316
WPSeku is a black box WordPress vulnerability scanner that can be used to scan remote WordPress installations to find security issues.
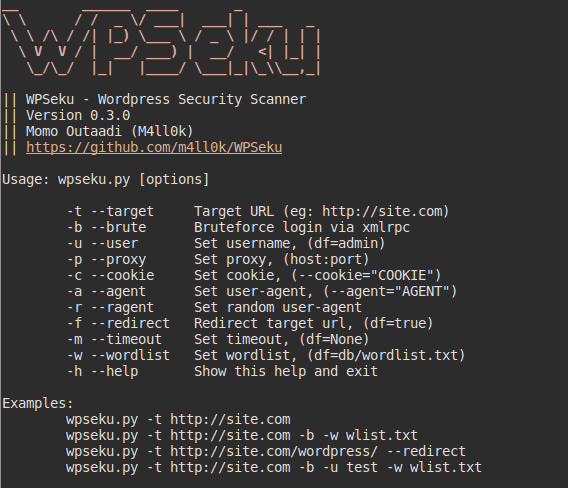
Table of Contents
Features of WPSeku WordPress Security Scanner
WPSeku supports various types of scanning including:
- Testing for XSS Vulnerabilities
- Testing for SQL Injection Vulnerabilities
- Testing for LFI Vulnerabilities
- Bruteforce login via xmlrpc
- Username Enumeration
- Proxy Support
- Method (GET/POST)
- Custom Wordlists
- Custom user-agent
It also uses the WPVulnDB Vulnerability Database API at https://wpvulndb.com/api.
Installation
$ git clone https://github.com/m4ll0k/WPSeku.git wpseku $ cd wpseku $ pip install -r requirements.txt $ python wpseku.py
Usage
python wpseku.py –target https://site.com –ragent
\ \ / / _ \/ ___| ___| | ___ _
\ \ /\ / /| |_) \___ \ / _ \ |/ / | | |
\ V V / | __/ ___) | __/ <| |_| |
\_/\_/ |_| |____/ \___|_|\_\\__,_|
|| WPSeku - Wordpress Security Scanner
|| Version 0.2.1
|| Momo Outaadi (M4ll0k)
|| https://github.com/m4ll0k/WPSeku
Usage: ./wpseku.py [--target|-t] https://localhost
-t --target Target URL (eg: https://localhost)
-x --xss Testing XSS vulns
-s --sql Testing SQL vulns
-l --lfi Testing LFI vulns
-q --query Testable parameters (eg: "id=1&test=1")
-b --brute Bruteforce login via xmlrpc
-u --user Set username, default=admin
-p --proxy Set proxy, (host:port)
-m --method Set method (GET/POST)
-c --cookie Set cookies
-w --wordlist Set wordlist
-a --agent Set user-agent
-r --redirect Redirect target url, default=True
-h --help Show this help and exit
Examples:
wpseku.py --target https://localhost
wpseku.py -t https://localhost/wp-admin/post.php -m GET -q "post=49&action=edit" [-x,-s,-l]
wpseku.py --target https://localhost --brute --wordlist dict.txt
wpseku.py --target https://localhost --brute --user test --wordlist dict.txt
Credits and Contributors
Original idea and script from WPScan Team (https://wpscan.org/)
WPScan Vulnerability Database (https://wpvulndb.com/api)
– Plecost – WordPress Fingerprinting Tool
– CMSmap – Content Management System Security Scanner
– WPScan – WordPress Vulnerability Scanner
You can download WPSeku here: WPSeku-master.zip
Or read more here.

