Metasploit was created by H. D. Moore in 2003 as a portable network tool using Perl. By 2007, the Metasploit Framework had been completely rewritten in Ruby.  On October 21, 2009, the Metasploit Project announced that it had been acquired by Rapid7, a security company that provides unified vulnerability management solutions. Metasploit’s emerging position as the de facto exploit development framework led to the release of software vulnerability advisories often accompanied by a third party Metasploit exploit module that highlights the exploitability, risk and remediation of that particular bug. Metasploit 3.0 began to include fuzzing tools, used to discover software vulnerabilities, rather than just exploits for known bugs. This avenue can be seen with the integration of the lorcon wireless (802.11) toolset into Metasploit 3.0 in November 2006. Metasploit 4.0 was released in August 2011. In this guide we will look into the most important part of using Metasploit, how to search exploits within it! Yeah, like it or not, if you can’t search, then you got nada!
On October 21, 2009, the Metasploit Project announced that it had been acquired by Rapid7, a security company that provides unified vulnerability management solutions. Metasploit’s emerging position as the de facto exploit development framework led to the release of software vulnerability advisories often accompanied by a third party Metasploit exploit module that highlights the exploitability, risk and remediation of that particular bug. Metasploit 3.0 began to include fuzzing tools, used to discover software vulnerabilities, rather than just exploits for known bugs. This avenue can be seen with the integration of the lorcon wireless (802.11) toolset into Metasploit 3.0 in November 2006. Metasploit 4.0 was released in August 2011. In this guide we will look into the most important part of using Metasploit, how to search exploits within it! Yeah, like it or not, if you can’t search, then you got nada!
searchsploit
How many of you used searchsploit in Kali Linux? It’s a nice tool that updates and downloads exploits often. I use it quite extensively along with MetaSploit.
Use searchsploit to search specific exploits. You can use it like this:
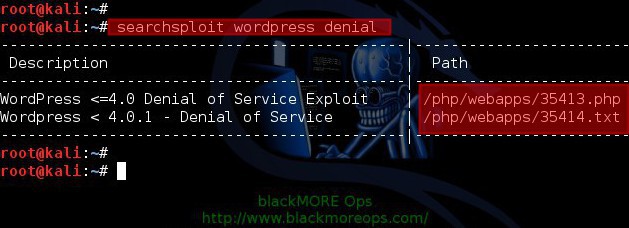
root@kali:~# searchsploit wordpress denial
---------------------------------------------|----------------------------------
Description | Path
---------------------------------------------|----------------------------------
WordPress <=4.0 Denial of Service Exploit | /php/webapps/35413.php
Wordpress < 4.0.1 - Denial of Service | /php/webapps/35414.txt
---------------------------------------------|----------------------------------
root@kali:~# Just in case you want to search something else, you -h and it shows the help menu. Now help yourself to find more vulnerabilities.
[toggle title=”searchsploit Help Menu – Click to expand” state=”close”]
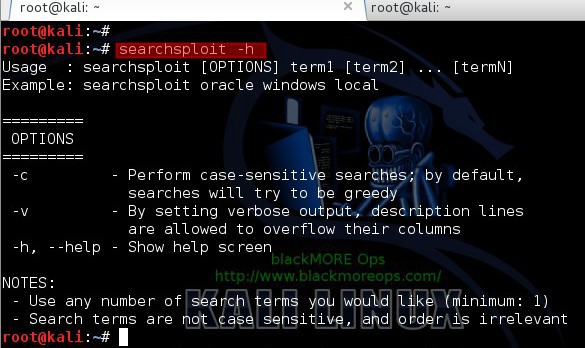
root@kali:~# searchsploit -h
Usage : searchsploit [OPTIONS] term1 [term2] ... [termN]
Example: searchsploit oracle windows local
=========
OPTIONS
=========
-c - Perform case-sensitive searches; by default,
searches will try to be greedy
-v - By setting verbose output, description lines
are allowed to overflow their columns
-h, --help - Show help screen
NOTES:
- Use any number of search terms you would like (minimum: 1)
- Search terms are not case sensitive, and order is irrelevant
root@kali:~# [/toggle]
Pretty easy way to search exploits actually if you don’t want to learn metasploit search options. Do share if you think it helped.


1 comment
Thanks . That was very helpful .