Asynchronous digital subscriber line (DSL or ADSL) modem is a device used to connect a computer or router to a telephone line which provides the digital subscriber line service for connectivity to the Internet, which is often called DSL or ADSL broadband.  In this guide I will show you show you how to scan IP range for connected ADSL or DSL modem routers and find DSL ADSL router hack remotely. This guide applies to Windows, Linux or Mac, so it doesn’t matter what’s your Operating system is, you can try the same steps from all these operating systems. The term DSL or ADSL modem is technically used to describe a modem which connects to a single computer, through a USB port or is installed in a computer PCI slot. The more common DSL or ADSL router which combines the function of a DSL or ADSL modem and a home router, is a standalone device which can be connected to multiple computers through multiple Ethernet ports or an integral wireless access point. Also called a residential gateway, a DSL or ADSL router usually manages the connection and sharing of the DSL or ADSL service in a home or small office network.
In this guide I will show you show you how to scan IP range for connected ADSL or DSL modem routers and find DSL ADSL router hack remotely. This guide applies to Windows, Linux or Mac, so it doesn’t matter what’s your Operating system is, you can try the same steps from all these operating systems. The term DSL or ADSL modem is technically used to describe a modem which connects to a single computer, through a USB port or is installed in a computer PCI slot. The more common DSL or ADSL router which combines the function of a DSL or ADSL modem and a home router, is a standalone device which can be connected to multiple computers through multiple Ethernet ports or an integral wireless access point. Also called a residential gateway, a DSL or ADSL router usually manages the connection and sharing of the DSL or ADSL service in a home or small office network.
Put this together with Wireshark hacking for http websites, you got a nightmare for the user behind that router as all their passwords and details can be tracked very easily.
[toggle title=”What’s in a DSL ADSL Router? – Click to expand” state=”close”]
What’s in a DSL ADSL Router?
A DSL or ADSL router consists of a box which has an RJ11 jack to connect to a standard subscriber telephone line. It has several RJ45 jacks for Ethernet cables to connect it to computers or printers, creating a local network. It usually also has a USB jack which can be used to connect to computers via a USB cable, to allow connection to computers without an Ethernet port. A wireless DSL or ADSL router also has antennas to allow it to act as a wireless access point, so computers can connect to it forming a wireless network. Power is usually supplied by a cord from a wall wart transformer. It usually has a series of LED status lights which show the status of parts of the DSL or ADSL communications link:
- Power light – indicates that the modem is turned on and has power.
- Ethernet lights – There is usually a light over each Ethernet jack. A steady (or sometimes flashing) light indicates that the Ethernet link to that computer or device is functioning
- DSL or ADSL light – a steady light indicates that the modem has established contact with the equipment in the local telephone exchange (DSL or ADSLAM) so the DSL or ADSL link over the telephone line is functioning
- Internet light – a steady light indicates that the IP address and DHCP protocol are initialized and working, so the system is connected to the Internet
- Wireless light – only in wireless DSL or ADSL modems, this indicates that the wireless network is initialized and working
Almost every ADSL DSL modem router provides a management web-page available via Internal network (LAN or Local area network) for device management, configuration and status reporting. You are supposed to login to the management web-page, configure a username password combination provided by your ISP (Internet service provider) which then allows you to connect to internet. The network is divided into two parts:
External Network
External network indicates the part where ADSL DSL modem routers connects to upstream provider for internet connectivity. Once connected to the ISP via a Phone line (ADSL DSL Modem routers can use conventional Copper Phone lines to connect to ISP at a much higher speed), the router gets an IP address. This is usually a Publicly routable IP address which is open to the whole world.
