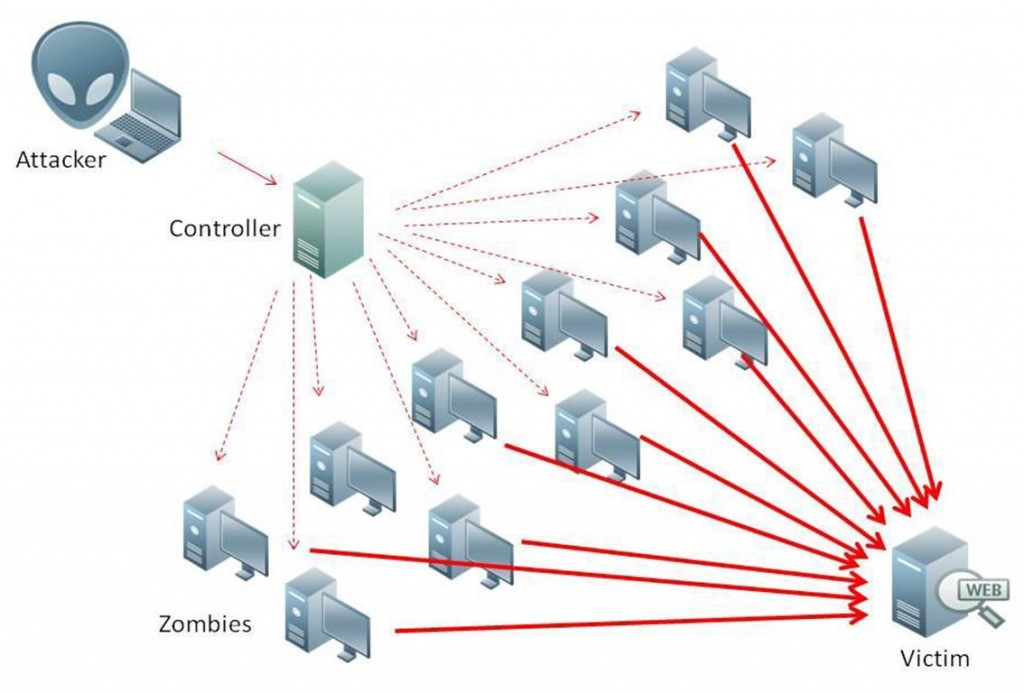
Following diagram shows how UDP based Amplification Attacks are carried out. Very simple, a 4MB ADSL connection can amplify upto 400MB traffiic easily. Take note of the Bandwidth amplification factor table below.
Systems Affected
Certain UDP protocols have been identified as potential attack vectors.
Following list is what I’ve found useful and interesting reading material, some are more common due to recent activity and DOS war between CloudFlare, SpamHaus and Cyber Bunker. Rest of services are quite low profile, but according to US Cert, they all have the similar vulnerability and can cause massive system outage. I will keep adding more links and tools below, if you have and interesting reading material or proof of concept tool, let me know via comment section and I will add it to the list.
- DNS
Honeypot DNS and amplification attacksProof of Concept DNS Amplification attack tool from noptrix
- NTP
Understanding and mitigating NTP-based DDoS attacks
Technical Details Behind a 400Gbps NTP Amplification DDoS Attack
NTP Amplification Attack Tool posted by anonymous user in github
- SNMPv2
SNMP Reflected Amplification DDoS Attack
SNMP Reflected Denial of Service
- NetBIOS
NETBIOS based pentesting tutorial by Gaurav Kumar
Denial of Service Attack in NetBIOS Services
NetBIOS Attack Methods
- SSDP
- CharGEN
Chargen denial of service (Chargen Denial of Service)
A Chargen-based DDoS? Chargen is still a thing?
ECHO Chargen Loop DoS
- QOTD
- BitTorrent
- Kad
- Quake Network Protocol
- Steam Protocol
Overview
A Distributed Reflective Denial of Service (DRDoS) attack is an emerging form of Distributed Denial of Service (DDoS) that relies on the use of publicly accessible UDP servers, as well as bandwidth amplification factors, to overwhelm a victim system with UDP traffic.
