Setting up Damn Vulnerable Web App is essential for security professionals looking to develop their skills in a controlled environment. This comprehensive guide walks you through the complete DVWA setup process on Ubuntu, creating the perfect platform for learning web application security testing techniques.
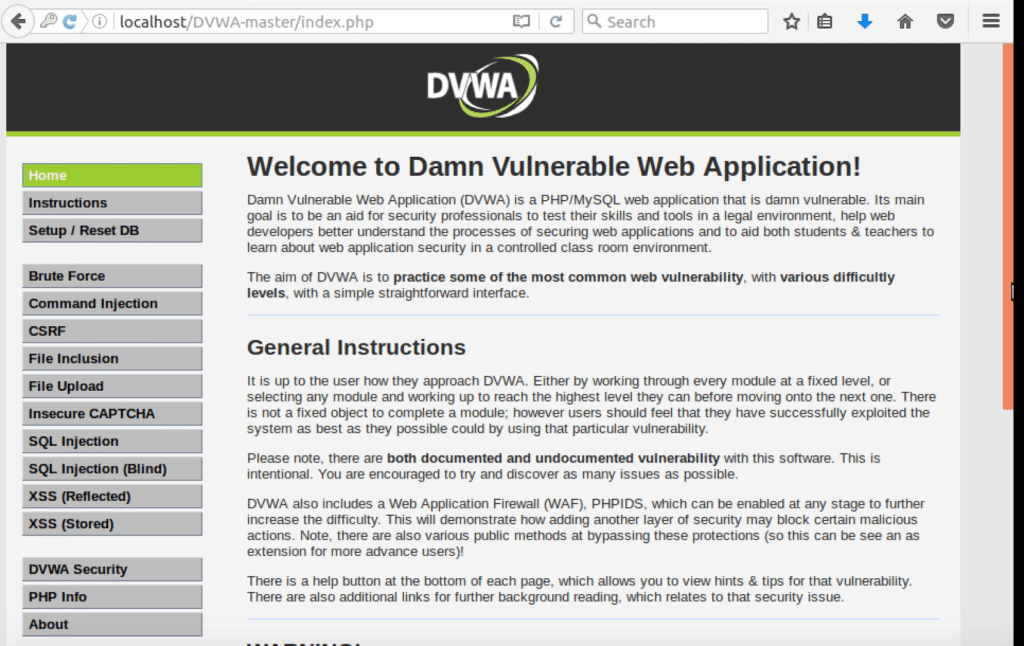
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is intentionally vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, help web developers better understand the processes of securing web applications, and aid teachers/students to teach/learn web application security in a classroom environment. In this tutorial, we will be installing Damn Vulnerable Web Application (DVWA) on an Ubuntu virtual machine.
Your DVWA setup will include an Ubuntu VM running the vulnerable application and a Kali Linux attacker machine. This configuration provides a realistic testing environment that mirrors real-world penetration testing scenarios while maintaining complete isolation from production systems.
Table of Contents
Prerequisites for Your Damn Vulnerable Web App Setup
Before beginning your Damn Vulnerable Web App setup, ensure you have the following components ready:
- Ubuntu 22.04 LTS (recommended for stability)
- Kali Linux 2024.1 (latest rolling release)
- Basic Linux knowledge and familiarity with command-line operations
- Virtual machine software (VirtualBox, VMware, or similar)
- Minimum 4GB RAM allocated to each virtual machine
- 20GB storage space for each VM
Understanding virtual machines and basic networking concepts is crucial for successfully setting up DVWA. If you’re new to these concepts, spend time familiarising yourself with VM management and Linux fundamentals before proceeding.
Installing DVWA for Your Penetration Testing Lab
Step 1: Download Damn Vulnerable Web App
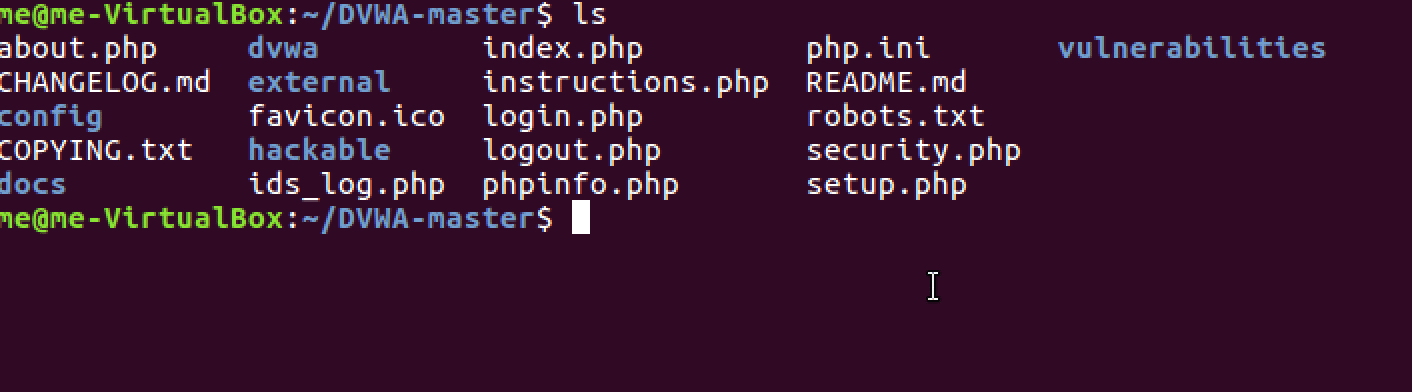
Navigate to the official DVWA GitHub repository and download the latest version. The GitHub repository is now the primary source for DVWA updates and contains the most current version with security patches and new features.
Extract the downloaded archive and examine the documentation in the docs folder. The documentation provides valuable insights into setting up DVWA correctly.
