I’m sure you bumped into situations where you needed to fake IP address in a capture file. This maybe required when you’re trying to send the capture file to someone that you don’t really share your real IP’s with or you just want to change cause you can. If you’ve tried this and looked around the interwebs, you’d surely know that there’s not many guides available and most people would just tell casually “just use sed” or use “WireEdit” and pay some fees for their license. Now, both works but I just got pissed off in a particular situation where sed wasn’t an options (the file was literally few GB’s in size and most text editors would just freeze) and to make things worse, I needed to filter a lot of info and only keep source and destination IP addresses in there for privacy’s sake. Yeah, that means removing all those noises like DNS, UDP, Broadcast, Cisco ARP, Broadcast, MDNS (yes, that too), SSDP … yes, pretty much anything except TCP/UDP, HTTP and TLS trarffic between my server and the destination server. So, in summary I had to filter all of these noises and change IP address in packet capture file to hide source IP address, this is similar to faking IP address in packet captures. You can also use other tools to do it on the fly but they require more setup and all I just wanted to do is to hide my source IP.
To make things easier for this guide, I will just use a browser and browse to https://www.blackmoreops.com. This would generate some TCP, HTTP and TLS traffic along with some other noises that I will filter in Wireshark and then change my workstation IP address (192.168.2.99) to Google DNS IP address (8.8.8.8).
(p.s. this is a super quick dump of the process, so excuse the typos)
Let’s begin:
Step1: Filter pcap for source and destination
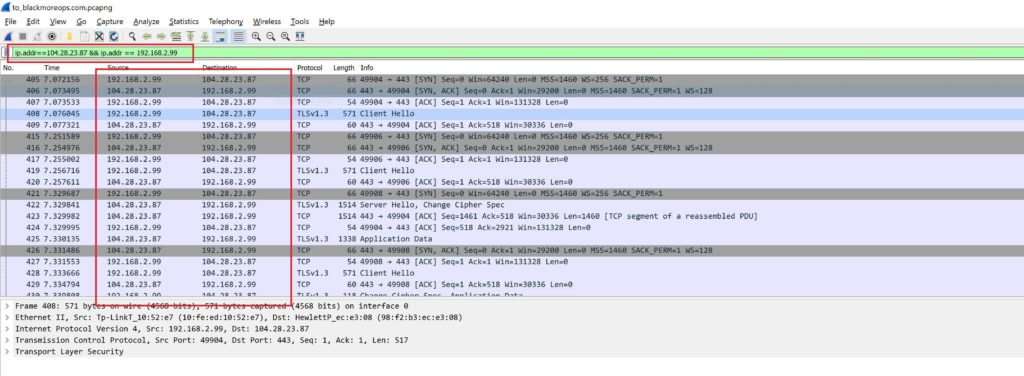
This is standard Wireshark filter. Simply filter for what you want to see in your pcap. In my case, it was IP address for https://www.blackmoreops.com and server.
ip.addr==104.28.23.87 && ip.addr == 192.168.2.99
It sort of looks like this in Wireshark!
As you can see, I’ve marked the IP filter and the source destination. I want to change my source IP 192.168.2.99 to something else here. I can very well change my destination IP address as well but let’s just keep it simple here.
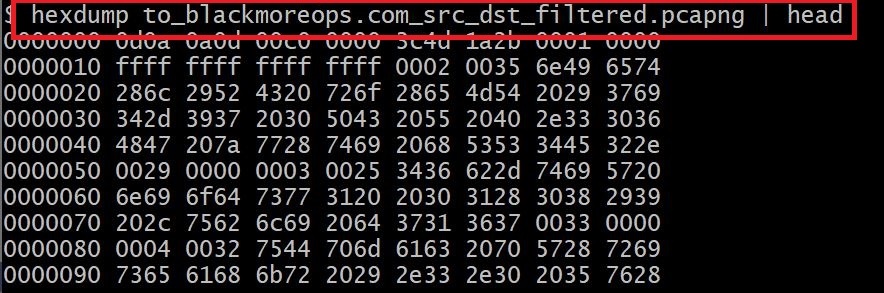
Step 2: hexdump the capture file
This is not really necessary but I wanted to show this so that you know what we’re dealing with here. hexdump is a standard Linux tool that shows the content of files in hex.
See all that 0000 and ffff etc, that’s hex values of different fields in hex.
