With Google, Microsoft and every major technological giants sunsetting sha-1 due to it’s vulnerability, sha256 is the new standard. It seems to be an issue almost all Infrastructure Administrators are facing right now. Those who are using managed PKI console, it’s very easy and straight forward and the signing authority such a Symantec/Verisign or GoDaddy will take care of the signature hash.  Users just select if they want to use sha1, sha256 and so on. But for those who have a test infrastructure where you are using self signed SSL/TLS certificate, they need to generate and or replace all their existing certificates with self-signed x509 certificate with 2048-bit key and sign with sha256 hash using OpenSSL. Generating a 2048-bit public key x509 certificate with sha256 digest algorithm is not very tough. But OpenSSL help menu can be confusing. This post would help anyone who had to walk that path of upgrading sha1 or issuing a new self-signed x509 certificate with 2048-bit key and sign with sha256 hash.
Users just select if they want to use sha1, sha256 and so on. But for those who have a test infrastructure where you are using self signed SSL/TLS certificate, they need to generate and or replace all their existing certificates with self-signed x509 certificate with 2048-bit key and sign with sha256 hash using OpenSSL. Generating a 2048-bit public key x509 certificate with sha256 digest algorithm is not very tough. But OpenSSL help menu can be confusing. This post would help anyone who had to walk that path of upgrading sha1 or issuing a new self-signed x509 certificate with 2048-bit key and sign with sha256 hash.
Step 1: Supported OpenSSL version for sha256
As of writing this article(17th March 2015), the current OpenSSL version in Debian Linux “OpenSSL 1.0.1e 11 Feb 2013“.
blackMORE@debian:~$ apt-cache show openssl Package: openssl Version: 1.0.1e-2+deb7u14 Installed-Size: 1082 Maintainer: Debian OpenSSL Team <pkg-openssl-devel@lists.alioth.debian.org> Architecture: amd64 Depends: libc6 (>= 2.7), libssl1.0.0 (>= 1.0.1e-2+deb7u5), zlib1g (>= 1:1.1.4) Suggests: ca-certificates Description-en: Secure Socket Layer (SSL) binary and related cryptographic tools This package contains the openssl binary and related tools. . It is part of the OpenSSL implementation of SSL. . You need it to perform certain cryptographic actions like: - Creation of RSA, DH and DSA key parameters; - Creation of X.509 certificates, CSRs and CRLs; - Calculation of message digests; - Encryption and decryption with ciphers; - SSL/TLS client and server tests; - Handling of S/MIME signed or encrypted mail.
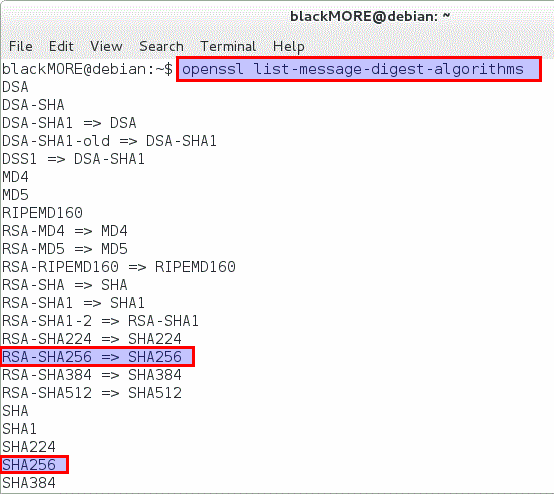