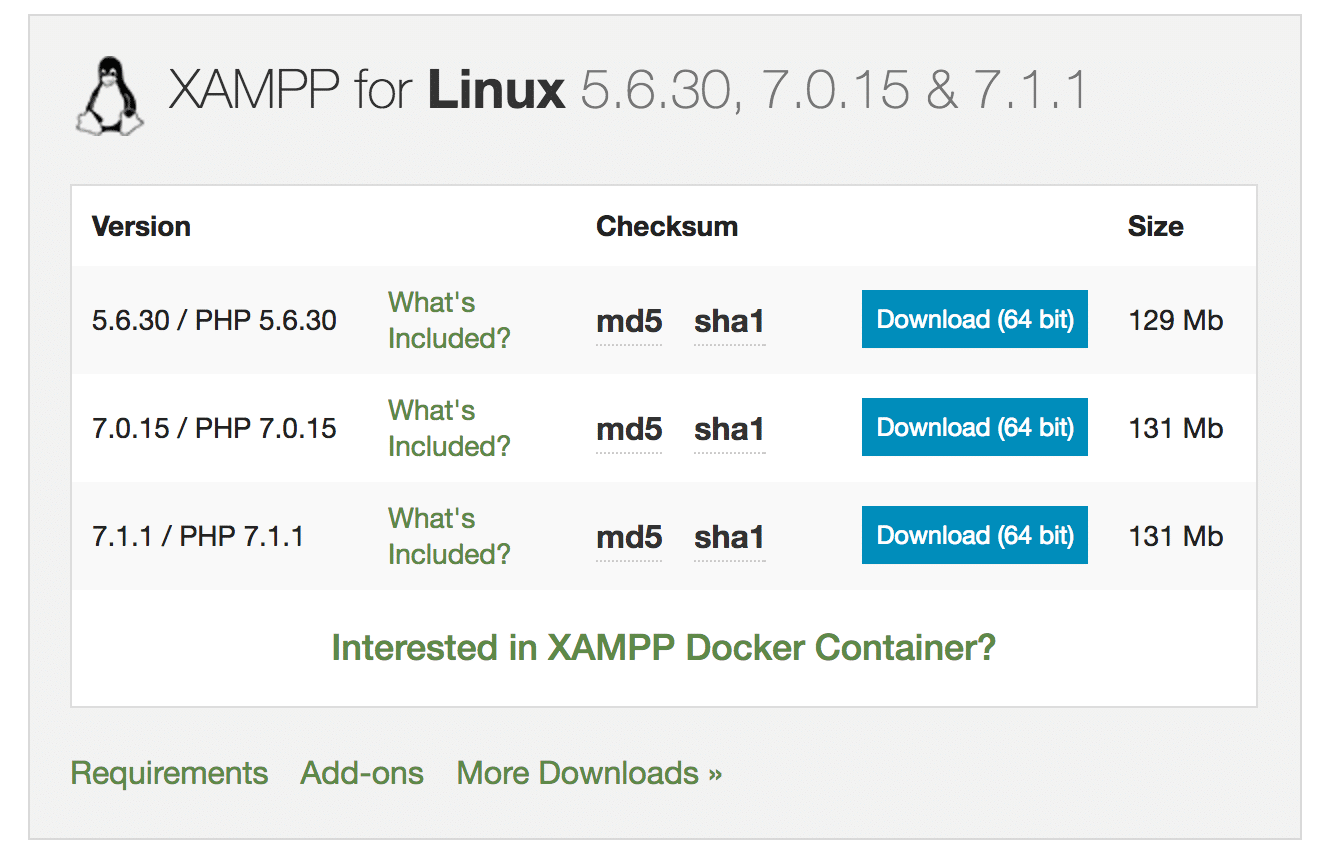
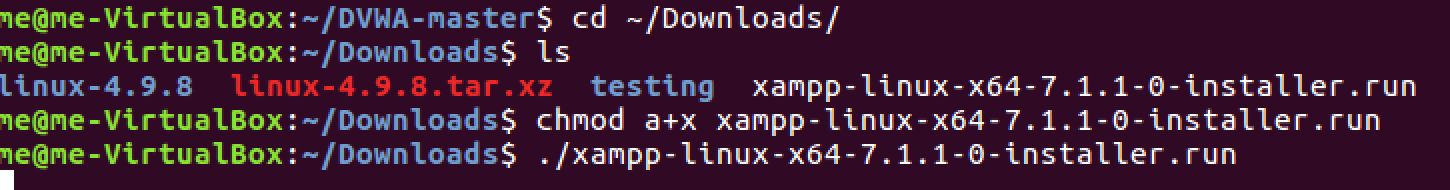
Step 2: Install XAMPP for Your DVWA Setup
Download the latest XAMPP package for Linux. As of 2025, XAMPP 8.2.12 is the current stable version, offering improved PHP 8.2 support and enhanced security features for your vulnerable web application pentest lab.
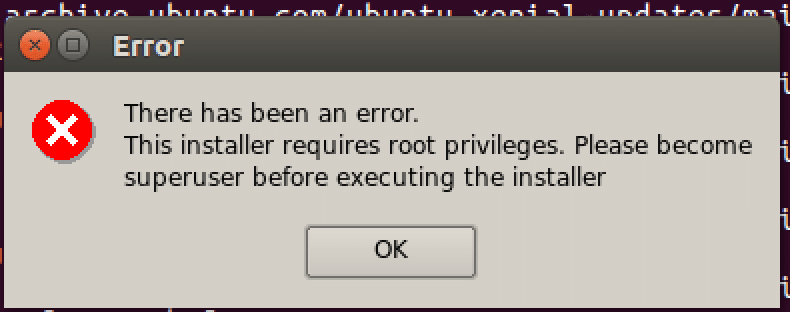
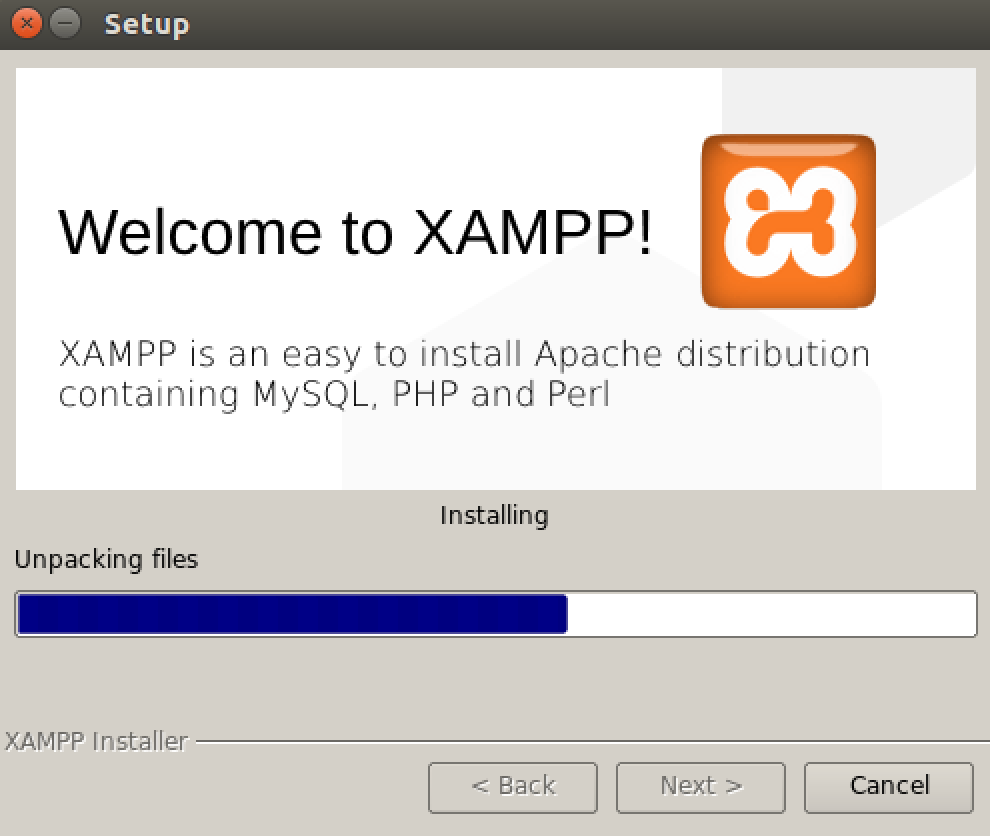
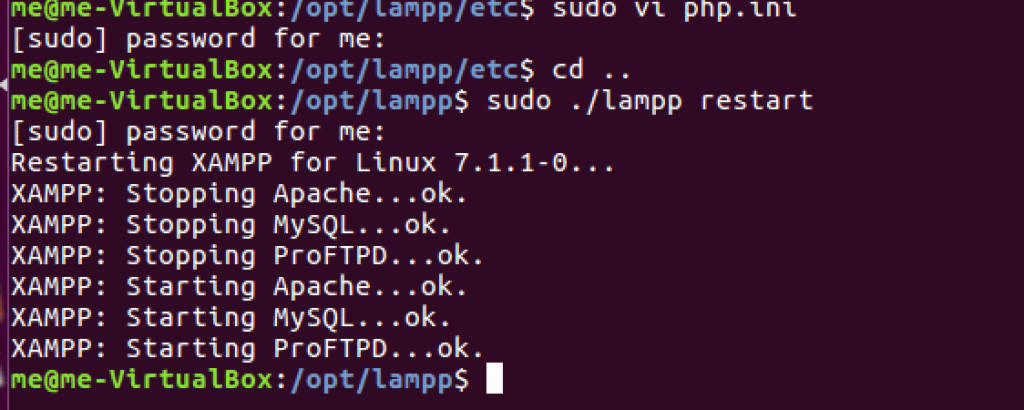
Remember to run the XAMPP installer with root privileges to ensure proper installation in your web application pentesting lab setup environment.
