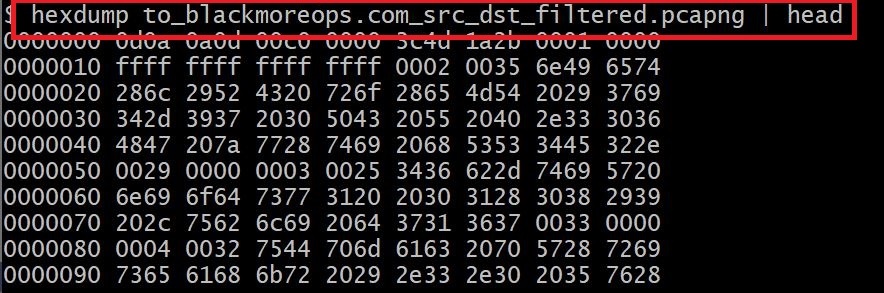
I’m sure you bumped into situations where you needed to fake IP address in a capture file. This maybe required when you’re trying to send the capture file to someone …
Traffic
-
HackingSecurity Related
Brute Force Attacks Conducted by Cyber Actors
by blackMOREOpsby blackMOREOpsIn a traditional brute-force attack, a malicious actor attempts to gain unauthorized access to a single account by guessing the password. This can quickly result in a targeted account getting …
-
HackingHow toLinuxSecurity Related
Avoiding Web Application Firewall using Python
by blackMOREOpsby blackMOREOpsWeb application firewalls are usually placed in front of the web server to filter the malicious traffic coming towards server. If you arehired as a penetration tester for some company …
-
HackingLinuxSecurity RelatedWindows
Using Rigorous Credential Control to Mitigate Trusted Network Exploitation
by blackMOREOpsby blackMOREOpsRecommended best practices for mitigating this threat include rigorous credential and privileged-access management, as well as remote-access control, and audits of legitimate remote-access logs. While these measures aim to prevent …
-
Security Related
What are the Challenges of Using Open Source Cybersecurity Tools?
by blackMOREOpsby blackMOREOpsBy making their source code freely available, developers of open source software rely on the power of the wider community in order to help them audit and improve their code. …