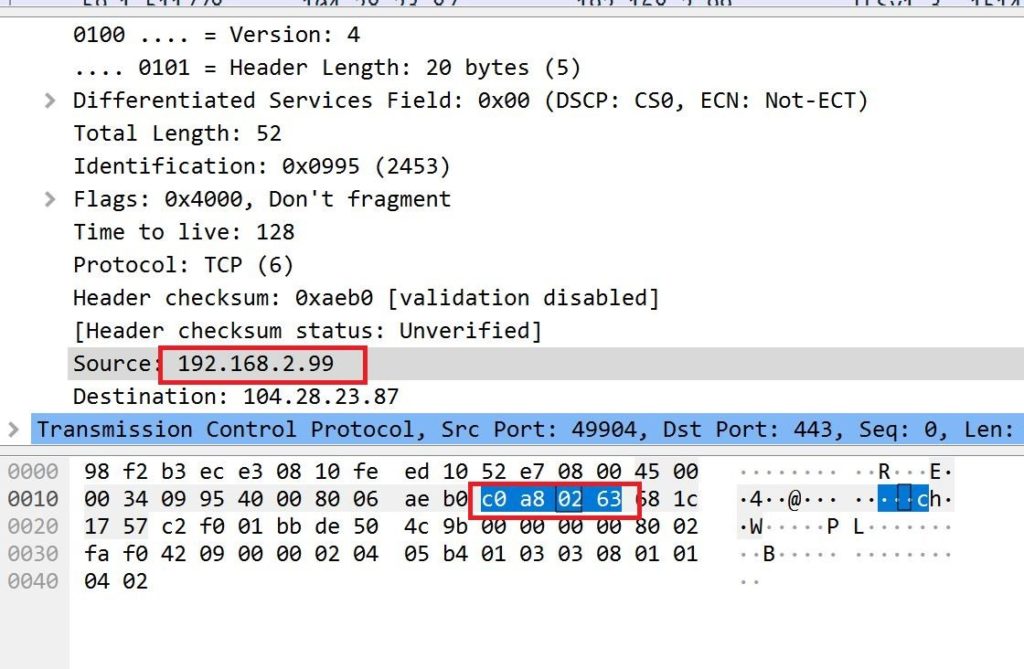
Step 3: Finding your IP to Hex value in capture file
I’m sure you already know how to find your own IP address in any machine but I just wanted to show this in the packet capture file and what it looks like.
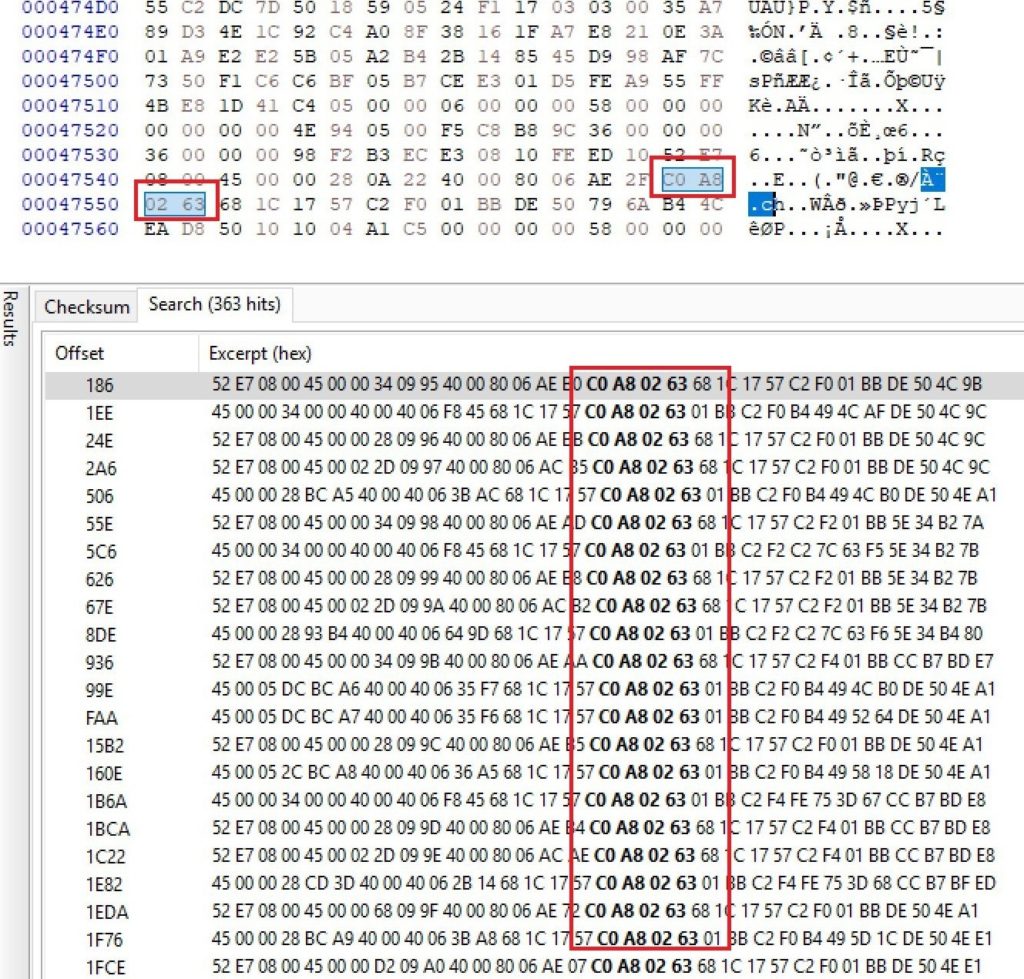
So, 192.168.2.99 is my private IP address on my server and in hex it’s C0 A8 02 63. I’ve showed it by highlighting Source: 192.168.2.99 in Wireshark which then highlights the Hex values.