Internal Network
Internal network indicates the part where devices in Local Area Network connects to the ADSL DSL modem router via either Wireless or Ethernet cable. Most modem DSL ADSL Modem routers runs a DHCP server internally which assigns an Internall IP address to the connected device. When I say device, this can be anything from a conventional computer, a laptop, a phone (Android, Apple, Nokia or Blackberry etc.), A smart TV, A Car, NAS, SAN, An orange, A banana, A cow, A dragon, Harry Potter … I mean anything that’s able to connect to internet! So you get the idea. Each device get’s it’s own IP address, a Gateway IP and DNS entries. Depending on different DSL ADSL Modem router, this can be slightly different, but the idea remains the same, the DSL ADSL Router allows users to share internet connectivity. These DSL ADSL Modem Routers are like miniature Gateway devices that can have many services running on them. Usually they all use BusyBox or similar proprietary Linux applications on them. You want to know what a DSL ADSL Router can do? Here’s a list of common services that can run on a DSL ADSL Modem Router:
- ADSL2 and/or ADSL2+ support
- Antenna/ae (wireless)
- Bridge/Half-bridge mode
- Cookie blocking
- DHCP server
- DDNS support
- DoS protection
- Switching
- Intrusion detection
- LAN port rate limiting
- Inbuilt firewall
- Inbuilt or Free micro-filter
- Java/ActiveX applet blocking
- Javascript blocking
- MAC address filtering
- Multiple public IP address binding
- NAT
- Packet filter
- Port forwarding/port range forwarding
- POP mail checking
- QoS (especially useful for VoIP applications)
- RIP-1/RIP-2
- SNTP facility
- SPI firewall
- Static routing
- So-called “DMZ” facility
- RFC1483 (bridged/routed)
- IPoA
- PPPoE
- PPPoA
- Embedded PPPoX login clients
- Parental controls
- Print server inbuilt
- Scheduling by time/day of week
- USB print server
- URL blocking facility
- UPnP facility
- VPN pass-through
- Embedded VPN servers
- WEP 64/128/256 bit (wireless security)
- WPA (wireless security)
- WPA-PSK (wireless security)
That’s a lot of services running on a small device that are configured by nanny, granny, uncle, aunt and the next door neighbour, in short many non technical people around the world. How many of those configured badly? Left ports open left right and center? Didn’t change default admin passwords? Many! I mean MANY! In this guide we will use namp to scan a range of IP addresses, from output we will determine which are DSL ADSL Routers and have left their Management ports open to External Network. (again read top section to know which one is a external network). A typical ADSL Router’s Management interface is available via following URL:
http://10.0.0.1/
http://192.168.0.1/
http://192.168.1.1/
http://192.168.1.254/ etc.
This is the Management page for DSL ADSL modem router and it’s always protected by a password. By default, this password is written below a DSL ADSL modem router in a sticker and they are one of these combinations: Username/Password
admin/admin admin/password admin/pass admin/secret etc.
A lot of the home users doesn’t change this password. Well, that’s ok. It doesn’t hurt much cause this is only available via a connected device. But what’s not OKAY is when users open up their management to the external network. All you need to know what’s the Public IP address for your target and just try to access this management page externally.[/toggle]
Installing NMAP
I use Kali Linux which comes with NMAP Preinstalled. If you are using Windows or Mac (or any other flavour of Linux) go to the following website to download and install NMAP.
