Search Gitlab For Sensitive Data and Credentials using GitLab Watchman
Read More »Use any Linux applications through a proxy (apt-get, wget etc)
It's pretty normal in many Organizations to use get servers to connect to Internet via a Proxy. In most cases it's for updating apt-get or yum via proxy. However, quite often you might need to download packages directly using wget or curl and setting up apt-get or apt via proxy, wget via proxy, curl via proxy is a pain. What if you could simply setup a Proxy and just use any applications to use that using a simply command? I faced this many times and hence writing this guide. Note that if you're only allowing apt-get via proxy then stick with configuring /etc/apt.conf or /etc/apt/conf.d/00proxy or something similar but if you need to allow different applications via a proxy then this method is best and simplest.
Read More »Sophisticated Spearphishing Campaign Targets Government Organizations, IGOs, and NGOs
This Joint Cybersecurity Advisory uses the MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK®) framework, Version 9. See the ATT&CK for Enterprise for all referenced threat actor tactics and techniques. The Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) are engaged in addressing a spearphishing …
Read More »Machine Learning Network Share Password Hunting Toolkit
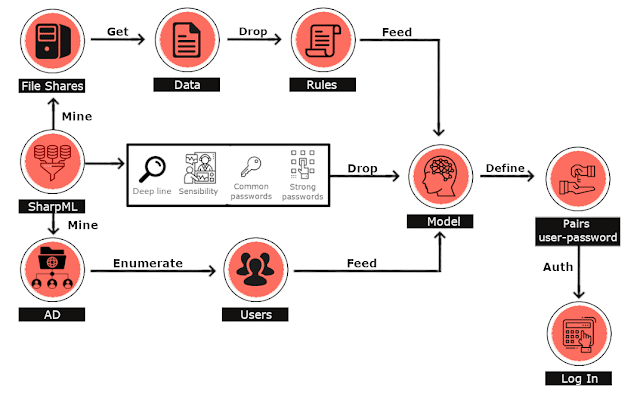
SharpML is a proof of concept file share data mining tool using Machine Learning in Python and C#. The tool is discussed in more detail on this blog here, but is summarised below also. SharpML performs a number of operations with a view to mining file shares, querying Active Directory for users, dropping an ML model and associated rules, performing Active Directory authentication checks, with a view to automating the process of hunting for passwords in file shares by feeding the mined data into the ML model.
Read More »How to fix “Got permission denied while trying to connect to the Docker daemon socket at unix:///var/run/docker.sock error
Quickest way to fix How to fix "Got permission denied while trying to connect to the Docker daemon socket at unix:///var/run/docker.sock: Post "http://%2Fvar%2Frun%2Fdocker.sock/v1.24/auth": dial unix /var/run/docker.sock: connect: permission denied" error
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….