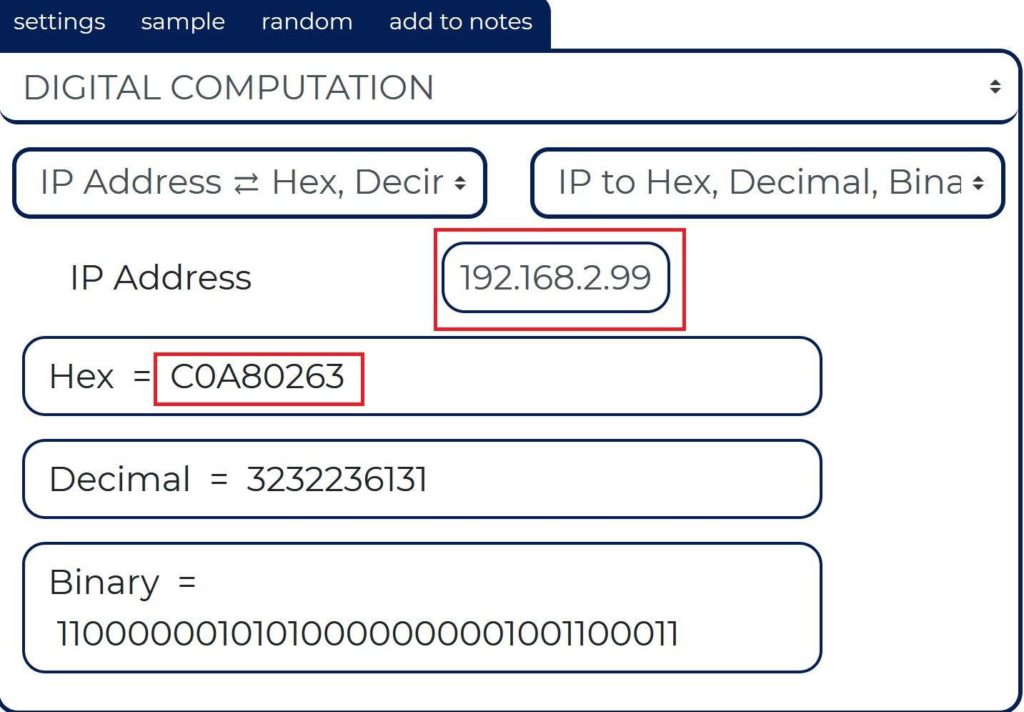
Step 4: Confirming your IP to Hex value in pcap file
Now that I can’t really translate IP to Hex on the fly (can you?) I decided to double check it in publicly available websites that has such tools i.e. https://ncalculators.com/digital-computation/ip-address-hex-decimal-binary.htm
This simply just proves that when we saw the Hex in packet capture, it was correct. We will use the same website to get Hex value for the fake IP address we want too.