Linux Installation:
For Ubuntu, Debian or aptitude based system NMAP is usually made available via default repository. Install NMAP using the following command:
sudo apt-get install nmap
For YUM Based systems such as Redhat, CentOS, install via
sudo yum install nmap
For PACMAN based systems such as Arch Linux, install via
sudo pacman -S nmap
Windows Installation:
For Windows Computers, download installer and run the executable. Link: http://nmap.org/dist/nmap-6.46-setup.exe
Mac Installation:
For Mac users, download installer and install Link: http://nmap.org/dist/nmap-6.46.dmg
Official NMAP site
You can read more about NMAP here: http://nmap.org/
Search for Vulnerable Routers
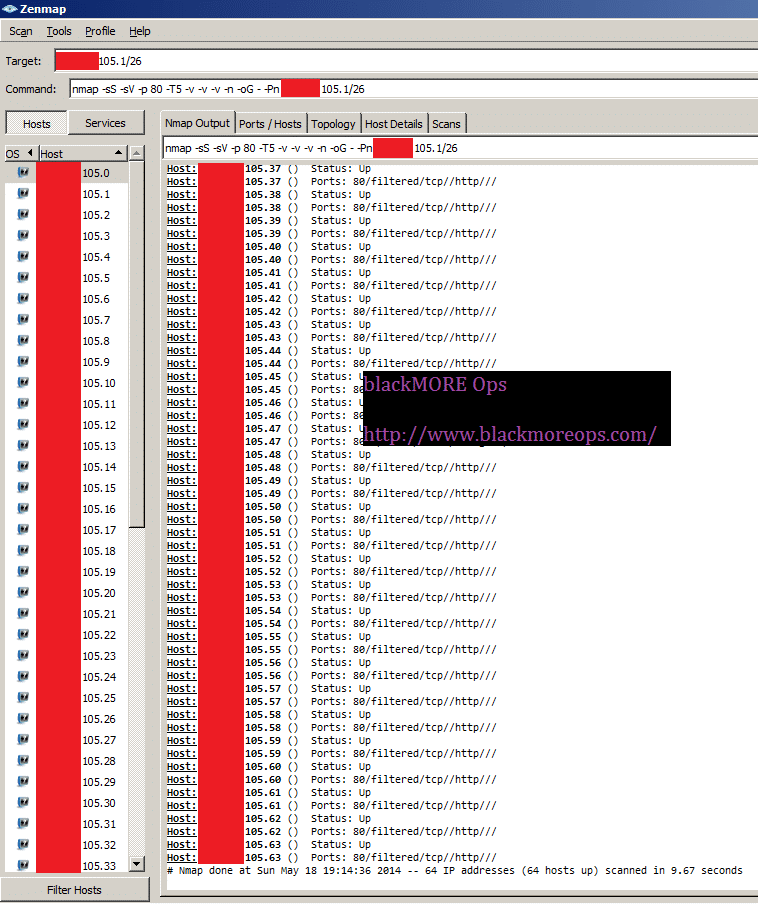
Now that we have NMAP sorted, we are going to run the following command to scan for ADSL Modem Routers based on their Banner on Port 80 to start our ADSL router hack. All you need is to pick an IP range. I’ve used an example below using 101.53.64.1/24 range.
Search from Linux using command Line
In Linux run the following command:
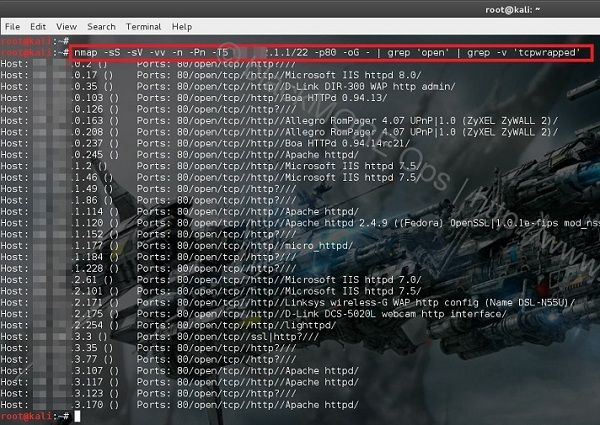
nmap -sS -sV -vv -n -Pn -T5 101.53.64.1-255 -p80 -oG - | grep 'open' | grep -v 'tcpwrapped'
In Windows or Mac open NMAP and copy paste this line:
nmap -sS -sV -vv -n -Pn -T5 101.53.64.1-255 -p80 -oG -
Once it finds the results, search for the word ‘open’ to narrow down results. A typical Linux NMAP command would return outputs line below: (and of course I’ve changed the IP details)
Host: 101.53.64.3 () Ports: 80/open/tcp//tcpwrapped/// Host: 101.53.64.4 () Ports: 80/open/tcp//http//micro_httpd/ Host: 101.53.64.9 () Ports: 80/open/tcp//tcpwrapped/// Host: 101.53.64.19 () Ports: 80/open/tcp//tcpwrapped/// Host: 101.53.64.20 () Ports: 80/open/tcp//http//Fortinet VPN|firewall http config/ Host: 101.53.64.23 () Ports: 80/open/tcp//tcpwrapped/// Host: 101.53.64.31 () Ports: 80/open/tcp//http?/// Host: 101.53.64.33 () Ports: 80/open/tcp//tcpwrapped/// Host: 101.53.64.35 () Ports: 80/open/tcp//http?/// Host: 101.53.64.37 () Ports: 80/open/tcp//http?