AI powered cybersecurity solutions have revolutionised how organisations protect themselves against evolving cyber threats across all deployment environments. These intelligent platforms leverage machine learning algorithms, behavioural analytics, and automated response capabilities to detect, prevent, and mitigate security incidents faster than traditional methods. Whether deployed on-premise, in hybrid configurations, pure cloud, hybrid multicloud, or air-gapped environments, AI powered cybersecurity solutions provide the advanced protection modern enterprises need to safeguard their digital assets and maintain operational resilience.
Table of Contents
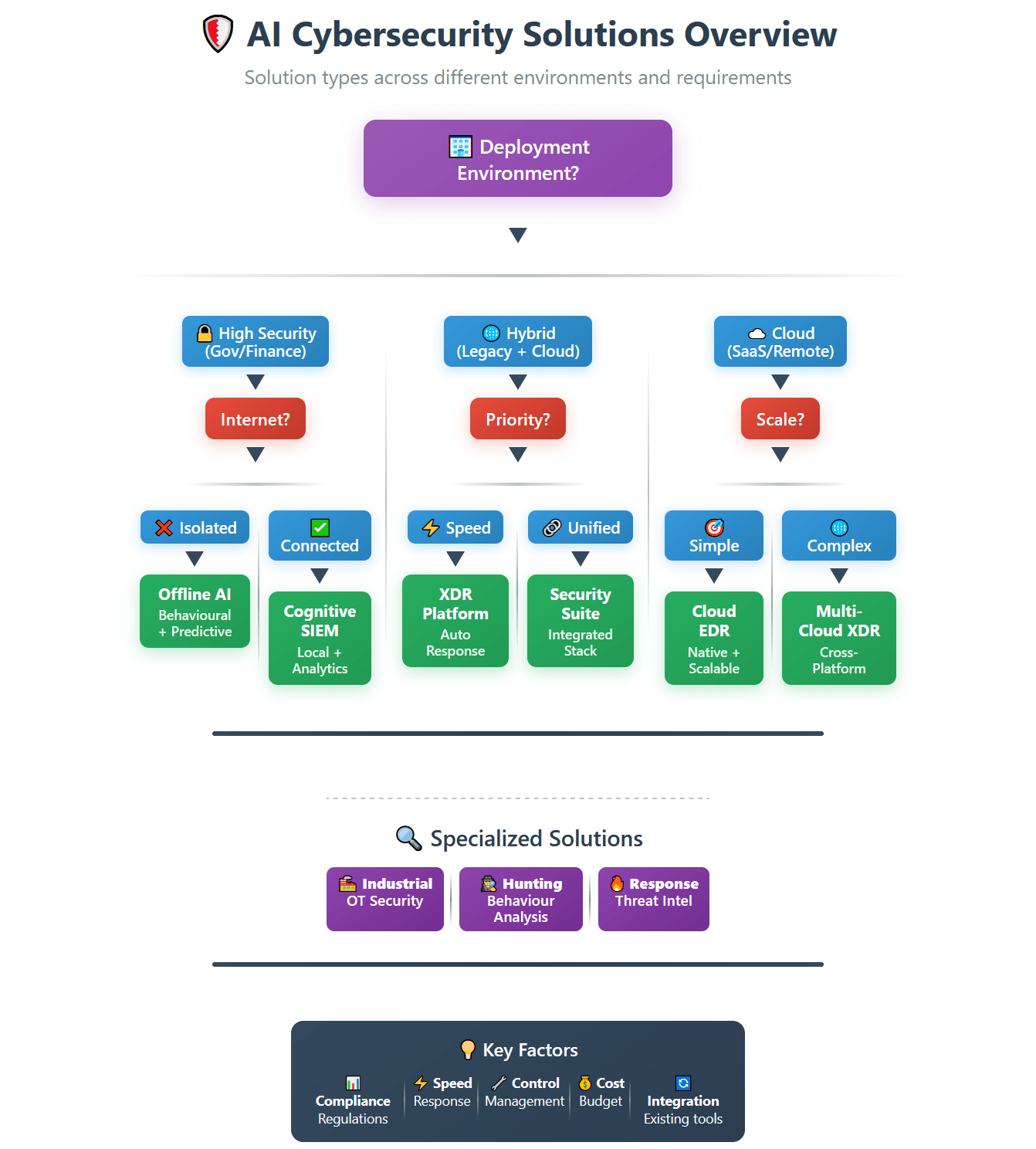
AI Cybersecurity Deployment Models and Use Cases
The flexibility of modern AI powered cybersecurity solutions enables deployment across various infrastructure configurations. Each deployment model offers unique advantages for different organisational requirements and security postures.