Step 5: Confirming your IP to Hex value in pcap file
I use HxD which is a fast free hex editor that can open files of any size (up to 8EB), gives raw read/write access to disks and main memory (RAM), still being as easy to use as any text-editor. This solves multiple problems like text editors not being able to open large files, Hex values shown in too much gibberish format (HxD shows a nice format). HxD is a carefully designed and fast hex editor which, additionally to raw disk editing and modifying of main memory (RAM), handles files of any size. The easy to use interface offers features such as searching and replacing, exporting, checksums/digests, insertion of byte patterns, a file shredder, concatenation or splitting of files, statistics and much more.
Editing works like in a text editor with a focus on a simple and task-oriented operation, as such functions were streamlined to hide differences that are purely technical.
For example, drives and memory are presented similar to a file and are shown as a whole, in contrast to a sector/region-limited view that cuts off data which potentially belongs together. Drives and memory can be edited the same way as a regular file including support for undo. In addition memory-sections define a foldable region and inaccessible sections are hidden by default.
Furthermore a lot of effort was put into making operations fast and efficient, instead of forcing you to use specialized functions for technical reasons or arbitrarily limiting file sizes. This includes a responsive interface and progress indicators for lengthy operations. I like this tool and use it, you can use anything you want.
I used the portable English version for this exercise: https://mh-nexus.de/en/downloads.php?product=HxD20
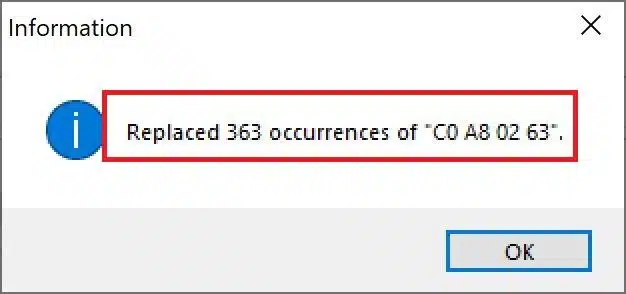
Simply open the capture file in HxD and search for C0 A8 02 63 (which is the IP address in Hex value). It finds it a total of 363 times (that matches with the captured pcap file I had).
Step 6: Choose your new fake IP address to Hex Value
Going back to https://ncalculators.com/digital-computation/ip-address-hex-decimal-binary.htm I simply put 8.8.8.8 as the IP address and it gave me Hex = 8080808.
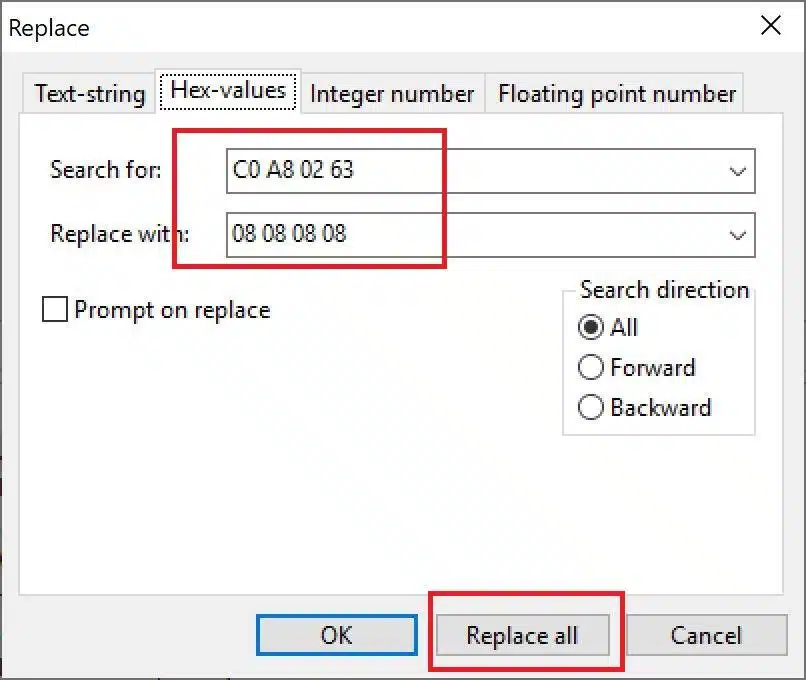
This is slightly incorrect as it didn’t add the preceding 0 in the Hex. 8.8.8.8 converted to Hex is actually 08080808 or 08 08 08 08 (sets of two characters in fours). We will now use 08 08 08 08 to replace 192.168.2.99 (Hex == C0 A8 02 63). If you’re not sure about this, simply use something like 230.130.30.3 (some random IP)
Step 7: Replacing IP address hex with new hex
Simply open HxD and search and replace:
Yeap, that easy really. Needs a bit of practicing when replacing long strings that breaks into multiple lines, but at the end, it’s as simple as that. Once you pressed "Replace all" it will give you something like this:
Save the file as a new file as .cap or .pcap or any Wireshark supported format. You might get few errors like out of bounds, simply ignore those.