/// Host: 101.53.64.49 () Ports: 80/open/tcp//http//Gadspot|Avtech AV787 webcam http config/ Host: 101.53.64.52 () Ports: 80/open/tcp//http?/// Host: 101.53.64.53 () Ports: 80/open/tcp//ssl|http//thttpd/ Host: 101.53.64.58 () Ports: 80/open/tcp//http?/// Host: 101.53.64.63 () Ports: 80/open/tcp//tcpwrapped/// Host: 101.53.64.69 () Ports: 80/open/tcp//http//Gadspot|Avtech AV787 webcam http config/ Host: 101.53.64.73 () Ports: 80/open/tcp//http//Allegro RomPager 4.07 UPnP|1.0 (ZyXEL ZyWALL 2)/ Host: 101.53.64.79 () Ports: 80/open/tcp//http//Apache httpd/ Host: 101.53.64.85 () Ports: 80/open/tcp//http//micro_httpd/ Host: 101.53.64.107 () Ports: 80/open/tcp//http?/// Host: 101.53.64.112 () Ports: 80/open/tcp//http?/// Host: 101.53.64.115 () Ports: 80/open/tcp//tcpwrapped/// Host: 101.53.64.123 () Ports: 80/open/tcp//tcpwrapped/// Host: 101.53.64.129 () Ports: 80/open/tcp//http//Allegro RomPager 4.07 UPnP|1.0 (ZyXEL ZyWALL 2)/ Host: 101.53.64.135 () Ports: 80/open/tcp//tcpwrapped/// Host: 101.53.64.145 () Ports: 80/open/tcp//http//micro_httpd/ Host: 101.53.64.149 () Ports: 80/open/tcp//http//Microsoft IIS httpd 6.0/ Host: 101.53.64.167 () Ports: 80/open/tcp//tcpwrapped/// Host: 101.53.64.170 () Ports: 80/open/tcp//http//Allegro RomPager 4.07 UPnP|1.0 (ZyXEL ZyWALL 2)/ Host: 101.53.64.186 () Ports: 80/open/tcp//http?/// Host: 101.53.64.188 () Ports: 80/open/tcp//tcpwrapped/// Host: 101.53.64.193 () Ports: 80/open/tcp//tcpwrapped/// Host: 101.53.64.202 () Ports: 80/open/tcp//http//Apache httpd 2.2.15 ((CentOS))/ Host: 101.53.64.214 () Ports: 80/open/tcp//tcpwrapped/// Host: 101.53.64.224 () Ports: 80/open/tcp//http//Allegro RomPager 4.51 UPnP|1.0 (ZyXEL ZyWALL 2)/
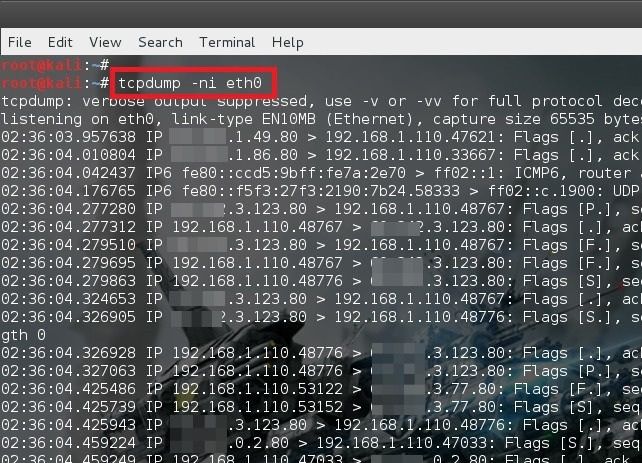
This was taking a long time (we are after all try to scan 256 hosts using the command above). Me being just impatient, I wanted to check if my Kali Linux was actually doing anything to ADSL router hack. I used the following command in a separate Terminal to monitor what my PC was doing… it was doing a lot …
tcpdump -ni eth0
That’s a lot of connected hosts with TCP Port 80 open. Some got ‘tcpwrapped’ marked on them. It means they are possibly not accessible.