| Deployment Model | Best Use Cases | Key Benefits | Ideal For |
|---|---|---|---|
| On-Premise | Financial institutions, government agencies, healthcare with strict compliance | Complete data control, regulatory compliance, low latency | Organisations with strict data sovereignty requirements |
| Hybrid | Enterprises with legacy systems and cloud adoption, manufacturing with OT/IT convergence | Balanced security across environments, gradual cloud migration | Companies transitioning to cloud while maintaining critical on-premise assets |
| Cloud | SaaS companies, startups, remote-first organisations | Rapid deployment, automatic updates, scalability | Organisations with cloud-native operations and distributed workforces |
| Hybrid Multicloud | Large enterprises, global corporations, disaster recovery focused | Vendor diversification, global presence, enhanced resilience | Multinational corporations requiring geographic data distribution |
| Air-Gapped | Critical infrastructure, security contractors, nuclear facilities | Maximum isolation, protection against network-based attacks | High-security environments with classified or extremely sensitive data |
Leading AI Cybersecurity Platforms
CrowdStrike Falcon Platform
CrowdStrike’s Falcon platform represents one of the most advanced AI powered cybersecurity solutions available today, built on a cloud-native architecture that fundamentally transforms endpoint security. The platform uses machine learning to analyse billions of events across endpoints, providing real-time threat detection and response capabilities that adapt to emerging attack vectors. Falcon’s cloud-native design enables instant deployment for cloud and hybrid environments whilst offering comprehensive management capabilities for organisations requiring local data processing.
The platform’s AI engine processes over 5 trillion events weekly, creating a continuously evolving threat intelligence database that benefits all customers. For hybrid multicloud environments, Falcon provides unified visibility across AWS, Azure, Google Cloud, and private cloud infrastructures. The platform’s OverWatch managed threat hunting service extends AI capabilities with human expertise, particularly valuable for air-gapped environments requiring periodic security assessments.
Falcon’s next-generation antivirus (NGAV) capabilities combine signature-based detection with behavioural analysis and machine learning models that can identify previously unknown threats. The platform’s Identity Protection module extends AI powered cybersecurity solutions beyond endpoints to include identity and access management, providing comprehensive protection across modern attack surfaces.
Darktrace Enterprise Immune System
Darktrace pioneered the use of unsupervised machine learning in cybersecurity through its Enterprise Immune System, creating one of the most innovative AI powered cybersecurity solutions available. The platform learns normal behaviour patterns across networks, devices, users, and applications, then identifies anomalies that could indicate threats without relying on pre-defined signatures or rules. This approach proves particularly effective in detecting sophisticated attacks that attempt to blend in with normal network traffic.
The platform adapts seamlessly across deployment environments, from on-premise installations in sensitive government facilities to hybrid configurations protecting financial institutions’ distributed infrastructure. For cloud environments, Darktrace provides native integration with major cloud service providers whilst maintaining the same unsupervised learning capabilities that make it effective in traditional network environments.
Darktrace’s Autonomous Response technology represents a significant advancement in AI powered cybersecurity solutions, capable of taking immediate action to neutralise threats whilst maintaining business operations. The platform’s AI algorithms can distinguish between legitimate business activities and malicious behaviour, enabling it to respond proportionally to different threat levels. For air-gapped networks, Darktrace offers standalone deployment options with periodic offline updates, maintaining effectiveness even in completely isolated environments.
The platform’s Industrial Immune System extends protection to operational technology environments, making it particularly valuable for manufacturing, energy, and critical infrastructure organisations operating hybrid IT/OT networks. This specialisation addresses the unique challenges of protecting industrial control systems whilst maintaining operational continuity.
SentinelOne Singularity Platform
The SentinelOne Singularity platform combines AI-driven threat detection with automated incident response across all deployment models, representing a comprehensive approach to AI powered cybersecurity solutions. The platform provides endpoint detection and response (EDR), extended detection and response (XDR), and cloud security capabilities through a unified console that simplifies security management across diverse environments.