Step 8: New pCAP file with fake IP address
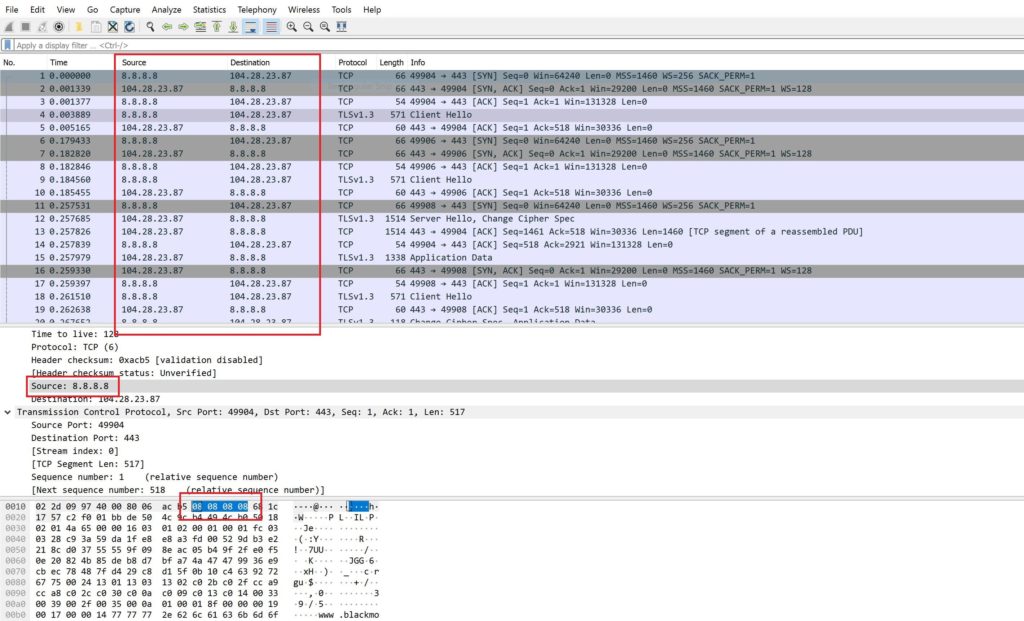
What good is a guide if you didn’t confirm it? lo and behold your new pcap file with fake ip
I’ve selected Source: 8.8.8.8 that highlights hex 08 08 08 08 in Wireshark.
Conclusion
Not that hard and can be done using many different tools. The practical use for such replacement is quite good. Obviously, in my case it was just to hide my server IP address but imagine if you captured network traffic when someone is trying to sign-in to a website and your pcap contains the cookie. You can edit the pcap file to change their machine IP to yours and use tcpreplay, Colasoft Packet Player or PlayCap to play the file again in your computer and suddenly you now have the cookie to sign-in! and of course this process can be used to do more that just that. Let me know how you’d do the steps above! Same tool or something better?


7 comments
I would also highly suggest making sure to mask the entire IP (as indicated in this post), I’ve seen some that only mask the first or last 2 octets. If you’re only doing a partial spoof, make sure to update the checksum (tampered or calculated). Here’s a PoC tool that can unmask IP’s given a valid checksum: https://github.com/XlogicX/tcpunmask
Supporting ToorCon talk: https://youtu.be/X5t1wVyof2I
Hi!
I would like to discuss with You the question of cooperation. Interested in placing a banner on Your site on a regular basis. The theme of the banner is mobile phones, gadgets. We work on an advance payment.
I will wait For your answer to my question. mail. Sincerely, Anna.
hey ya
Hi!
I would like to discuss with You the question of cooperation. Interested in placing a banner on Your site on a regular basis. The theme of the banner is mobile phones, gadgets. We work on an advance payment.
I will wait For your answer to my question. mail. Sincerely, Anna.
very interesting and helpful
is there any way to edit pcap files in mac laptop ? all the above options i could see only for windows
Any Hexeditor should do.