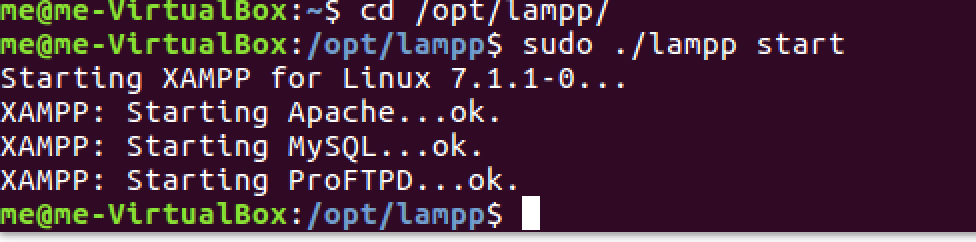
Start the XAMPP server using the command /opt/lampp/lampp start. This initialises all necessary services for your DVWA setup.
Verify your installation by navigating to localhost or 127.0.0.1 in your web browser. A successful installation displays the XAMPP welcome page.
Step 3: Deploy DVWA in Your Penetration Testing Lab
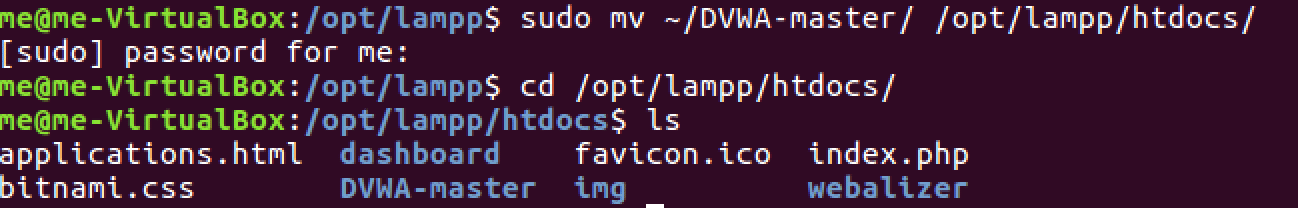
Move the DVWA folder to the XAMPP htdocs directory to make it accessible through your web server. This step integrates the vulnerable application into your penetration testing lab infrastructure.