Search from Windows, Mac or Linux using GUI – NMAP or Zenmap
Assuming you got NMAP installation sorted, you can now open NMAP (In Kali Linux or similar Linux distro, you can use Zenmap which is GUI version of NAMP cross platform). Copy paste the following line in Command field
nmap -sS -sV -vv -n -Pn -T5 101.53.64.1/26 -p80 -oG -
another version of this command is using different representation of Subnet MASK.
nmap -sS -sV -vv -n -Pn -T5 101.53.64.1-255 -p80 -oG -
Press SCAN Button and wait few minutes till the scan is over.
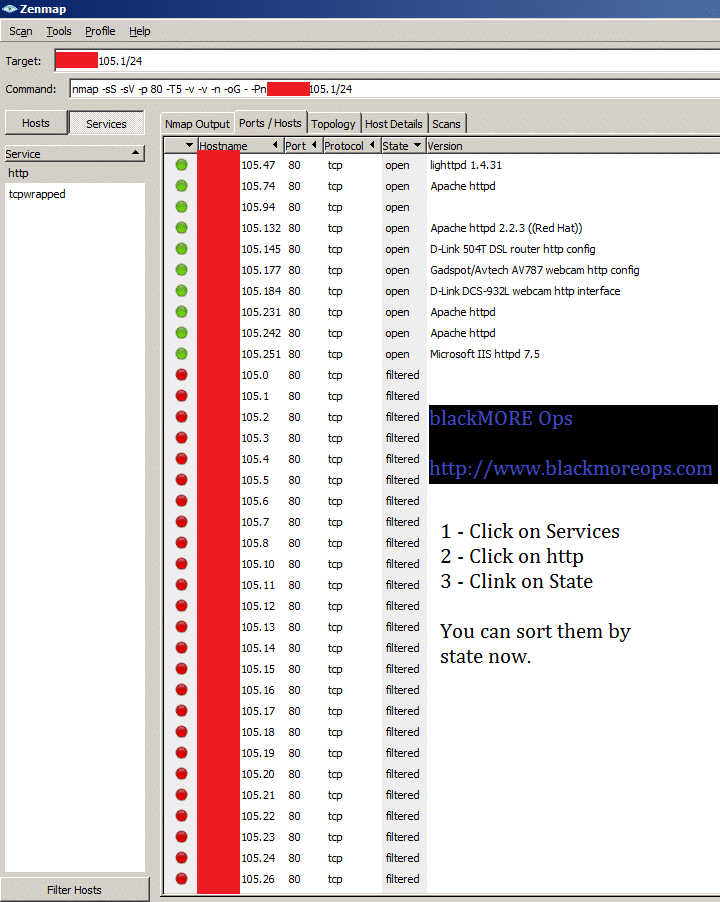
Once you have some results, then you need to find the open devices with open ports. In search Result page:
- Click on Services Button
- Click on http Service
- Click on Ports/Hosts TAB (Twice to sort them by status)
As you can see, I’ve found a few devices with open http port 80.
It is quite amazing how many devices got ports open facing outer DMZ.
