The word “hacking” has two definitions. The first definition refers to the hobby/profession of working with computers. The second definition refers to breaking into computer systems. While the first definition is older and is still used by many computer enthusiasts (who refer to cyber-criminals as “crackers”), the second definition is much more commonly used.
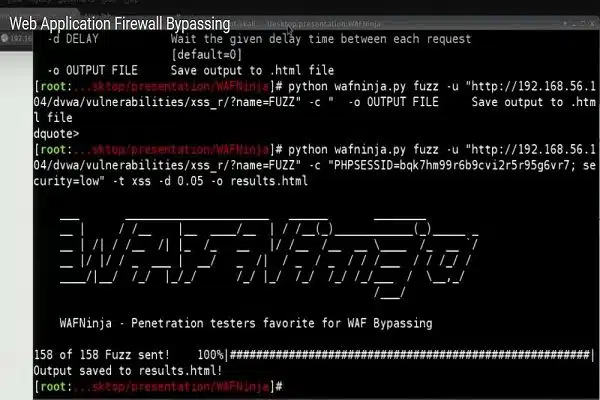
WAFNinja is a CLI python tool that helps penetration testers to bypass Web Application Firewall by automating steps necessary for bypassing input validation. WAFNinja supports HTTP connections, GET and POST requests and the use of Cookies in order to access pages restricted to authenticated users. It also supports intercepting proxy, so yes MITM for you.
The tool was created with the objective to be easily extendible, simple to use and usable in a team environment.
Supported web methods:
- HTTP connections
- GET requests
- POST requests
- Using Cookies (for pages behind auth)
- Intercepting proxy
Using WAFNinja for WAF Bypass
wafninja.py [-h] [-v] {fuzz, bypass, insert-fuzz, insert-bypass, set-db} ...
More examples
fuzzing
python wafninja.py fuzz -u "https://www.target.com/index.php?id=FUZZ" -c "phpsessid=value" -t xss -o output.html
Bypass WAG
python wafninja.py bypass -u "https://www.target.com/index.php" -p "Name=PAYLOAD&Submit=Submit" -c "phpsessid=value" -t xss -o output.html
Insert fuzz
python wafninja.py insert-fuzz -i select -e select -t sql
Video demo
Here a complete video of a workshop that will teach you how to attack an application secured by a WAF. The moderator describes WAF bypassing techniques and offers a systematic and practical approach on how to bypass web application firewalls based on these techniques. This video introduces WAFNinja, a tool that helps to find multiple vulnerabilities in firewalls.
Complete slides can be found here.