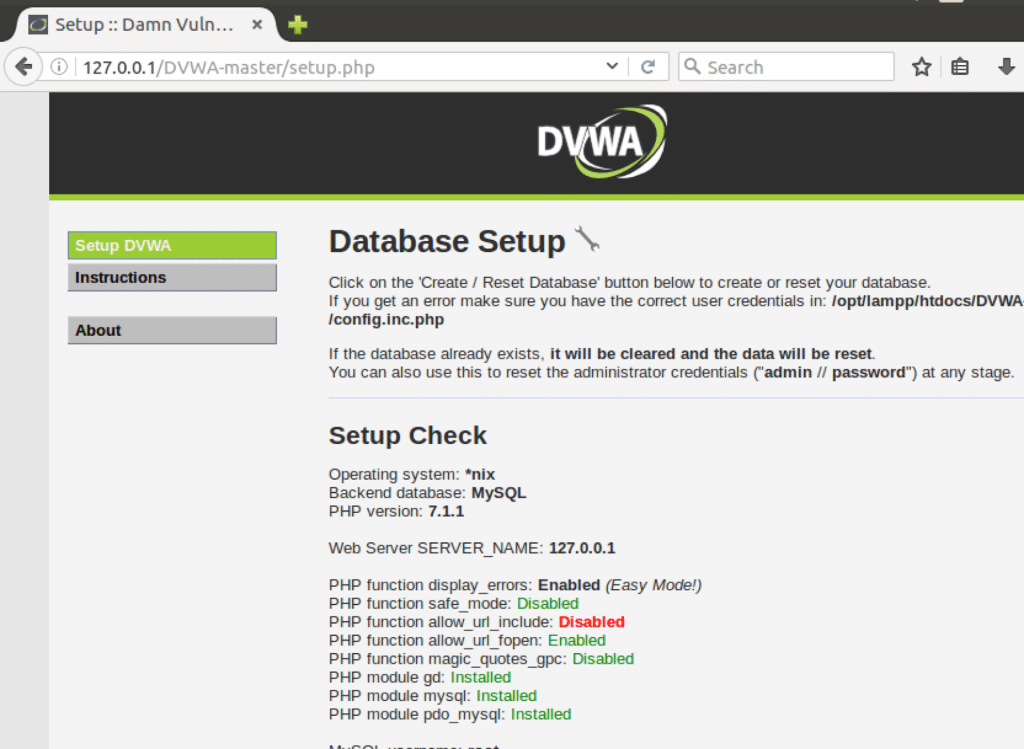
Access localhost/DVWA-master to confirm your setting up DVWA is functioning correctly.
Quick Setup Commands for Your Damn Vulnerable Web App Installation
For experienced users, here are the essential commands to rapidly configure your DVWA setup:
# Download and install XAMPP
cd ~/Downloads
chmod a+x xampp-linux-x64-8.2.12-0-installer.run
sudo ./xampp-linux-x64-8.2.12-0-installer.run
# Clone DVWA from GitHub (recommended method)
git clone https://github.com/digininja/DVWA.git
