Cybersecurity researchers have uncovered a concerning development where Türkiye-affiliated hackers successfully exploited a Zero-Day Vulnerability in Output Messenger. The attack, which began in April 2024, specifically targeted Kurdish military operations in Iraq. This Zero-Day Vulnerability in Output Messenger highlights the ongoing cybersecurity challenges faced by organisations using enterprise communication tools and underscores the sophisticated nature of state-affiliated threat actors in the cyber espionage landscape.
Table of Contents
The Attack Details
Microsoft Threat Intelligence has attributed this attack to a threat group they track as Marbled Dust (formerly known as Silicon). This group operates under various aliases including Cosmic Wolf, Sea Turtle, Teal Kurma, and UNC1326. According to Microsoft’s analysis, Marbled Dust has been active since at least 2017, with documented attacks targeting both public and private entities throughout the Middle East and North Africa.
The vulnerability exploited in this attack has been identified as CVE-2025-27920, a directory traversal vulnerability affecting Output Messenger version 2.0.62. This security flaw allowed remote attackers to access or execute arbitrary files on targeted systems. Srimax, the developer of Output Messenger, addressed this vulnerability in late December 2024 with the release of version 2.0.63, though their advisory notably omitted mention of the vulnerability being actively exploited in the wild.
Sophisticated Attack Chain
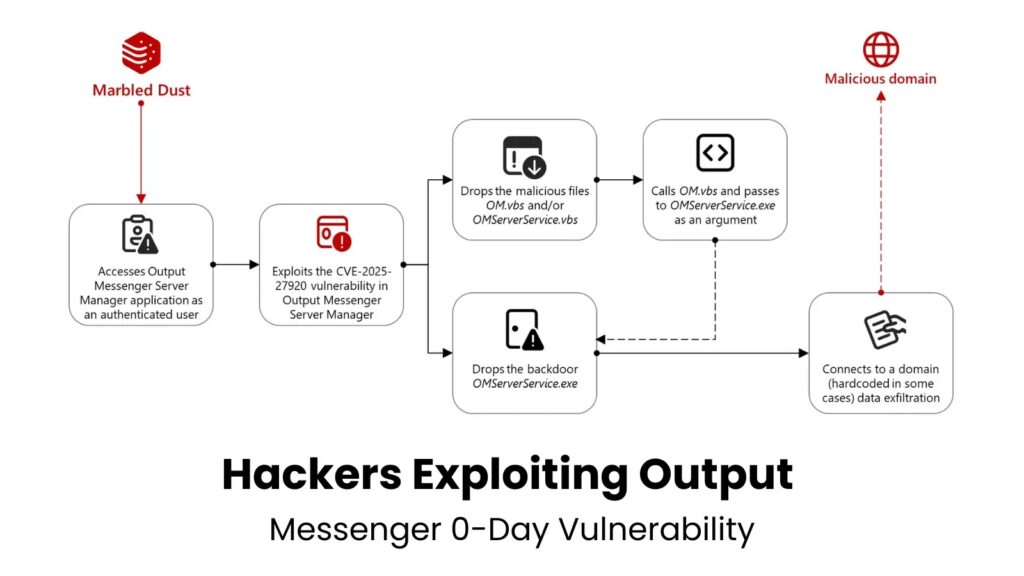
The attack methodology employed by Marbled Dust demonstrates their technical sophistication and targeted approach. The attack chain begins with the threat actor gaining authenticated access to the Output Messenger Server Manager application. Microsoft believes that Marbled Dust likely employs techniques such as DNS hijacking or typosquatted domains to intercept authentication credentials.
Upon gaining access, the attackers collect the user’s Output Messenger credentials and exploit the zero-day vulnerability to deploy malicious payloads. These include script files named “OM.vbs” and “OMServerService.vbs” which are placed in the server startup folder, along with an executable file “OMServerService.exe” deployed to the server’s “Users/public/videos” directory.
In the subsequent phase of the attack, “OMServerService.vbs” is used to invoke both “OM.vbs” and “OMServerService.exe”. The latter is a Golang backdoor programmed to contact a hard-coded domain (“api.wordinfos[.]com”) for the purpose of data exfiltration.
Client-Side Compromise
The attack isn’t limited to server components. On the client side, the compromised installer extracts and executes both the legitimate “OutputMessenger.exe” file and a malicious “OMClientService.exe”, which is another Golang backdoor that connects to the same command-and-control (C2) domain used by Marbled Dust.
This client-side backdoor performs an initial connectivity check via a GET request to the C2 domain. Upon successful connection, a second GET request containing hostname information is sent to uniquely identify the victim. The response from the C2 server is then directly executed using the Windows command prompt with the “cmd /c” instruction, allowing the attackers to run specific commands and then terminate the session.
Microsoft reports identifying at least one instance where a victim device with the Output Messenger client software installed connected to an IP address previously linked to Marbled Dust, likely for data exfiltration purposes.
Additional Vulnerabilities
During their investigation, Microsoft discovered a second vulnerability in the same version of Output Messenger – a reflected cross-site scripting (XSS) vulnerability catalogued as CVE-2025-27921. However, Microsoft found no evidence of this additional vulnerability being weaponised in real-world attacks.
December 25, 2024 V2.0.63
- (CVE-2025-27921) XSS vulnerability issues.
- (CVE-2025-27920) Directory traversal attack.
Strategic Implications
Microsoft’s threat assessment suggests this new attack represents “a notable shift in Marbled Dust’s capability while maintaining consistency in their overall approach.” The successful exploitation of a zero-day vulnerability indicates an increase in the group’s technical sophistication and may suggest either an escalation in their targeting priorities or greater urgency in their operational goals.
This development aligns with Marbled Dust’s previously observed targeting patterns. Early last year, the group was identified targeting telecommunication companies, media organisations, internet service providers (ISPs), IT service providers, and Kurdish websites in the Netherlands.
Conclusion
The exploitation of the Output Messenger zero-day vulnerability by Türkiye-affiliated hackers represents a significant cybersecurity incident with implications for organisations using enterprise communication platforms. This zero-day attack demonstrates the sophisticated capabilities of state-affiliated threat actors and their persistent focus on specific geopolitical targets.
Organisations using Output Messenger should immediately update to version 2.0.63 or later to protect against this vulnerability. More broadly, this incident serves as a reminder of the critical importance of maintaining up-to-date security patches across all communication platforms and implementing robust security measures to detect and mitigate sophisticated cyber espionage attempts.