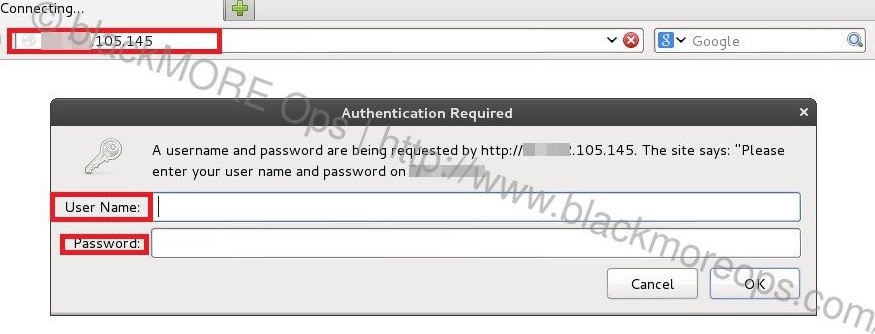
Access Management Webpage
Pick one at a time. For example try this:
http://101.53.64.3
http://101.53.64.4
http://101.53.64.129
You get the idea. If it opens a webpage asking for username and password, try one of the following combinations:
admin/admin admin/password admin/pass admin/secret
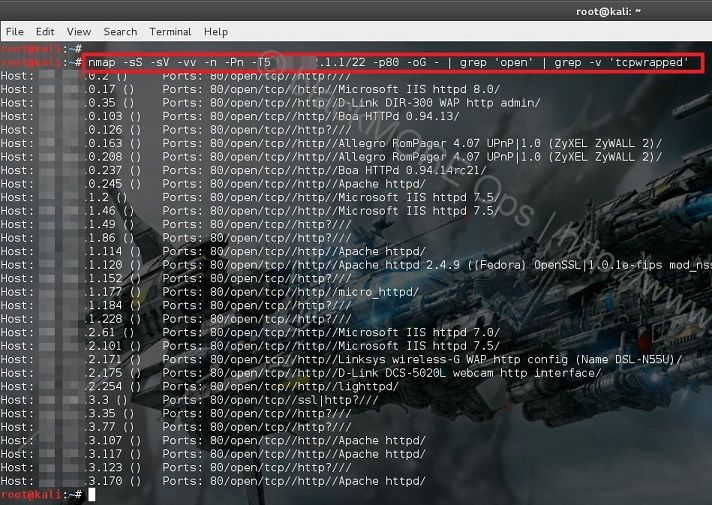
If you can find the Router’s model number and make, you can find exact username and password from this webpage: http://portforward.com/default_username_password/ Before we finish up, I am sure you were already impatient like me as a lot of the routers had ‘tcpwrapped’ on them which was actually stopping us from accessing the web management interface to ADSL router hack. Following command will exclude those devices from our search. I’ve also expanded my search to a broader range using a slightly different Subnet MASK.
nmap -sS -sV -vv -n -Pn -T5 101.53.64.1/22 -p80 -oG - | grep 'open' | grep -v 'tcpwrapped'
In this command I am using /22 Subnet Mask with 2 specific outputs: I am looking for the work ‘open’ and excluding ‘tcpwrapped’ on my output. As you can see, I still get a lot of outputs.
Conclusion
You’ll be surprised how many have default username and passwords enabled. Once you get your access to the router, you can do a lot more, like DNS hijacking, steal username and passwords (for example: Social Media username passwords (FaceBook, Twitter, WebMail etc.)) using tcpdump/snoop on router’s interface and many more using ADSL router hack … Why did I write this guide? I get lots of feedback via Contact Us page. Here’s one for example:
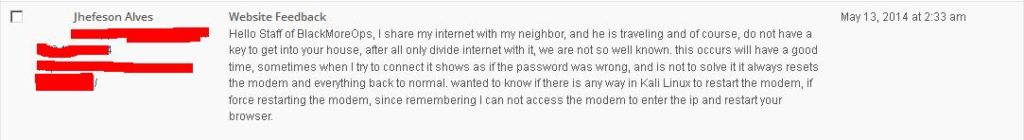
As you can see Jhefeson probably has a legitimate reason to try and reboot this shared router, but he can’t just because he doesn’t have physical access to it. If this guide works, he can actually get access back.
There’s many things you can do after you’ve got access to a router. You can change DNS settings, setup a tcpdump and later snoop all plaintext passwords using wireshark etc. If you know a friends, family. colleague or neighbor who didn’t change their routers default password, let them know of the risks.