sudo mv DVWA/ /opt/lampp/htdocs/
# Start XAMPP services
sudo /opt/lampp/lampp startConfiguring DVWA for Optimal Performance
Database Configuration
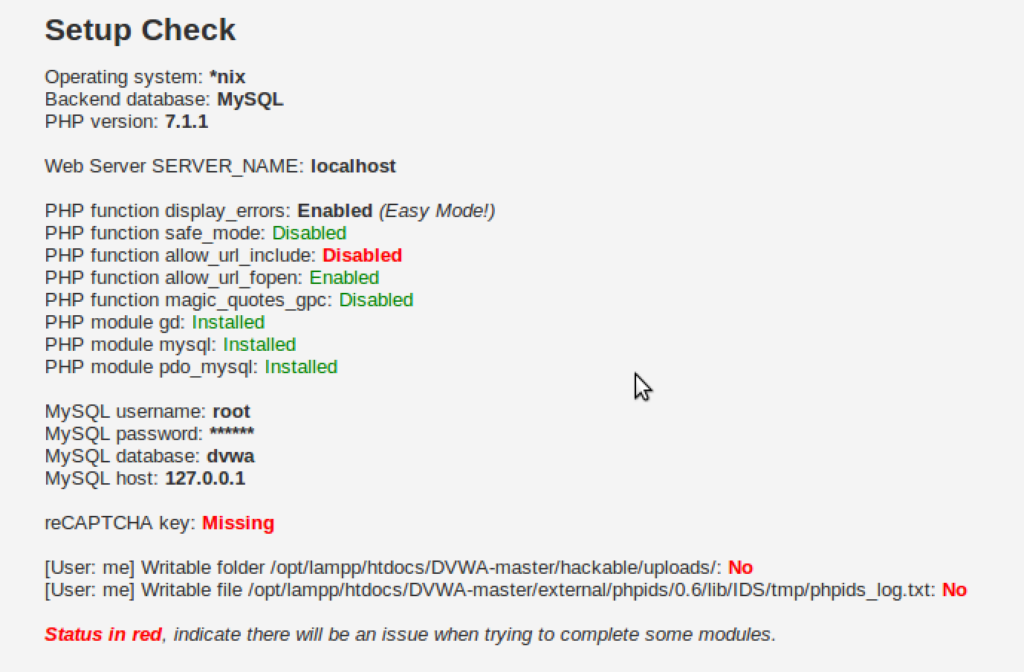
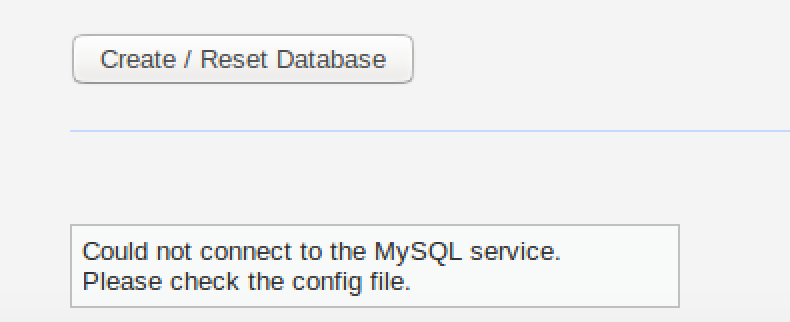
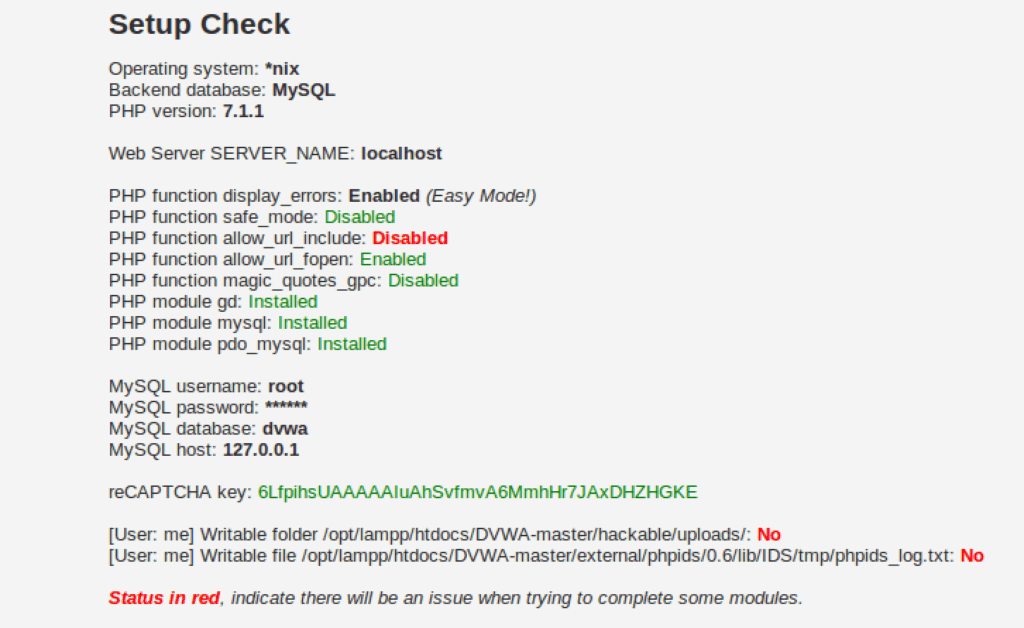
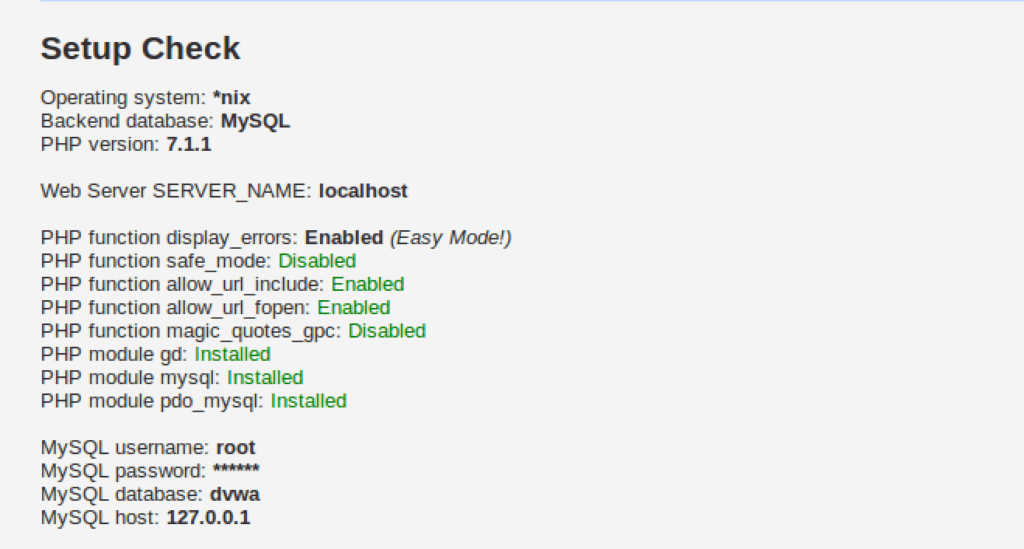
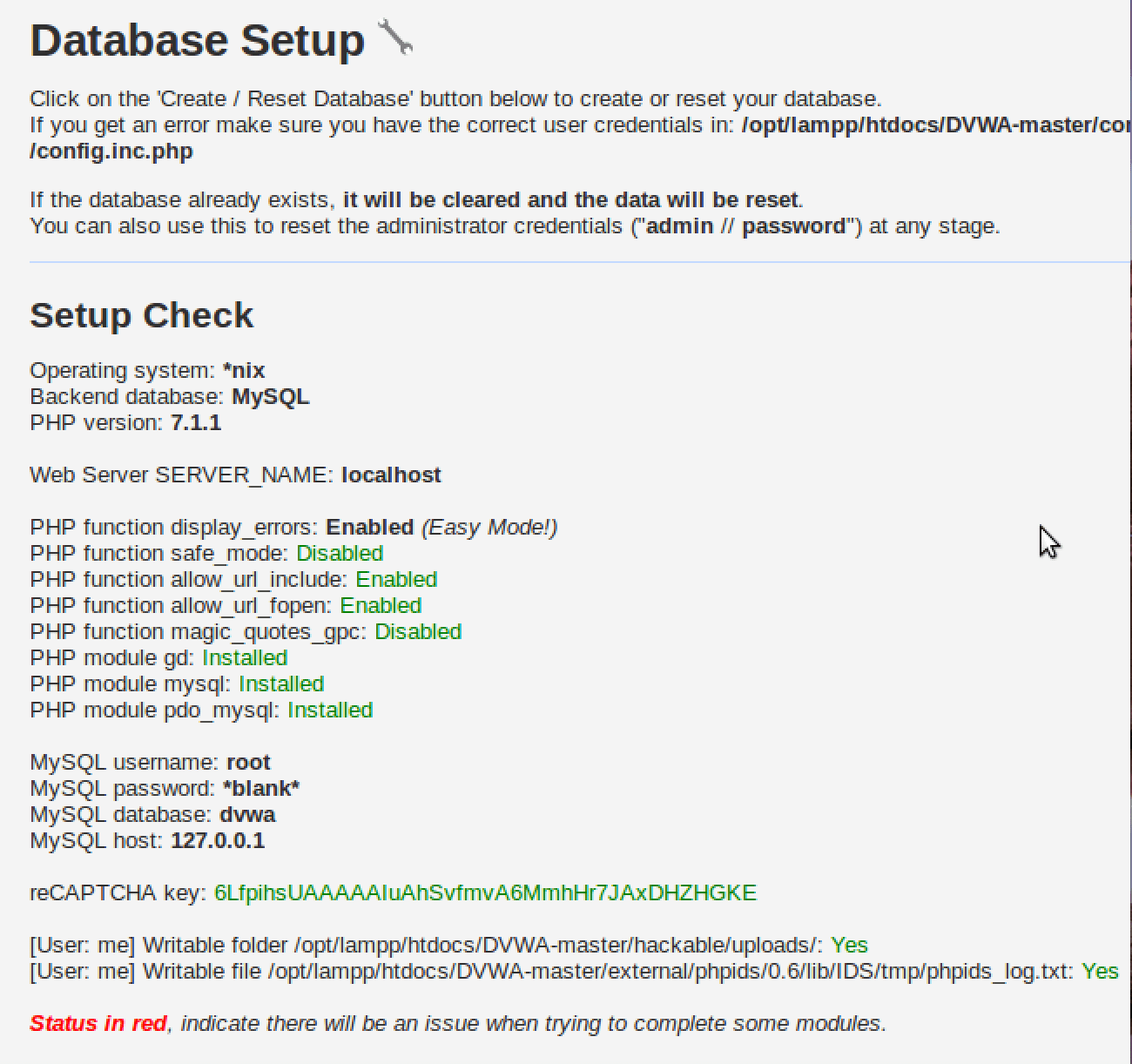
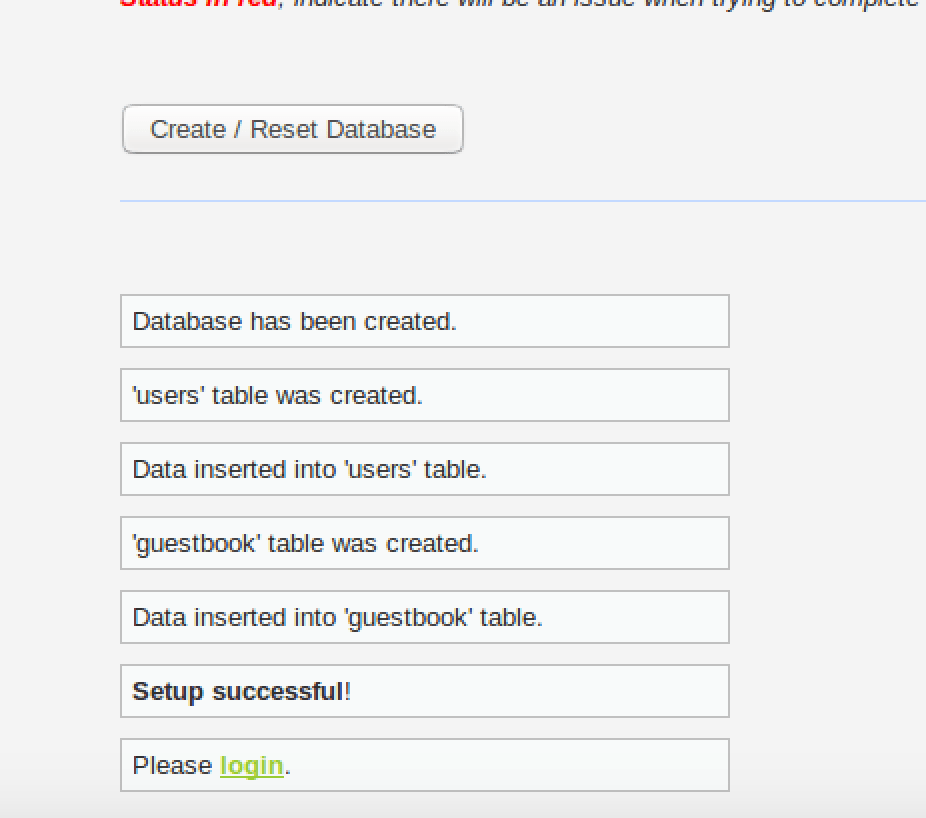
Navigate to the DVWA setup page where you’ll see configuration issues highlighted in red. These require attention to ensure your DVWA setup functions properly.