SentinelOne’s behavioural AI engine utilises static analysis, behavioural analysis, and machine learning models that can predict and prevent both known and unknown threats across multiple attack vectors. The platform’s ability to rollback malicious changes automatically sets it apart from traditional security solutions, providing not just detection but complete remediation capabilities.
For on-premise deployments, SentinelOne offers flexible management options that can operate independently of cloud connectivity whilst maintaining full AI capabilities. The platform’s hybrid deployment options enable organisations to maintain sensitive data on-premise whilst leveraging cloud-based threat intelligence and management capabilities. In cloud environments, SentinelOne provides native integration with containerised applications and serverless computing platforms.
The Singularity platform’s cloud workload protection capabilities extend AI powered cybersecurity solutions to modern application architectures, including Kubernetes clusters and microservices deployments. This comprehensive coverage ensures consistent protection across traditional and modern computing environments within hybrid multicloud infrastructures.
Microsoft Defender Suite
Microsoft’s Defender suite integrates AI powered cybersecurity solutions across cloud, endpoint, and identity protection scenarios. The platform leverages Microsoft’s global threat intelligence network whilst allowing organisations to maintain sensitive data processing on-premise according to regulatory requirements. This approach makes it particularly attractive for organisations already invested in Microsoft technologies who want to maintain consistency across their security stack.
Defender for Identity monitors on-premise domain controllers whilst Defender for Cloud Apps protects cloud-based applications, creating unified protection across hybrid environments. The platform’s AI capabilities analyse user behaviour patterns, authentication anomalies, and access patterns to identify potential insider threats and compromised accounts.
The integration with Azure infrastructure services enables organisations to implement comprehensive security policies across their entire Microsoft ecosystem. This tight integration proves particularly valuable for organisations managing infrastructure as code deployments where security policies need to be embedded within automated provisioning processes.
IBM QRadar with Watson
IBM’s QRadar platform enhanced with Watson AI provides cognitive security analytics capabilities that transform how security teams investigate and respond to threats. This AI powered cybersecurity solution uses natural language processing and machine learning to analyse security events and provide contextual insights that help analysts understand complex attack patterns.
QRadar’s integration with Watson AI transforms log analysis and incident investigation processes, enabling security teams to identify patterns and relationships that might otherwise remain hidden. The platform’s ability to process and correlate data from hundreds of different security tools makes it particularly valuable for large enterprises with complex security infrastructures.
The platform’s cognitive analytics capabilities enable security analysts to investigate complex threats using natural language queries and automated correlation of security events. This approach significantly reduces the time required to investigate security incidents whilst improving the accuracy of threat assessments.
Palo Alto Networks Cortex
The Cortex platform from Palo Alto Networks represents sophisticated hybrid multicloud AI powered cybersecurity solutions designed to operate across multiple cloud providers whilst maintaining unified security policies and threat correlation. Cortex XDR correlates data across networks, endpoints, and multiple cloud environments using machine learning to detect sophisticated attacks that span diverse infrastructure components.
The platform’s automated investigation and response capabilities help security teams manage threats across complex, distributed environments without requiring manual intervention for routine security events. This automation proves particularly valuable for organisations operating across multiple time zones or with limited security staff.
Cortex integrates with the broader Palo Alto Networks security ecosystem, creating comprehensive protection strategies that extend from network perimeters to individual endpoints and cloud workloads. This integration enables consistent security policies across hybrid environments.
Additional Notable Platforms
Vectra AI specialises in network detection and response across hybrid environments, using artificial intelligence to monitor network traffic patterns and identify attacker behaviours and lateral movement attempts. The platform’s ability to detect advanced persistent threats and insider threats makes it particularly valuable for organisations with complex hybrid network infrastructures.
Fortinet’s FortiAI represents the company’s commitment to integrating artificial intelligence across its security fabric architecture. This AI powered cybersecurity solution enhances threat detection capabilities whilst automating routine security operations tasks, creating comprehensive protection strategies through integration with Fortinet’s broader security ecosystem.
Arctic Wolf Cylance provides AI-powered threat prevention with its predictive AI models capable of operating completely offline whilst maintaining high detection rates. This makes it particularly effective for air-gapped environments where continuous internet connectivity isn’t available.
Trellix (formerly FireEye) offers AI-driven threat intelligence and advanced malware detection capabilities, with particular strength in identifying sophisticated attack campaigns and providing actionable threat intelligence.