But I am not here to judge whether it should be done or not, but this is definitely a way to gain access to a router. So hacking is not always bad, it sometime is required when you loose access or a system just wouldn’t respond. As a pentester, you should raise awareness. Share this guide as anyone who uses a Linux, Windows, Mac can use this guide to test their own network and fix ADSL router hack issue.

21 comments
well…why didn’t you explain the later part in detail like what to do when you get into the router. That would have made this tutorial a 5 star!
My thoughts were the same.
and why do you wanna know ya mo7taram example of what you can do is : fake dns , dns attack … etc mostly has to do with dns
come on nobody wants to leave the party soon what we can do if we hacked into a router I’m just curious to know
Because the author doesn’t know what they’re even doing with what they posted.
It is all taken fro mvery familiar sources I have read before.
all this work to say “change the default password”… nice article!
i am wondering what does the “-n” option does in nmap? i’ve googled it and didn’t come up with anything useful.
can you please explain what is the difference between DNS Resolver and DNS Resolution?
-n (No realizar resolución de nombres)
Le indica a Nmap que nunca debe realizar resolución DNS inversa de
las direcciones IP activas que encuentre. Ya que DNS es
generalmente lento, esto acelera un poco las cosas.
i don’t speak Spanish but i’v translated what you’v written, and now every thing makes since now :)
thanks.
-n (No realizar resolución de nombres)
Le indica a Nmap que nunca debe realizar resolución DNS inversa de
las direcciones IP activas que encuentre. Ya que DNS es
generalmente lento, esto acelera un poco las cosas.
The best way for jhefeson to restart the the router is to go to his neighbour outdoor main electric power supply trip it off, wait 3 minutes and switch it on it back, wait 5-10 minutes for the router to back online. Plus the fact is the neightbour is out of town. Don’t worry about blackout.
Sometimes you need to be creative, not everything can be solved from ur machine.
Hope u can inform that to jhefeson. Glad if that could help.
You could have used hydra to hack router pw
what i put in the user name and password box
Yeah it sounds very good but how can i use wireshark on this router?
Router have an public IP address like as 123.321.44.55
Ok i have access to the router
But how i can catch traffic and do MITM attacks on the user who is behind this router?
Router may be use NAT.
What to do
Pardon my ignorance, but where does the Nmap hacking part start? All you did was a scan for open ports/services on a network. If you want to know your home router’s IP, check the gateway on a client machine.
Great headline, but slightly dissapointing article.
Hello Tomas,
You got nmap scanning and saving IP in a file and hydra trying uname/passwd combination. I had to remove Hydra part that automates it.
No, you don’t really scan your own Gateway/Public IP. You can pick any IP range (/24) and scan it to see what’s in there. I happen to use an ADSL router so I scanned my Local ISP’s range. It was disappointing to see how many people mis-configured their home router. Cheers,
-BMO
Is it possible to do this type of attack with http-brute.nse script?
“For Ubuntu, Debian or aptitude based system”
apt is NOT apptitude
“rom man apt
apt(8) apt(8)
NAME
apt – Advanced Package Tool”
Get your facts right or don’t write articles pretending that you know things
apt isn’t apptitude
you’re using options that leak your real ip even through a proxy (ie sS)
you’re uselesly grepping tcpwrapped and open when you could just tell Nmap to only show ports that are open(–open)
You’re using timing(T5) that quite probably is too fast and going to make your results inaccurate depending on network conditions.
You obviously looked up all this information or just threw together some options after reading the help file.
You explain nothing about what the options actually do
You have no clue (or never mentioned) that ISP supplied modems and routers don’t normally have remote access enabled or even have the option to do so which makes this entire article and what you did in it a waste of time and useless.
I’ve put this as politley as I can.
It is really annoying when sites claim they are teacing something when all they are doing is showing people how to make noise on a network and leak machine id’s, IP,s, OS fingerprints, MAC’s, software version ID’s etc etc all over the place.
Not to mention DNS leaks and not one mention about not using your ISP default DNS servers.
And the encouragement to use a bloated prepackaged OS like Kali is not how people learn anything.
My system has a bad “apt-itude”. lol
bulshit.