In a traditional brute-force attack, a malicious actor attempts to gain unauthorized access to a single account by guessing the password. This can quickly result in a targeted account getting locked-out, as commonly used account-lockout policies allow three to five bad attempts during a set period of time. During a …
Read More »Cyber Actors Target Home and Office Routers and Networked Devices Worldwide
DHS and FBI recommend that all SOHO router owners power cycle (reboot) their devices to temporarily disrupt the malware. Network device management interfaces—such as Telnet, SSH, Winbox, and HTTP—should be turned off for wide-area network (WAN) interfaces, and, when enabled, secured with strong passwords and encryption. Network devices should be upgraded …
Read More »HIDDEN COBRA – FASTCash Campaign targeting banks
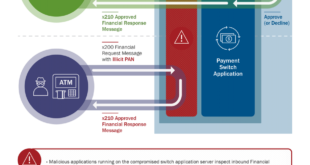
Since at least late 2016, HIDDEN COBRA actors have used FASTCash tactics to target banks in Africa and Asia. At the time of this TA’s publication, the U.S. Government has not confirmed any FASTCash incidents affecting institutions within the United States. FASTCash schemes remotely compromise payment switch application servers within …
Read More »Emotet Malware – one of the most destructive malware right now
Emotet continues to be among the most costly and destructive malware affecting SLTT governments. Its worm-like features result in rapidly spreading network-wide infection, which are difficult to combat. Emotet infections have cost SLTT governments up to $1 million per incident to remediate. Emotet continues to be among the most costly …
Read More »Using Rigorous Credential Control to Mitigate Trusted Network Exploitation
Recommended best practices for mitigating this threat include rigorous credential and privileged-access management, as well as remote-access control, and audits of legitimate remote-access logs. While these measures aim to prevent the initial attack vectors and the spread of malicious activity, there is no single proven threat response. Using a defense-in-depth …
Read More »