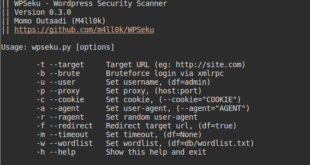
WPSeku is a black box WordPress vulnerability scanner that can be used to scan remote WordPress installations to find security issues. Features of WPSeku WordPress Security Scanner WPSeku supports various types of scanning including: Testing for XSS Vulnerabilities Testing for SQL Injection Vulnerabilities Testing for LFI Vulnerabilities Bruteforce login via …
Read More »Gain root access in macOS High Sierra #iamroot
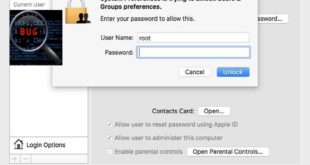
It’s a rather embarrassing a bug that was discovered by developer Lemi Ergin that allows anyone to gain root access in macOS High Sierra with a blank password. Yes, all you need to do is just press enter enough times and you’re root. In fact everyone now using #iamroot just to …
Read More »Wireless WPA2 password cracking using KRACK attacks
We discovered serious weaknesses in WPA2, a protocol that secures all modern protected Wi-Fi networks. An attacker within range of a victim can exploit these weaknesses using key reinstallation attacks (KRACKs). Concretely, attackers can use this novel attack technique to read information that was previously assumed to be safely encrypted. …
Read More »Fix Java error Unsigned application requesting unrestricted access to system
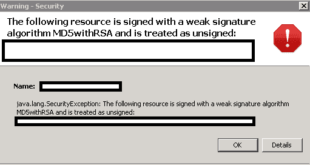
Tried to login to one of my server that requires Java and immediately got this error: Unsigned application requesting unrestricted access to system. The following resource is signed with a weak signature algorithm MD5withRSA and is treated as unsigned After some research on Google I found that the root cause …
Read More »Pay the Ransom or Face the Music – Hackers Threaten Apple Over iCloud Compromised Accounts
If you are an Apple user and thought that your data was secure, perhaps it’s time you retracted that thought. According to Motherboard, an Information and Technology Security magazine, a gang of hackers going by the name “Turkish Crime Family” allegedly claim a hold of over 200 million iCloud Compromised …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….