The Department of Homeland Security (DHS) National Cybersecurity and Communications Integration Center (NCCIC) and the Federal Bureau of Investigation (FBI) are issuing this activity alert to inform computer network defenders about SamSam ransomware, also known as MSIL/Samas.A. Specifically, this product shares analysis of vulnerabilities that cyber actors exploited to deploy this ransomware. In addition, this report provides recommendations for prevention and mitigation.
The SamSam actors targeted multiple industries, including some within critical infrastructure. Victims were located predominately in the United States, but also internationally. Network-wide infections against organizations are far more likely to garner large ransom payments than infections of individual systems. Organizations that provide essential functions have a critical need to resume operations quickly and are more likely to pay larger ransoms.
The actors exploit Windows servers to gain persistent access to a victim’s network and infect all reachable hosts. According to reporting from victims in early 2016, cyber actors used the JexBoss Exploit Kit to access vulnerable JBoss applications. Since mid-2016, FBI analysis of victims’ machines indicates that cyber actors use Remote Desktop Protocol (RDP) to gain persistent access to victims’ networks. Typically, actors either use brute force attacks or stolen login credentials. Detecting RDP intrusions can be challenging because the malware enters through an approved access point.
After gaining access to a particular network, the SamSam actors escalate privileges for administrator rights, drop malware onto the server, and run an executable file, all without victims’ action or authorization. While many ransomware campaigns rely on a victim completing an action, such as opening an email or visiting a compromised website, RDP allows cyber actors to infect victims with minimal detection.
Analysis of tools found on victims’ networks indicated that successful cyber actors purchased several of the stolen RDP credentials from known darknet marketplaces. FBI analysis of victims’ access logs revealed that the SamSam actors can infect a network within hours of purchasing the credentials. While remediating infected systems, several victims found suspicious activity on their networks unrelated to SamSam. This activity is a possible indicator that the victims’ credentials were stolen, sold on the darknet, and used for other illegal activity.
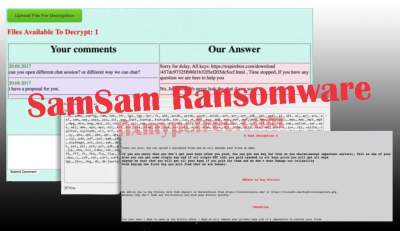
SamSam actors leave ransom notes on encrypted computers. These instructions direct victims to establish contact through a Tor hidden service site. After paying the ransom in Bitcoin and establishing contact, victims usually receive links to download cryptographic keys and tools to decrypt their network.