AI Cybersecurity Platform Environment Compatibility
Understanding which AI powered cybersecurity solutions work optimally in specific environments is crucial for effective deployment planning. The following table provides a comprehensive overview of platform compatibility across different infrastructure configurations.
| Platform | On-Premise | Hybrid | Cloud | Hybrid Multicloud | Air-Gapped | Key Strengths |
|---|---|---|---|---|---|---|
| CrowdStrike Falcon | ✓ Limited | ✓ Excellent | ✓ Native | ✓ Excellent | ✓ Managed | Cloud-native architecture, real-time updates |
| Darktrace | ✓ Excellent | ✓ Excellent | ✓ Good | ✓ Good | ✓ Excellent | Unsupervised learning, autonomous response |
| SentinelOne | ✓ Excellent | ✓ Excellent | ✓ Excellent | ✓ Excellent | ✓ Good | Cross-platform compatibility, behavioural AI |
| Microsoft Defender | ✓ Good | ✓ Excellent | ✓ Native | ✓ Good | ✓ Limited | Azure integration, identity protection |
| Palo Alto Cortex | ✓ Good | ✓ Excellent | ✓ Excellent | ✓ Excellent | ✓ Limited | XDR capabilities, threat correlation |
| IBM QRadar Watson | ✓ Excellent | ✓ Good | ✓ Good | ✓ Good | ✓ Excellent | Cognitive analytics, on-premise strength |
| Vectra AI | ✓ Excellent | ✓ Excellent | ✓ Good | ✓ Good | ✓ Good | Network traffic analysis, APT detection |
| Fortinet FortiAI | ✓ Excellent | ✓ Excellent | ✓ Good | ✓ Good | ✓ Excellent | Integrated security fabric, OT protection |
| Cylance (Arctic Wolf) | ✓ Excellent | ✓ Good | ✓ Good | ✓ Limited | ✓ Excellent | Predictive AI, offline capability |
| FireEye (Trellix) | ✓ Excellent | ✓ Good | ✓ Good | ✓ Limited | ✓ Good | Threat intelligence, advanced malware detection |
Environment-Specific Security Technologies
On-Premise AI Security Solutions
On-premise AI powered cybersecurity solutions provide maximum control over data processing and storage, addressing regulatory requirements and latency concerns that affect many organisations. IBM QRadar with Watson offers robust on-premise deployment capabilities, processing threat intelligence locally whilst maintaining compliance with strict regulatory requirements. The platform’s cognitive analytics capabilities enable security analysts to investigate complex threats using natural language queries and automated correlation of security events.
QRadar’s integration with Watson AI transforms log analysis and incident investigation processes, enabling security teams to identify patterns and relationships that might otherwise remain hidden. The platform’s ability to process and correlate data from hundreds of different security tools makes it particularly valuable for large enterprises with complex security infrastructures.
Fortinet’s FortiAI represents another strong on-premise option, integrating artificial intelligence across the company’s security fabric architecture. This AI powered cybersecurity solution enhances threat detection capabilities whilst automating routine security operations tasks. FortiAI’s integration with Fortinet’s broader security ecosystem creates comprehensive protection strategies that extend from network perimeters to individual endpoints.
For organisations requiring air-gapped security solutions, specialised platforms like Cyber-Ark’s Privileged Access Security provide AI-driven threat detection within completely isolated networks. These solutions maintain effectiveness through machine learning models trained on historical data and behavioural analysis of user activities within secure perimeters.
Hybrid Infrastructure Protection
Microsoft’s Defender suite exemplifies effective hybrid AI powered cybersecurity solutions, seamlessly protecting on-premise Active Directory environments whilst extending coverage to Azure cloud workloads and Microsoft 365 services. The platform leverages Microsoft’s global threat intelligence network whilst allowing organisations to maintain sensitive data processing on-premise according to regulatory requirements.
Defender for Identity monitors on-premise domain controllers whilst Defender for Cloud Apps protects cloud-based applications, creating unified protection across hybrid environments. The platform’s AI capabilities analyse user behaviour patterns, authentication anomalies, and access patterns to identify potential insider threats and compromised accounts.
Symantec Enterprise Security provides similar hybrid capabilities with cloud-managed but locally-deployed protection agents. The platform’s AI engine processes telemetry from endpoints across hybrid environments whilst enabling centralised policy management and threat correlation.