If you want to conclusively determine whether your installed version of OpenSSL supports SHA256, you can use the following command:
blackMORE@debian:~$ openssl list-message-digest-algorithms DSA DSA-SHA DSA-SHA1 => DSA DSA-SHA1-old => DSA-SHA1 DSS1 => DSA-SHA1 MD4 MD5 RIPEMD160 RSA-MD4 => MD4 RSA-MD5 => MD5 RSA-RIPEMD160 => RIPEMD160 RSA-SHA => SHA RSA-SHA1 => SHA1 RSA-SHA1-2 => RSA-SHA1 RSA-SHA224 => SHA224 RSA-SHA256 => SHA256 RSA-SHA384 => SHA384 RSA-SHA512 => SHA512 SHA SHA1 SHA224 SHA256 SHA384 SHA512 <--SNIP--> blackMORE@debian:~$ clear
Step 2: Generate x509 certificate with 2048-bit key and sign with sha256 hash
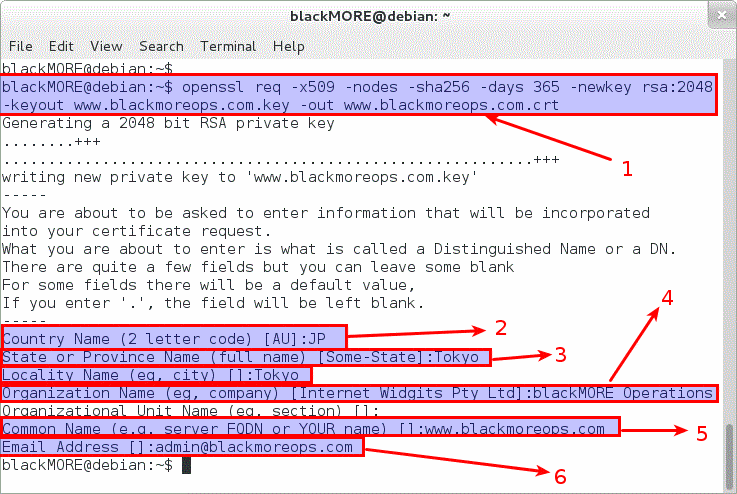
To generate x509 certificate with 2048-bit key and sha256 hash using OpenSSL, use the following command:
blackMORE@debian:~$ openssl req -x509 -nodes -sha256 -days 365 -newkey rsa:2048 -keyout www.blackmoreops.com.key -out www.blackmoreops.com.crt Generating a 2048 bit RSA private key ........+++ ...........................................................+++ writing new private key to 'www.blackmoreops.com.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [AU]:JP State or Province Name (full name) [Some-State]:Tokyo Locality Name (eg, city) []:Tokyo Organization Name (eg, company) [Internet Widgits Pty Ltd]:blackMORE Operations Organizational Unit Name (eg, section) []: Common Name (e.g. server FQDN or YOUR name) []:www.blackmoreops.com Email Address []:admin@blackmoreops.com blackMORE@debian:~$ clear
See screenshot below:
Step 3: Verify sha256 hash function in self-signed x509 digital certificate
Now the certificate is generated, you need to verify whether the certificate is actually used sha256 hash function for encryption. Here is the OpenSSL command through which you can verify:
blackMORE@debian:~$ openssl x509 -noout -text -in www.blackmoreops.com.crt Certificate: Data: Version: 3 (0x2) Serial Number: 14926338292752877067 (0xcf25019818d8860b) Signature Algorithm: sha256WithRSAEncryption Issuer: C=JP, ST=Tokyo, L=Tokyo, O=blackMORE Operations, CN=www.blackmoreops.com/emailAddress=admin@blackmoreops.com Validity Not Before: Mar 16 14:07:15 2015 GMT Not After : Mar 15 14:07:15 2016 GMT Subject: C=JP, ST=Tokyo, L=Tokyo, O=blackMORE Operations, CN=www.blackmoreops.com/emailAddress=admin@blackmoreops.com Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (2048 bit) Modulus: 00:c3:e3:3f:a9:38:27:e2:1b:e4:e4:6f:66:33:6f: bf:79:ab:b9:b2:16:52:b9:d9:98:ba:dd:e7:ad:58: 50:e6:b9:12:96:32:32:2a:24:1e:fb:ee:4f:11:12: dd:c6:1b:d5:af:80:93:5a:11:ad:2d:03:fd:59:d1: 40:b4:0d:c1:90:1f:b6:1d:8f:6c:a6:66:5d:9c:50: 10:ae:24:6f:df:77:52:b6:aa:c2:c5:23:3d:b2:60: 