The sudo command offers a mechanism for providing trusted users with administrative access to a system without sharing the password of the root user. When users given access via this mechanism precede an administrative command with sudo they are prompted to enter their own password. Once authenticated, and assuming the command is permitted, the administrative command is executed as if run by the root user. 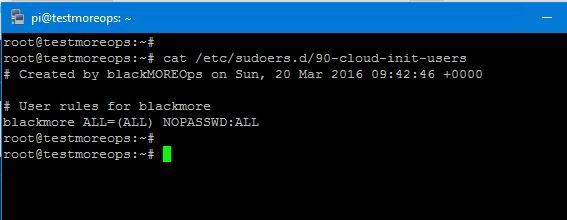
Follow this procedure to create a normal user account and give it sudo access. You will then be able to use the sudo command from this user account to execute administrative commands without logging in to the account of the root user.
Configuring sudo access for single user
Create a file named 90-cloud-init-users in /etc/sudoers.d folder. This file defines the policies applied by the sudo command.
root@testmoreops:~# cd /etc/sudoers.d/ root@testmoreops:~# vi 90-cloud-init-users
Add the following lines.
# Created by blackMOREOps on Sun, 20 Mar 2016 09:42:46 +0000 # User rules for blackmore blackmore ALL=(ALL) NOPASSWD:ALL
Here, NOPASSWD:ALL is the special key I am using. Once you’re logged in as blackmore, you can simply do sudo -s to become root without typing in the password again. Just some convenience. I don’t recommend it in Production Environment though.
Configuring sudo access for group
Create a file named 90-cloud-init-users in /etc/sudoers.d folder. Add the following lines.
## Allows people in group wheel to run all commands %wheel ALL=(ALL) NOPASSWD:ALL
Save your changes and exit the editor. If you dont have a user already added to wheel group, you can add them by using the usermod command. Here testmore is the username.
# usermod -aG wheel testmore
Test that the updated configuration allows the user you created to run commands using sudo.
Use the su to switch to the new user account that you created.
# su testmore -
Use the groups to verify that the user is in the wheel group.
$ groups testmore wheel
Use the sudo -s command to become root user. At this point you don’t have to type in the password anymore cause we’ve used NOPASSWD:ALL to tell it that no password is required for users in this usergroup.
This is pretty simple but useful when you are working on a development environment. In Production environment, you would want to restrict sudo access; that means to become root, you need to use su - and then type in the root password separately.
You can achieve the same results by modifying /etc/sudoers file, I however found that by adding it under /etc/sudoers.d/90-cloud-init-users file, it is easier to maintain when you have lots of groups and users to maintain. I guess it’s less cluttered.
Hope you’ve enjoyed the guide on configuring sudo access for single user and group with NOPASSWORD.
I found the first method of using NOPASSWORD in Microsoft Azure’s Classic Virtual Machine. Wonder why Azure wanted to do deploy it that way? Would you do it in a prod environment? How would you recommend doing it in cloud server?
 blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….