Vectra AI specialises in network detection and response across hybrid environments, using artificial intelligence to monitor network traffic patterns and identify attacker behaviours and lateral movement attempts. The platform’s ability to detect advanced persistent threats (APTs) and insider threats makes it particularly valuable for organisations with complex hybrid network infrastructures that span on-premise data centres and cloud environments.
Cloud-Native AI Security
Pure cloud deployments of AI powered cybersecurity solutions offer rapid scalability, automatic updates, and reduced infrastructure overhead. Cloud Security Posture Management (CSPM) tools integrated with AI capabilities provide continuous compliance monitoring and threat detection across cloud infrastructure without requiring on-premise hardware investments.
CrowdStrike Falcon exemplifies cloud-native AI powered cybersecurity solutions, with its architecture designed specifically for cloud deployment and consumption models. The platform’s ability to process massive amounts of threat telemetry in real-time becomes a significant advantage in cloud environments where resources can scale dynamically to meet processing demands.
Cloud-native security platforms often incorporate container security capabilities, protecting modern application architectures including Docker containers and Kubernetes orchestration platforms. These AI powered cybersecurity solutions adapt to the ephemeral nature of cloud workloads whilst maintaining consistent security policies across dynamic environments.
Serverless security represents an emerging area for AI powered cybersecurity solutions, with platforms adapting to protect function-as-a-service (FaaS) and other serverless computing models. These solutions must operate within the unique constraints of serverless environments whilst providing comprehensive threat detection and response capabilities.
Hybrid Multicloud Orchestration
The Cortex platform from Palo Alto Networks represents sophisticated hybrid multicloud AI powered cybersecurity solutions, designed to operate across multiple cloud providers whilst maintaining unified security policies and threat correlation. Cortex XDR correlates data across networks, endpoints, and multiple cloud environments using machine learning to detect sophisticated attacks that span diverse infrastructure components.
Managing security across hybrid multicloud environments requires sophisticated orchestration capabilities that can adapt to different cloud providers’ APIs, security models, and operational characteristics. AI powered cybersecurity solutions must integrate with Amazon Web Services, Microsoft Azure, Google Cloud Platform, and private cloud platforms whilst maintaining consistent threat detection and response capabilities.
Cloud access security brokers (CASBs) enhanced with AI capabilities provide visibility and control across multiple cloud services and applications. These platforms use machine learning to identify unusual access patterns, data exfiltration attempts, and policy violations across diverse cloud environments.
The complexity of hybrid multicloud security requires AI powered cybersecurity solutions that can adapt to different cloud architectures, networking models, and security primitives whilst maintaining centralised management and reporting capabilities. This includes integration with cloud-native security tools provided by individual cloud vendors whilst maintaining independent threat detection and correlation capabilities.
Air-Gapped Environment Protection
Air-gapped environments present unique challenges for AI powered cybersecurity solutions, requiring periodic offline updates and local threat intelligence processing capabilities. These isolated networks, common in critical infrastructure, government facilities, and high-security research environments, cannot rely on real-time cloud-based threat intelligence or continuous security updates.
Specialised AI powered cybersecurity solutions for air-gapped environments must maintain effectiveness through machine learning models that can operate independently of external connectivity. These platforms often utilise behavioural analysis techniques that learn normal patterns within the isolated environment and identify deviations that could indicate security incidents.
Arctic Wolf Cylance represents one of the most effective AI powered cybersecurity solutions for air-gapped environments, with its AI engine capable of operating completely offline whilst maintaining high detection rates. The platform’s predictive AI models are trained on massive datasets but can function independently once deployed, providing consistent protection without requiring internet connectivity.
Update procedures for air-gapped AI powered cybersecurity solutions typically involve physical media transfers or carefully controlled network connections during maintenance windows. These updates must include not only signature updates but also enhanced AI models and algorithm improvements developed from global threat intelligence.
Industrial control systems within air-gapped environments require specialised AI powered cybersecurity solutions that understand operational technology (OT) protocols and industrial network behaviours. These platforms must distinguish between normal industrial processes and potentially malicious activities whilst avoiding disruption to critical operations.
