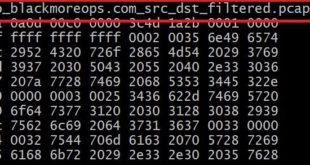
I'm sure you bumped into situations where you needed to fake IP address in a capture file. This maybe required when you're trying to send the capture file to someone that you don't really share your real IP's with or you just want to change cause you can. If you've tried this and looked around the interwebs, you'd surely know that there's not many guides available and most people would just tell casually "just use sed" or use "WireEdit" and pay some fees for their license. Now, both works but I just got pissed off in a particular situation where sed wasn't an options (the file was literally few GB's in size and most text editors would just freeze) and to make things worse, I needed to filter a lot of info and only keep source and destination IP addresses in there for privacy's sake. Yeah, that means removing all those noises like DNS, UDP, Broadcast, Cisco ARP, Broadcast, MDNS (yes, that too), SSDP ... yes, pretty much anything except TCP/UDP, HTTP and TLS trarffic between my server and the destination server. So, in summary I had to filter all of these noises and change IP address in packet capture file to hide source IP address, this is similar to faking IP address in packet captures. You can also use other tools to do it on the fly but they require more setup and all I just wanted to do is to hide my source IP.
Read More »How to access Dark Web?
The concept of the Dark Web isn’t vastly different from the Surface Web. There are message boards (e.g. 8chan, nntpchan), places you can buy things (e.g. Alphabay, Hansa), and blogs (e.g. OnionNews, Deep Web Radio). The rules, or rather a lack thereof, is what makes the Dark Web unique. Anything …
Read More »SecLists – Security Tester’s Companion
SecLists is the security tester’s companion. It’s a collection of multiple types of lists used during security assessments, collected in one place. List types include usernames, passwords, URLs, sensitive data patterns, fuzzing payloads, web shells, and many more. The goal is to enable a security tester to pull this repo …
Read More »Using Rigorous Credential Control to Mitigate Trusted Network Exploitation
Recommended best practices for mitigating this threat include rigorous credential and privileged-access management, as well as remote-access control, and audits of legitimate remote-access logs. While these measures aim to prevent the initial attack vectors and the spread of malicious activity, there is no single proven threat response. Using a defense-in-depth …
Read More »Advanced Persistent Threat Activity Exploiting Managed Service Providers
Organizations should configure system logs to detect incidents and to identify the type and scope of malicious activity. Properly configured logs enable rapid containment and appropriate response. Response An organization’s ability to rapidly respond to and recover from an incident begins with the development of an incident response capability. An …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….