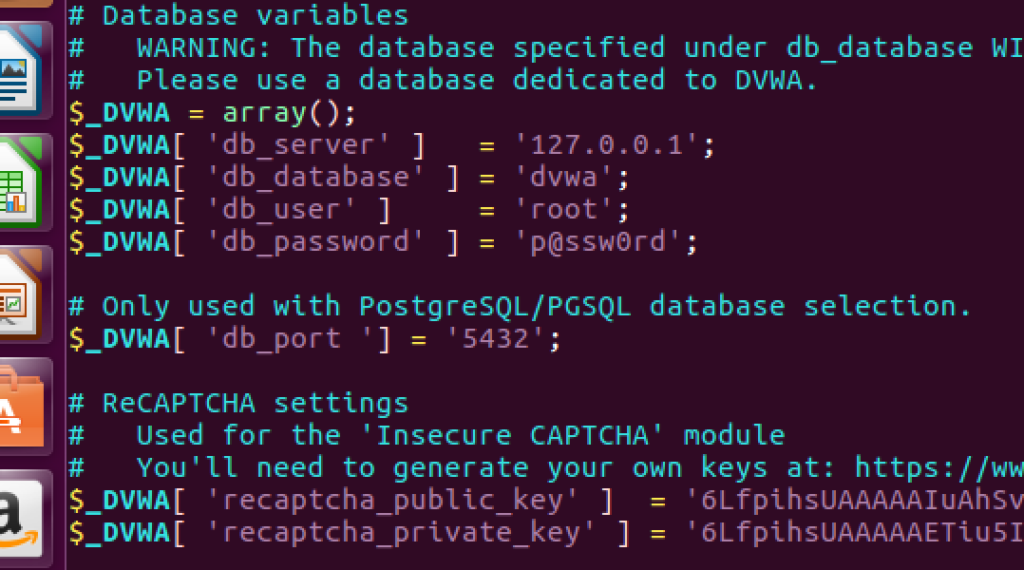
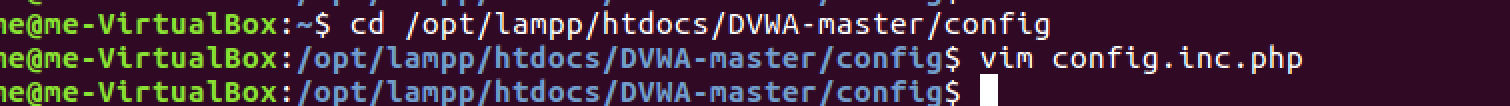
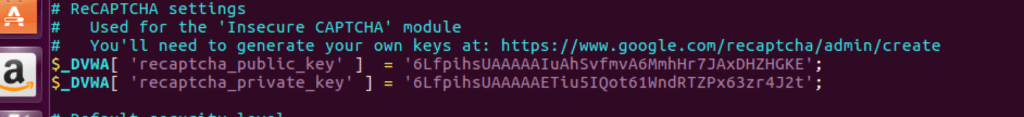
Edit the database configuration file located at /opt/lampp/htdocs/DVWA/config/config.inc.php. Update the database credentials to match your MySQL setup:
For default XAMPP installations, change the password from ‘p@ssw0rd’ to an empty string (”). This resolves the database connection issue in your Damn Vulnerable Web App setup.