51:99:90:b1:f7:44:ec:56:2c:49:4f:7f:64:17:88: 75:80:85:f7:57:1b:a0:1e:a7:2f:16:0a:9c:6b:36: 11:88:15:8c:e0:1a:34:40:fa:fd:7d:95:16:8a:6a: e3:10:7e:04:e8:ca:87:e9:9f:31:4d:3a:e0:6a:bd: 70:3e:b6:85:01:6f:24:38:c6:78:b9:54:07:41:46: 43:e6:b7:55:f5:0f:79:91:59:1d:bc:df:f1:36:dc: c2:1d:fb:3a:8b:0a:18:ed:57:8b:bc:c0:e3:71:ee: 47:fa:c7:a8:86:5c:93:38:c3:e6:30:34:34:04:10: 45:2b:29:13:a5:4f:b1:85:b7:ea:ed:b4:a2:a7:42: 6f:bc:01:db:30:a1:33:dc:61:0a:eb:e1:c8:97:50: 5c:58:55:08:47:60:a0:a1:b7:18:56:02:54:bd:4a: ea:dd Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Subject Key Identifier: D9:59:62:5A:C9:02:B3:AC:DD:62:C5:B6:DA:1B:1C:38:7A:6D:21:24 X509v3 Authority Key Identifier: keyid:D9:59:62:5A:C9:02:B3:AC:DD:62:C5:B6:DA:1B:1C:38:7A:6D:21:24 X509v3 Basic Constraints: CA:TRUE Signature Algorithm: sha256WithRSAEncryption 86:2a:87:39:d7:a0:06:7b:f9:cc:79:21:84:88:a0:a4:36:10: 28:24:5b:89:0d:3f:a7:aa:fb:f1:25:de:26:74:db:a4:e7:4b: 6d:b5:aa:68:41:da:e9:2c:dc:a7:25:a3:fb:eb:3e:ed:8d:c0: 04:a0:f5:ed:6d:a0:05:44:54:ee:c8:33:ed:9e:79:7c:78:33: fe:b9:dd:15:7f:81:98:c4:59:2c:38:ba:ea:e2:61:0a:aa:08: 9e:ab:6d:a3:01:d6:f1:d2:b8:89:be:a5:c9:10:fc:e2:8d:b3: 70:5d:dd:30:a2:61:25:6e:30:37:7b:4e:14:b8:eb:65:b3:4d: 2d:62:49:9f:f9:3f:24:22:d8:88:74:f4:b9:24:0f:43:f9:5d: 41:62:ba:ed:17:a5:ef:c4:ef:42:8a:34:3c:d2:df:d1:f8:a5: 5c:d1:1c:55:50:97:98:7d:0b:c6:a7:d7:32:4a:65:55:d2:54: 50:00:57:05:da:67:38:16:00:1b:b1:6e:79:1f:bd:a1:62:06: 45:93:4e:c2:53:1a:49:c1:2b:df:e6:6c:fe:3b:f7:dd:de:ff: 7e:e8:22:60:6a:b1:56:4a:2c:01:22:83:08:65:2a:34:f9:5c: 4d:00:3e:2a:66:d2:b7:09:3f:8a:6d:6e:1e:1b:22:19:d3:bf: 48:a4:6c:d6 blackMORE@debian:~$ clear
Step 4: Certificate Installation
Depending on which application and softwares you are using, this step is different for every one of them. Please read related documentations for your software to know more about installation.
Step 5: Testing your installed Certificate
Qualys at SSL Labs has a bunch of free hosted services that allows you to test SSL configuration of Internet facing web servers for SSL issues. You can use their SSL Server Test to determine how strong your SSL is.
Conclusion
Self-signed SSL is mostly use in private environment of in QA, PST environment where service is not used by general users. They allow you to test your services without spending anything. With Google, Microsoft and every major technological giants sunsetting sha-1 due to it’s vulnerability, sha256 is the new standard. Hopefully this post would help anyone who got stuck on issuing a new self-signed x509 certificate with 2048-bit key and sign with sha256 hash. Thanks for reading. Please Share and RT.
 blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….