Advanced AI Security Capabilities
Machine Learning and Behavioural Analytics
Modern AI powered cybersecurity solutions leverage multiple machine learning techniques to provide comprehensive threat detection capabilities. Supervised learning algorithms train on labelled datasets of known threats and benign activities, enabling accurate classification of new events and files. Unsupervised learning techniques identify anomalies and unusual patterns without requiring pre-defined threat signatures.
Deep learning neural networks process complex data relationships that traditional security tools might miss, including subtle patterns in network traffic, file behaviour, and user activities. These AI powered cybersecurity solutions can identify sophisticated attacks that attempt to evade detection through techniques like living-off-the-land attacks and fileless malware.
Behavioural analytics represent a critical component of modern AI powered cybersecurity solutions, establishing baselines of normal user, device, and network behaviour then identifying deviations that could indicate security incidents. These techniques prove particularly effective against insider threats and compromised accounts that might have legitimate access credentials.
Natural language processing (NLP) capabilities within AI powered cybersecurity solutions enable automated analysis of threat intelligence reports, security logs, and incident documentation. These capabilities help security teams stay current with emerging threats and automatically correlate internal security events with external threat intelligence.
Automated Response and Orchestration
AI powered cybersecurity solutions increasingly incorporate automated response capabilities that can take immediate action to contain and remediate security incidents. These capabilities range from simple isolation actions to complex orchestrated responses that coordinate multiple security tools and systems.
Security orchestration, automation, and response (SOAR) platforms enhanced with AI capabilities can automatically investigate security alerts, correlate events across multiple sources, and execute response playbooks without human intervention. These AI powered cybersecurity solutions significantly reduce mean time to response (MTTR) whilst ensuring consistent incident handling procedures.
Machine learning algorithms continuously improve automated response capabilities by learning from previous incidents and their outcomes. This enables AI powered cybersecurity solutions to adapt their response strategies based on effectiveness and environmental characteristics.
The integration of AI powered cybersecurity solutions with identity and access management systems enables automated responses that can modify user permissions, terminate suspicious sessions, and implement additional authentication requirements based on risk assessments.
Deployment Considerations by Environment
Infrastructure Requirements and Scalability
Each deployment model for AI powered cybersecurity solutions presents distinct infrastructure requirements and scalability considerations. On-premise deployments require substantial hardware investments including high-performance computing resources for AI model processing, extensive storage for log retention, and ongoing maintenance capabilities.
The computational requirements for AI powered cybersecurity solutions continue to increase as machine learning models become more sophisticated and datasets grow larger. Graphics processing units (GPUs) and specialised AI processors can significantly accelerate threat detection and analysis capabilities, particularly for deep learning applications.
Hybrid configurations demand careful orchestration between local and cloud components to maintain security consistency whilst optimising performance and cost. Network connectivity between on-premise and cloud components must be secured and monitored to prevent attacks that could compromise the hybrid architecture.
Cloud deployments offer the advantage of immediate scalability and reduced infrastructure overhead, making AI powered cybersecurity solutions accessible to organisations of all sizes. Cloud platforms provide elastic computing resources that can automatically scale to handle increased security telemetry during incidents or peak activity periods.
Hybrid multicloud environments require sophisticated management tools to maintain visibility and control across multiple cloud providers whilst ensuring consistent security policies. AI powered cybersecurity solutions must adapt to different cloud architectures and APIs whilst maintaining unified threat correlation and response capabilities.
Air-gapped environments present the greatest implementation challenges for AI powered cybersecurity solutions, requiring periodic manual updates and local processing capabilities. However, these deployments provide the highest level of security for critical infrastructure and classified information systems.
Integration and Interoperability
Successful deployment of AI powered cybersecurity solutions requires careful consideration of integration capabilities with existing security infrastructure. Application programming interfaces (APIs) enable automated data sharing and coordinated responses between different security tools and platforms.
Security information and event management (SIEM) systems often serve as central integration points for AI powered cybersecurity solutions, aggregating telemetry from multiple sources and enabling cross-platform correlation and analysis. Modern SIEM platforms incorporate AI capabilities themselves whilst supporting integration with specialised AI security tools.
Identity and access management (IAM) integration enables AI powered cybersecurity solutions to understand user contexts, access patterns, and privilege levels when evaluating security events. This integration proves particularly important for detecting insider threats and compromised account activities.
Network security tool integration allows AI powered cybersecurity solutions to correlate endpoint activities with network traffic patterns, providing comprehensive visibility across the entire attack surface. This integration proves particularly valuable for detecting lateral movement and command-and-control communications.