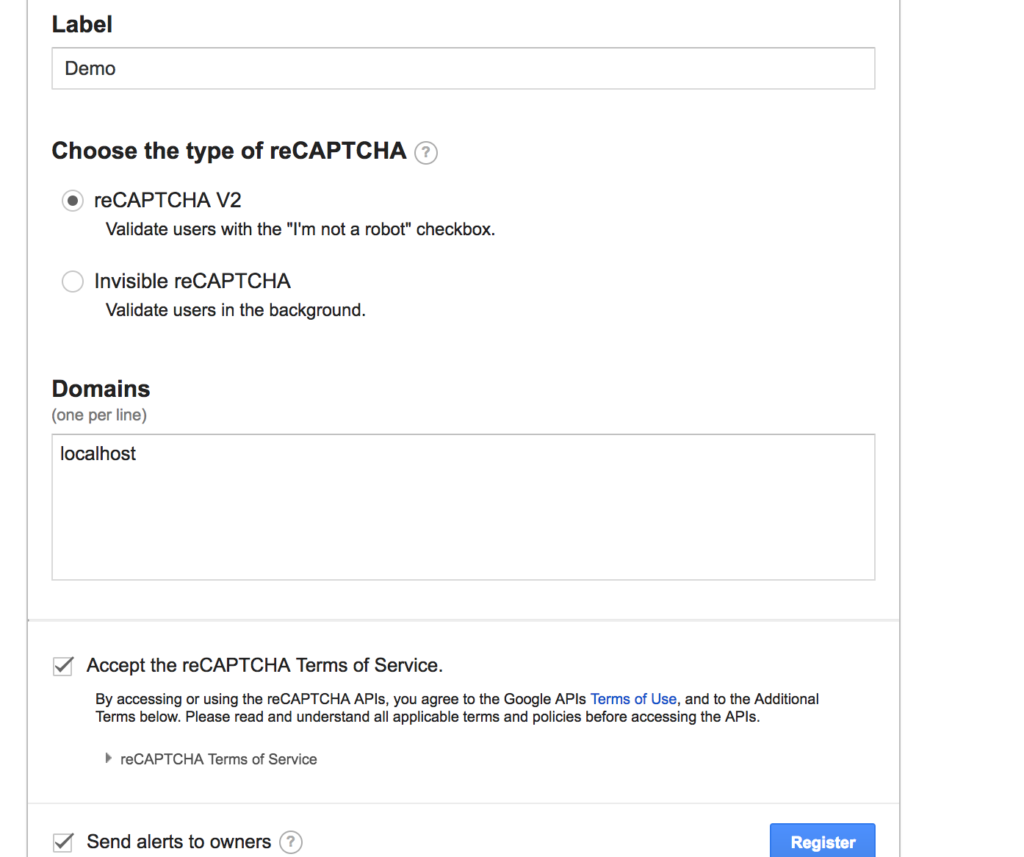
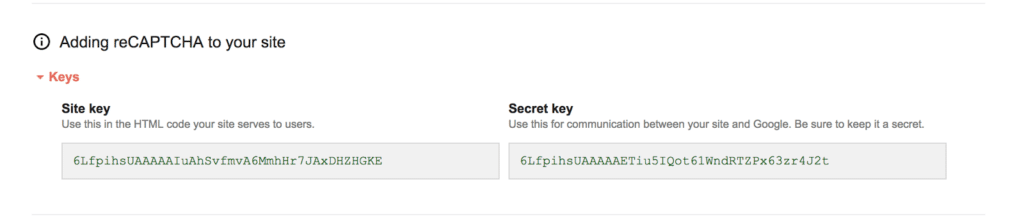
ReCAPTCHA Configuration
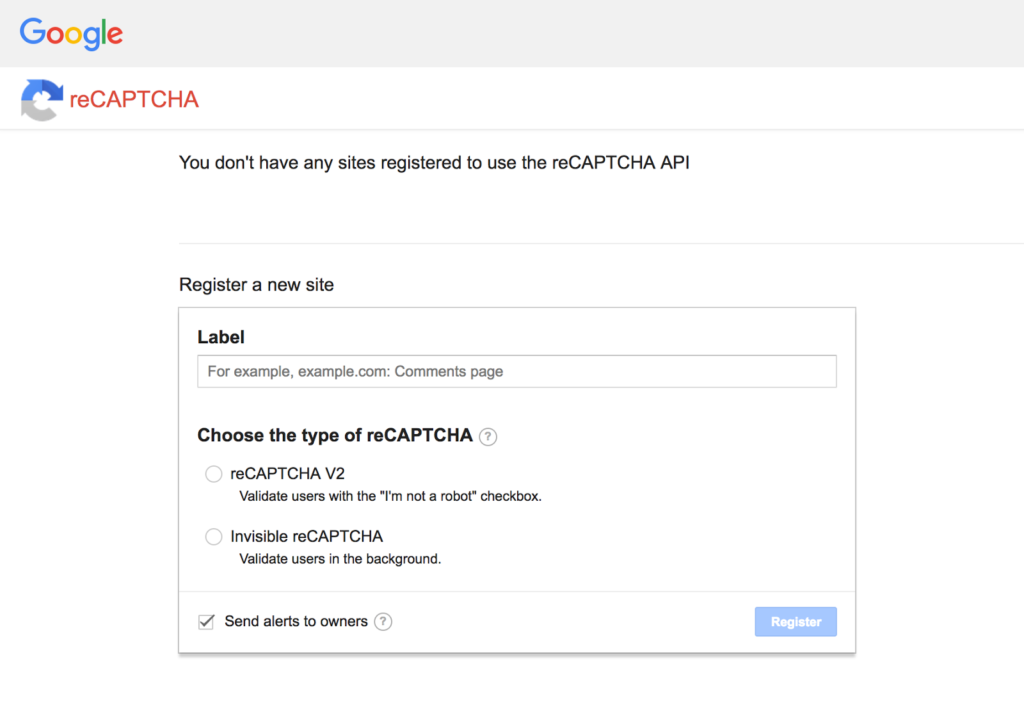
Configure reCAPTCHA for your vulnerable web application pentest lab by visiting the Google reCAPTCHA Admin Console.
Add the generated keys to your DVWA configuration file to enable reCAPTCHA functionality in your setting up DVWA process.