Description
UDP, by design, is a connection-less protocol that does not validate source IP addresses. Unless the application-layer protocol uses countermeasures such as session initiation, it is very easy to forge the IP packet datagram to include an arbitrary source IP address [7]. When many UDP packets have their source IP address forged to a single address, the server responds to that victim, creating a reflected Denial of Service (DoS) Attack.
Recently, certain UDP protocols have been found to have particular responses to certain commands that are much larger than the initial request. Where before, attackers were limited linearly by the number of packets directly sent to the target to conduct a DoS attack, now a single packet can generate tens or hundreds of times the bandwidth in its response. This is called an amplification attack, and when combined with a reflective DoS attack on a large scale it makes it relatively easy to conduct DDoS attacks.
To measure the potential effect of an amplification attack, we use a metric called the bandwidth amplification factor (BAF). BAF can be calculated as the number of UDP payload bytes that an amplifier sends to answer a request, compared to the number of UDP payload bytes of the request.
The list of known protocols, and their associated bandwidth amplification factors, is listed below. US-CERT would like to offer thanks to Christian Rossow for providing this information to us.
| Protocol | Bandwidth Amplification Factor | Vulnerable Command |
| DNS | 28 to 54 | see: TA13-088A [1] |
| NTP | 556.9 | see: TA14-013A [2] |
| SNMPv2 | 6.3 | GetBulk request |
| NetBIOS | 3.8 | Name resolution |
| SSDP | 30.8 | SEARCH request |
| CharGEN | 358.8 | Character generation request |
| QOTD | 140.3 | Quote request |
| BitTorrent | 3.8 | File search |
| Kad | 16.3 | Peer list exchange |
| Quake Network Protocol | 63.9 | Server info exchange |
| Steam Protocol | 5.5 | Server info exchange |
Impact
Attackers can utilize the bandwidth and relative trust of large servers that provide the above UDP protocols to flood victims with unwanted traffic, a DDoS attack.
Solution
DETECTION
Detection of DRDoS attacks is not easy, due to their use of large, trusted servers that provide UDP services. As a victim, traditional DoS mitigation techniques may apply.
As a network operator of one of these exploitable services, look for abnormally large responses to a particular IP address. This may indicate that an attacker is using your service to conduct a DRDoS attack.
MITIGATION
Source IP Verification
Because the UDP requests being sent by the attacker-controlled clients must have a source IP address spoofed to appear as the victim’s IP, the first step to reducing the effectiveness of UDP amplification is for Internet Service Providers to reject any UDP traffic with spoofed addresses. The Network Working Group of the Internet Engineering Task Force (IETF) released Best Current Practice 38 document in May 2000 and Best Current Practice 84 in March 2004 that describes how an Internet Service Provider can filter network traffic on their network to reject packets with source addresses not reachable via the actual packet’s path [3][4]. The changes recommended in these documents would cause a routing device to evaluate whether it is possible to reach the source IP address of the packet via the interface that transmitted the packet. If it is not possible, then the packet most likely has a spoofed source IP address. This configuration change would substantially reduce the potential for most popular types of DDoS attacks. As such, we highly recommend to all network operators to perform network ingress filtering if possible. Note that it will not explicitly protect a UDP service provider from being exploited in a DRDoS (all network providers must use ingress filtering in order to completely eliminate the threat).
To verify your network has implemented ingress filtering, download the open source tools from the Spoofer Project [5].
Traffic Shaping
Limiting responses to UDP requests is another potential mitigation to this issue. This may require testing to discover the optimal limit that does not interfere with legitimate traffic. The IETF released Request for Comment 2475 and Request for Comment 3260 that describes some methods to shape and control traffic [6] [8]. Most network devices today provide these functions in their software.
References
- [1] DNS Amplification Attacks
- [2] NTP Amplification Attacks Using CVE-2013-5211
- [3] Network Ingress Filtering: Defeating Denial of Service Attacks which employ IP Source Address Spoofing
- [4] Ingress Filtering for Multihomed Networks
- [5] The Spoofer Project
- [6] An Architecture for Differentiated Services
- [7] SIP: Session Initiation Protocol
- [8] New Terminology and Clarifications for Diffserv
 blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….

Hi there!!!
Thank you very much for your detailed article, it has been, for me, an amazing article. I will read the links above to try understand deeply how it works
Best regards
Alex