Benefits of Multi-Environment AI Security
AI powered cybersecurity solutions have transformed how we think about digital protection, moving away from traditional reactive approaches towards proactive, intelligent systems that can adapt and learn. These platforms process enormous amounts of data every second, identifying subtle patterns that might indicate emerging threats. The beauty of modern AI security lies in its ability to understand context – it doesn’t just look for known bad things, but understands what normal looks like and spots when something doesn’t fit.
What makes these systems particularly powerful is their ability to work across different environments without losing effectiveness. Whether you’re running everything in your own data centre, spreading workloads across multiple clouds, or operating in highly secure air-gapped environments, modern AI powered cybersecurity solutions can adapt to your specific situation.
The automated response capabilities we see in today’s platforms represent a significant leap forward. Instead of simply alerting security teams to potential threats, these systems can take immediate action to contain incidents whilst they’re still developing. This speed makes all the difference when you consider that many successful attacks happen within minutes or even seconds.
The learning aspect of these systems continues to impress security professionals. Machine learning algorithms get better over time by analysing new attack patterns, understanding which alerts were false positives, and adapting to changes in the environment. This means your security actually improves the longer these systems run, creating a positive feedback loop that benefits everyone.
Having the flexibility to deploy AI powered cybersecurity solutions across various environments means organisations can maintain consistent security standards regardless of where their data and applications live. This consistency becomes particularly valuable for organisations operating across multiple geographic regions with different regulatory requirements, or those going through digital transformation initiatives that involve moving workloads between different platforms.
From a cost perspective, modern AI powered cybersecurity solutions offer compelling advantages. Cloud-based models eliminate the need for substantial infrastructure investments whilst still providing enterprise-grade security capabilities. The scalability these platforms offer means organisations can adjust their security spending based on actual usage and threat levels, rather than having to over-provision for peak scenarios.
Future of Multi-Environment AI Security
Looking ahead, the cybersecurity industry continues evolving at a rapid pace, with AI powered cybersecurity solutions becoming increasingly sophisticated across all deployment models. We’re seeing exciting developments in areas like quantum computing and advanced neural networks that will further enhance threat detection and response capabilities, regardless of how organisations choose to deploy their infrastructure.
Edge computing integration represents a particularly interesting development, enabling AI powered cybersecurity solutions to provide real-time protection in hybrid and distributed environments. This means processing security telemetry closer to where it’s generated, reducing latency for critical response actions. This capability proves especially important for industrial environments and Internet of Things deployments where immediate response times can make the difference between minor incidents and major operational disruptions.
The evolution towards better coordination between different security systems looks promising too. Advanced federation capabilities will improve how on-premise, cloud, and air-gapped security systems work together, enabling better threat intelligence sharing whilst maintaining appropriate security boundaries. These developments will help AI powered cybersecurity solutions benefit from global threat intelligence whilst respecting data sovereignty and security requirements.
Zero-trust architecture integration represents another significant trend, with platforms adapting to assume no implicit trust and continuously validate access requests based on multiple factors including user behaviour, device posture, and environmental context. This approach aligns perfectly with how AI systems naturally work – continuously assessing and reassessing rather than making one-time decisions.
The artificial intelligence and machine learning capabilities themselves continue advancing, with new techniques like federated learning enabling AI powered cybersecurity solutions to improve their capabilities without centralising sensitive training data. This approach proves particularly valuable for organisations operating in regulated industries or air-gapped environments where data can’t leave the local environment.
For organisations thinking about their security strategy, investing in flexible AI-driven security platforms today positions them well for future cyber challenges across evolving infrastructure landscapes. The ability to seamlessly adapt AI powered cybersecurity solutions across different deployment models will become increasingly critical as organisations continue diversifying their infrastructure strategies and adopting new technologies.
AI powered cybersecurity solutions represent the future of digital protection across all environment types, offering unprecedented capabilities to protect against sophisticated cyber threats whilst adapting to diverse operational requirements. As these platforms continue maturing, they’re becoming essential components of comprehensive cybersecurity strategies for organisations operating in on-premise, hybrid, cloud, hybrid multicloud, and air-gapped environments. The key is choosing solutions that can grow and adapt with your organisation rather than locking you into specific approaches or technologies.