PHP Configuration for Enhanced Lab Security
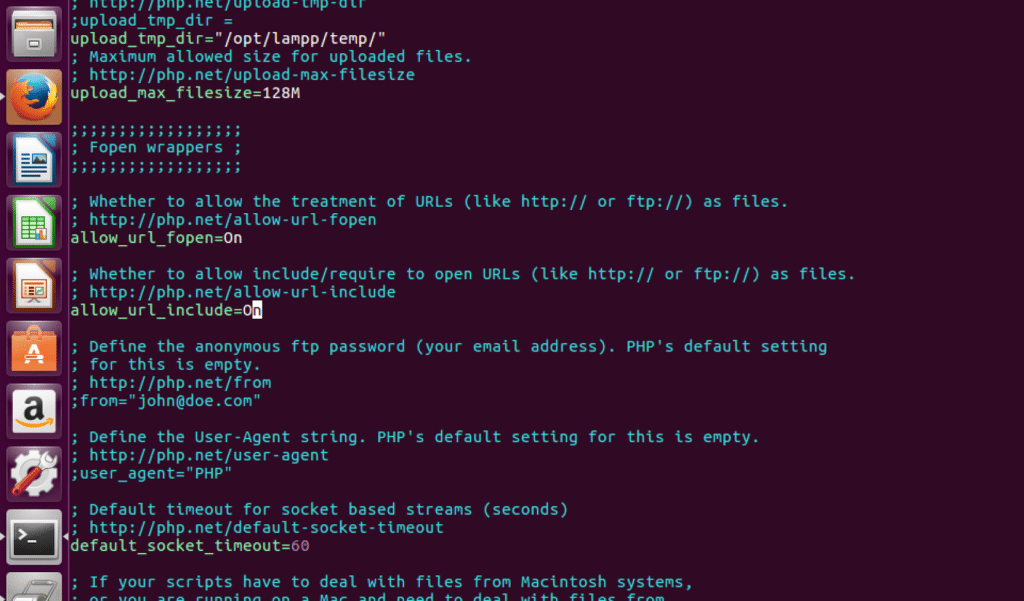
Modify the PHP configuration file at /opt/lampp/etc/php.ini to enable specific functions required by your DVWA setup:
Enable allow_url_include by changing the value from Off to On. This setting is crucial for certain DVWA vulnerabilities to function correctly in your penetration testing lab.
Restart XAMPP services after making configuration changes to ensure your vulnerable web application pentest lab operates with the updated settings.
File Permissions and Final Configuration
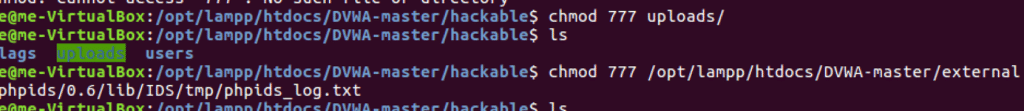
Set appropriate file permissions for the DVWA directories to ensure proper functionality:
sudo chmod 777 /opt/lampp/htdocs/DVWA/hackable/uploads/
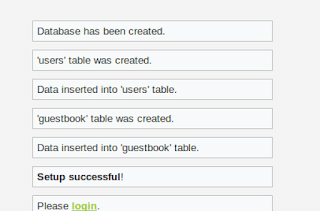
sudo chmod 777 /opt/lampp/htdocs/DVWA/external/phpids/0.6/lib/IDS/tmp/phpids_log.txtOnce all configuration issues are resolved, you’ll see green status indicators, confirming your Setup Damn Vulnerable Web App process is complete and properly configured.
Modern DVWA Setup Best Practices
Docker Alternative for Advanced Users
For a more isolated and reproducible DVWA setup environment, consider using the official DVWA Docker container:
docker run --rm -it -p 80:80 vulnerables/web-dvwaThis approach provides better isolation and easier deployment across different systems in your setting up DVWA process.
Security Considerations for Your Lab Environment
When setting up DVWA, remember these security practices:
- Network Isolation: Ensure your lab VMs are isolated from production networks
- Snapshot Management: Create VM snapshots before major configuration changes
- Regular Updates: Keep your base systems updated while maintaining vulnerable applications
- Documentation: Document all configurations for consistent lab reproduction
Integration with Modern Pentesting Tools
Your DVWA setup can integrate with contemporary security tools:
- Burp Suite Professional for comprehensive web application testing
- OWASP ZAP for automated vulnerability scanning
- SQLMap for database exploitation testing
- Nikto for web server vulnerability assessment
Troubleshooting Your Damn Vulnerable Web App Installation
Common Issues and Solutions
Database Connection Problems: Verify MySQL credentials in the configuration file and ensure the MySQL service is running.
Permission Errors: Check file ownership and permissions, particularly for upload directories and log files.
PHP Module Issues: Install missing PHP modules using your system’s package manager or enable them in php.ini.
Network Connectivity: Ensure VM network settings allow communication between your attacker and target machines.
Advanced Damn Vulnerable Web App Setup Features
Custom Vulnerability Scenarios
Extend your DVWA setup by creating custom vulnerable applications or modifying existing DVWA challenges. This approach provides targeted practice for specific vulnerability types.
Automated Testing Integration
Integrate automated vulnerability scanners into your setting up DVWA workflow to compare manual and automated testing results, enhancing your understanding of tool capabilities and limitations.
Conclusion
Successfully setting up Damn Vulnerable Web App provides a solid foundation for learning and practising web application security testing. This controlled environment allows you to develop crucial pentesting skills while maintaining ethical boundaries and legal compliance.
Your DVWA setup serves as a stepping stone to more advanced security challenges and real-world penetration testing scenarios. Regular practice in this environment builds the expertise necessary for professional security assessments and helps maintain current knowledge of evolving web application vulnerabilities.
WebGoat: https://owasp.org/www-project-webgoat/
- OWASP’s official WebGoat project page
- GitHub repository: https://github.com/WebGoat/WebGoat
bWAPP (buggy Web Application): http://www.itsecgames.com/
- Official bWAPP website by Malik Mesellem
- Download page: http://www.itsecgames.com/download.htm
Mutillidae: https://github.com/webpwnized/mutillidae
- OWASP Mutillidae II project on GitHub
VulnHub: https://www.vulnhub.com/
- Collection of vulnerable VMs for practice
TryHackMe: https://tryhackme.com/
- Online platform with vulnerable web applications
Hack The Box: https://www.hackthebox.com/
- Platform with various vulnerable applications and machines
Continue expanding your vulnerable web application pentest lab by incorporating additional vulnerable applications like above that reflect modern web development frameworks and technologies. This comprehensive approach ensures your skills remain relevant in the constantly evolving cybersecurity landscape. In addition, check these links for more resources: